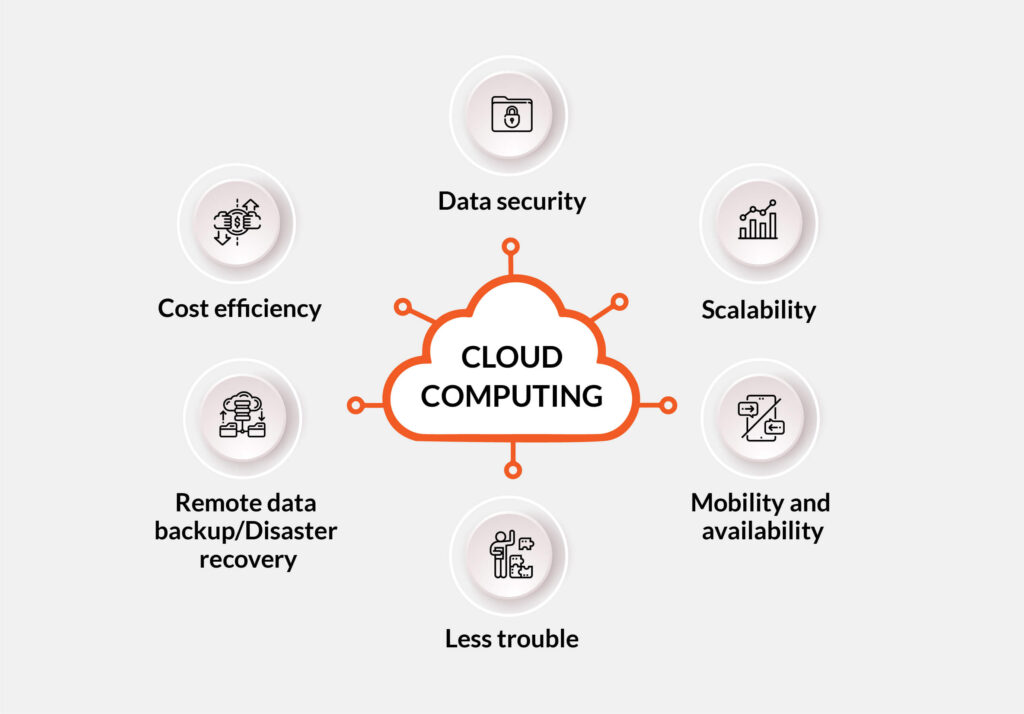
Cloud computing has revolutionized the way businesses operate in today’s digital era. It offers an array of benefits that include reduced costs, scalability, and flexibility. But, before you start using cloud services, it is important to understand the different account attributes that come with it. These attributes are essential to ensure that your cloud service is secure, reliable, and meets your specific business needs.
Cloud service account attributes are the characteristics that define your cloud environment. They include everything from access controls, resource allocation, and network security policies to data backup and recovery options. Understanding these attributes is crucial, as they determine how you will interact with the cloud service and what level of security and access control you will have. In this article, we will explore the different cloud service account attributes that you need to know to make informed decisions when choosing a cloud service provider.
- Identity: A service account is associated with a single Google identity. It is used to authenticate the service account.
- Permissions: Permissions control what a service account can do, like access Google APIs or manage resources.
- Groups: Service accounts can be added to Google Groups to control access to resources.
- IAM Policies: Policies are used to control access to resources, like Cloud Storage buckets.
- Key Management: Service accounts can have cryptographic keys associated with them, used to authenticate applications.
- Audit Logging: All requests to a service account are logged and monitored to help protect against security threats.

What Are Cloud Service Account Attributes?
Cloud service accounts are user accounts that grant access to cloud-based services and applications. These accounts are essential for managing user access to cloud-based services, ensuring that users are able to securely access and manage data in the cloud. Cloud service accounts offer a range of attributes including authentication, authorization, and accountability.
Authentication
Authentication is the process of verifying user identity when accessing cloud-based services. This process is important for ensuring that only authorized users can access and manage data in the cloud. Cloud service accounts offer authentication features such as two-factor authentication and biometric authentication. Two-factor authentication requires users to enter a username and password as well as an additional form of identification such as a one-time code sent via SMS. Biometric authentication involves using biometric data such as fingerprints or facial recognition to verify the user’s identity.
The authentication process also includes the use of encryption to protect data from being accessed by unauthorized users. Encryption ensures that only authorized users can access sensitive information and prevents data from being accessed by malicious actors.
Authorization
Authorization is the process of granting users access to specific cloud-based services and applications. Cloud service accounts offer authorization features such as role-based access control and access control lists. Role-based access control involves assigning users with specific roles and permissions based on their job functions. Access control lists allow organizations to specify which users have access to specific cloud-based services and applications.
The authorization process also includes the use of authorization tokens which are used to identify and authenticate users when accessing cloud-based services. Authorization tokens also allow organizations to track user activity and ensure that only authorized users have access to sensitive data.
Accountability
Accountability is the process of tracking user activity and ensuring that users are compliant with security policies. Cloud service accounts offer accountability features such as audit logs and activity reports. Audit logs record user activity such as login attempts, data access, and changes to security settings. Activity reports provide an overview of user activity and can be used to detect any suspicious activity.
The accountability process also includes the use of security policies which define how users should access and use cloud-based services. Security policies help ensure that users are compliant with security standards and reduce the risk of unauthorized access to sensitive data.
Frequently Asked Questions About Cloud Service Account Attributes
The cloud service account attribute is the set of requirements, rules and conditions a cloud service provider enforces to ensure customer data is secure and protected. Understanding the attributes of a cloud service account can help you make the best decision when choosing a cloud provider.
What Are the Key Attributes of a Cloud Service Account?
The key attributes of a cloud service account include access control, authentication and authorization, encryption, and auditing. Access control is the ability to control who can access data and resources in a cloud environment. Authentication and authorization is the process of verifying the identity of a user or device and granting access to the cloud resources they are allowed to access. Encryption is the process of encoding data to make it unreadable to anyone without the encryption key. Auditing is the process of tracking and logging access to data and cloud resources to ensure compliance with security policies.
What Are the Benefits of Cloud Service Account Attributes?
The benefits of cloud service account attributes are improved security and data protection. Access control ensures that only authorized users and devices can access data and resources. Authentication and authorization verifies that the user or device has the necessary credentials to access the cloud resources. Encryption ensures that only authorized users have access to the data in its readable form. Auditing helps to ensure that access to cloud resources is compliant with security policies.
What Are the Different Types of Cloud Service Account Attributes?
There are several different types of cloud service account attributes. These include access control, authentication and authorization, encryption, and auditing. Access control is the ability to control who can access data and resources in a cloud environment. Authentication and authorization is the process of verifying the identity of a user or device and granting access to the cloud resources they are allowed to access. Encryption is the process of encoding data to make it unreadable to anyone without the encryption key. Auditing is the process of tracking and logging access to data and cloud resources to ensure compliance with security policies.
How Can I Ensure That the Cloud Service Account Attributes are Secure?
To ensure that the cloud service account attributes are secure, it is important to follow best practices for access control, authentication and authorization, encryption, and auditing. Access control should be used to restrict access to only those users and devices that have been authorized. Authentication and authorization should be used to verify the identity of users and devices and to grant access to the resources they are allowed to access. Encryption should be used to protect data in transit and at rest. Auditing should be used to track and log access to cloud resources to ensure compliance with security policies.
What Are the Best Practices for Managing Cloud Service Account Attributes?
The best practices for managing cloud service account attributes include implementing strong access control measures, ensuring authentication and authorization protocols are secure, encrypting data both in transit and at rest, and regularly auditing access to cloud resources. Access control measures should restrict access to only authorized users and devices. Authentication and authorization protocols should ensure that only those users and devices with the necessary credentials can access the cloud resources. Data should be encrypted both in transit and at rest to ensure that only authorized users have access to the data in its readable form. Auditing should be regularly performed to ensure that access to cloud resources is compliant with security policies.

In conclusion, understanding the different attributes of cloud service accounts is essential for businesses and individuals who want to leverage the benefits of cloud computing. These attributes, including scalability, availability, reliability, security, and cost-effectiveness, are critical factors to consider when selecting a cloud service provider. By evaluating each of these attributes carefully and choosing a provider that meets their specific needs, users can ensure that they are getting the best value for their investment.
With the increasing popularity of cloud computing, it is becoming more important than ever to be aware of the different attributes of cloud service accounts. As technology continues to evolve, it is likely that new attributes will emerge, and existing ones may change. Businesses and individuals who stay up-to-date with these changes will be better equipped to take advantage of the benefits of cloud computing and stay ahead of the competition. Therefore, it is crucial for anyone interested in cloud computing to continue learning about these essential attributes and how they can impact their business or personal use of cloud services.