In today’s digital age, cloud computing has become an essential component of the modern business landscape. With the convenience and flexibility that it offers, more and more organizations are adopting cloud solutions to store and process their sensitive data. However, as the use of cloud environments grows, so does the risk of cyber attacks and data breaches. Therefore, securing sensitive data in cloud environments has become a crucial concern for businesses across all industries.
To protect sensitive data in the cloud, companies must understand the unique security challenges that come with cloud computing. Unlike traditional on-premise solutions, cloud environments are accessible from anywhere in the world, making them a popular target for cybercriminals. In this article, we will explore the best practices that businesses can implement to secure their sensitive data in the cloud. From data encryption to access controls, we will provide practical guidance that can help you mitigate the risks and keep your information safe.
Secure Sensitive Data in Cloud Environments
- Step 1: Research and select the cloud provider that best meets your security needs.
- Step 2: Establish a secure connection between the provider and your existing system.
- Step 3: Identify and classify all the sensitive data that needs to be secured.
- Step 4: Utilize encryption methods to protect the data.
- Step 5: Implement access control policies to regulate access to the data.
- Step 6: Monitor and audit the system regularly to detect any potential threats.
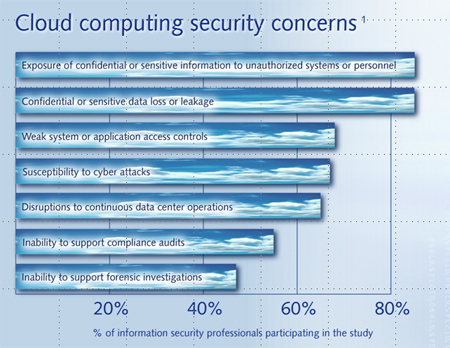
How to Secure Sensitive Data in Cloud Environments?
Data security is a major concern when it comes to cloud computing. It is important to understand how to secure sensitive data in cloud environments to ensure that the data is kept safe and secure. This article will outline the various steps that can be taken to protect sensitive data in the cloud.
Encryption of Data
Encryption is a key component of protecting data in the cloud. It is important to ensure that data is encrypted when it is stored in the cloud. This will ensure that any sensitive data is unreadable by anyone who does not have the encryption key. It is also important to ensure that the encryption keys are stored securely and not accessible by anyone who does not have the appropriate permissions.
Encryption can be applied to data in transit, such as when it is being transferred from one cloud infrastructure to another, as well as to data when it is stored in the cloud. This will ensure that the data is kept secure and is not vulnerable to any malicious actors.
Access Control and Authentication
It is important to ensure that access to sensitive data is restricted to only those who have the appropriate permissions. This can be done through the use of access control and authentication. Access control is a system that is used to determine who has access to which data and what they are allowed to do with it. Authentication is the process of verifying that a user is who they claim to be.
By using access control and authentication, it is possible to ensure that only those with the appropriate permissions can access sensitive data in the cloud. This will help to protect the data and keep it secure.
Auditing and Logging
Auditing and logging are important components of cloud security. Auditing is the process of examining the security of a system to ensure that it is meeting the desired security requirements. Logging is the process of recording any activities that occur on the system, such as when a user accesses sensitive data.
By regularly auditing and logging, it is possible to identify any potential security vulnerabilities or suspicious activities. This will help to ensure that the data is kept secure and any malicious actors are identified and dealt with appropriately.
Secure Protocols
It is important to ensure that secure protocols are used when transferring data in the cloud. This includes using secure protocols such as TLS, HTTPS, and SFTP. These protocols will help to ensure that any data that is transferred is kept secure and is not vulnerable to any malicious actors.
It is also important to ensure that secure protocols are used when accessing data in the cloud. This includes using secure protocols such as SSH and SFTP. These protocols will help to ensure that any data that is accessed is kept secure and is not vulnerable to any malicious actors.
Data Backup
Data backup is an important component of protecting data in the cloud. Data backups should be done regularly and stored securely in order to ensure that any data that is lost can be easily recovered. This will help to ensure that any sensitive data is kept safe and secure in the event of any data loss.
It is also important to ensure that the data backups are regularly tested to ensure that they are working properly. This will help to ensure that any data that is backed up is kept secure and can be easily recovered if needed.
Data Governance
Data governance is an important component of protecting data in the cloud. Data governance is the process of defining and enforcing policies and procedures around how data is used in the cloud. This includes policies around access control and authentication, auditing and logging, and secure protocols.
By enforcing data governance policies, it is possible to ensure that data is kept secure and is not vulnerable to any malicious actors. It is also important to ensure that data governance policies are regularly reviewed and updated to ensure that they are up to date and are still relevant in the ever-changing cloud environment.
Frequently Asked Questions
Securing sensitive data in the cloud is one of the most important tasks for organizations to undertake. With the increasing use of cloud computing, organizations must be aware of the security risks involved and work to mitigate them in order to protect their data. In this article, we will answer five frequently asked questions about how to secure sensitive data in cloud environments.
What Is the Best Way to Secure Sensitive Data in the Cloud?
The best way to secure sensitive data in the cloud is to use a combination of measures. This includes using encryption, implementing access control policies, and employing other security measures such as two-factor authentication and multifactor authentication. Additionally, organizations should also have their cloud-based systems maintained and monitored regularly to ensure the security of their data.
How Can Organizations Ensure That Their Cloud Data Is Secure?
Organizations can ensure that their cloud data is secure by taking a few critical steps. First, they should make sure that the cloud provider they are using is compliant with relevant security standards, such as ISO 27001. Additionally, they should also have their data encrypted and access control policies in place to restrict access to the data. Finally, organizations should also ensure that their cloud-based systems are regularly monitored and maintained.
What Are the Benefits of Implementing Access Control Policies in Cloud Environments?
Implementing access control policies in cloud environments can help to ensure the security of sensitive data. Access control policies allow organizations to control who can access their data and what they can do with it. This helps to ensure that only authorized users are able to access the data, reducing the risk of unauthorized access. Additionally, access control policies also allow organizations to set up different levels of access, so that only users who need to have access to certain data can view it.
What Are the Risks of Storing Sensitive Data in the Cloud?
One of the main risks of storing sensitive data in the cloud is the potential for unauthorized access. This can be due to hackers or malicious actors gaining access to the data, or due to a user with access to the data misusing it. Additionally, if the cloud provider does not have adequate security measures in place, this can also increase the risk of a data breach.
What Are Some Best Practices for Securing Sensitive Data in the Cloud?
There are several best practices organizations can follow to ensure the security of their sensitive data in the cloud. First, they should ensure that their data is encrypted and access control policies are in place. Additionally, organizations should also employ two-factor authentication and multifactor authentication for added security. Finally, organizations should make sure that their cloud-based systems are regularly monitored and maintained to ensure the security of their data.

In conclusion, securing sensitive data in cloud environments is a critical task that requires careful planning and implementation. The key is to adopt a multi-layered security approach that encompasses all aspects of the cloud infrastructure, including the network, application, and data layers. This involves implementing robust authentication and authorization mechanisms, encrypting data at rest and in transit, and monitoring the cloud environment for potential threats and vulnerabilities.
As more organizations move their data to the cloud, the need to secure sensitive information becomes increasingly important. By following the best practices outlined in this article, organizations can ensure that their sensitive data is protected from unauthorized access, theft, and other malicious activities. As the cloud continues to evolve, it is essential to stay abreast of the latest security trends and technologies to keep data safe and secure in a cloud environment. Ultimately, data security is a shared responsibility between cloud providers and their customers, and both parties must work together to ensure that sensitive data is safeguarded at all times.



