Wireless networks have become an integral part of our daily lives. From homes to offices and public spaces, we rely on wireless networks to stay connected and productive. However, this convenience comes with a price: the security of wireless networks is often compromised, leaving valuable data and personal information vulnerable to cyber attacks. As such, it is crucial to understand the characteristics of wireless network security to ensure the safety of our devices and information.
One important aspect of wireless network security is encryption. Encryption is the process of encoding information in a way that only authorized parties can access it. In wireless networks, encryption is used to protect the data that is being transmitted between devices. Two common encryption protocols used in wireless networks are Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA). While WEP is an older and less secure protocol, WPA provides stronger encryption and is widely used in modern wireless networks. Therefore, the first characteristic of wireless network security is the use of encryption protocols such as WPA to protect the data transmitted over the network.

Wireless Network Security Characteristics
Wireless network security is an important factor to consider when setting up any kind of network. It is important to ensure that the data transmitted over the network is secure and cannot be accessed by unauthorized individuals. There are two main statements that characterize wireless network security: encryption and authentication. In this article, we will discuss what these two statements mean and how they can help protect your network.
Encryption
Encryption is the process of scrambling data so that it is unreadable to anyone without the proper decryption key. This is done to ensure that even if someone were to gain access to the data, they would not be able to decipher it. Wireless networks use a variety of encryption algorithms to secure data transmissions. The most common type of encryption used is called WEP (Wired Equivalent Privacy). WEP uses a 64-bit or 128-bit key to encrypt data as it is sent over the airwaves.
In addition to WEP, there are several other types of encryption algorithms used to secure wireless networks. These include WPA (Wi-Fi Protected Access), WPA2 (Wi-Fi Protected Access II), and TKIP (Temporal Key Integrity Protocol). Each of these encryption algorithms has its own set of features and benefits, so it is important to research each one before selecting the right one for your network.
Authentication
Authentication is the process of verifying the identity of a user or device before allowing access to the network. There are several methods of authentication commonly used in wireless networks. These include MAC (Media Access Control) address filtering, RADIUS (Remote Authentication Dial-In User Service) server authentication, and 802.1X (Extensible Authentication Protocol).
MAC address filtering is a simple and cost-effective way of authentication. It uses the MAC address of a device to determine if it should be allowed to access the network. The advantage of MAC address filtering is that it is easy to implement and does not require any additional hardware or software. However, it is not secure since the MAC address of a device can easily be changed.
RADIUS server authentication is more secure than MAC address filtering but is more complex to implement. It requires an authentication server, such as a RADIUS server, to verify the identity of a user or device. The advantage of RADIUS server authentication is that it is secure and can be used to enforce access policies.
802.1X is a protocol that is used to authenticate users and devices on a wireless network. It uses a variety of different methods, including passwords and certificates, to verify the identity of a user or device before allowing access to the network. The advantage of 802.1X is that it is secure and can be used to enforce access policies.
Conclusion
In conclusion, wireless network security can be ensured by using encryption and authentication. Encryption is used to scramble data so that it is unreadable to anyone without the proper decryption key. Authentication is the process of verifying the identity of a user or device before allowing access to the network. There are several methods of authentication commonly used in wireless networks, including MAC address filtering, RADIUS server authentication, and 802.1X. It is important to research each method before selecting the right one for your network.
Frequently Asked Questions About Wireless Network Security
Wireless network security is a critical component of network security. It is important to understand how wireless networks operate, the security risks associated with them, and the best practices that can be used to protect them.
What Are the Security Risks Associated With Wireless Networks?
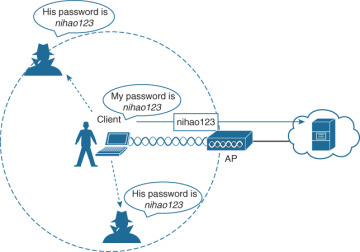
Wireless networks are vulnerable to a variety of security risks, including unauthorised access, data interception, and malicious attacks. Unauthorised access occurs when an unauthorised user gains access to the network without permission. Data interception occurs when someone intercepts data as it is being transmitted across the network. Malicious attacks occur when malicious actors exploit weaknesses in the network to gain access or disrupt its operation.
The security risks associated with wireless networks can be addressed through the use of authentication and encryption technologies. Authentication requires users to prove their identity before being granted access to the network. Encryption technologies scramble data as it is transmitted across the network, making it unreadable to anyone attempting to intercept it.
How Can I Prevent Unauthorised Access to My Wireless Network?
The most effective way to prevent unauthorised access to your wireless network is to use wireless encryption. Wireless encryption scrambles the data as it is transmitted across the network, making it unreadable to anyone trying to intercept it. It also requires users to prove their identity before being granted access to the network. Additionally, using a strong password or passphrase can help prevent unauthorised access.
Another way to prevent unauthorised access is to use a firewall to control access to the network. A firewall will limit access to the network to authorised users and can be configured to block unauthorised devices from connecting.
What Are the Best Practices for Securing a Wireless Network?
The best practices for securing a wireless network include enabling wireless encryption, using a strong password or passphrase, and enabling a firewall to control access to the network. Additionally, it is important to regularly update the firmware on your wireless router to ensure it is running the latest security patches.
It is also important to monitor your network for any suspicious activity. Regularly scanning your network for unauthorised devices, monitoring for suspicious traffic, and logging user activity can help detect potential security threats.
What Is a Wireless Access Point?
A wireless access point (WAP) is a device that allows wireless devices to connect to a wired network. A WAP typically consists of a radio transceiver, an antenna, and a network connection. WAPs are used to extend the range of a wireless network and provide users with access to the network from outside of the range of the main network.
When configuring a WAP, it is important to use a secure encryption protocol and a strong password or passphrase. Additionally, it is important to configure the WAP to use the least powerful signal that is necessary, as this will reduce the range of the signal and make it harder for unauthorised users to gain access.
What Is a Wireless Router?
A wireless router is a device that connects a wired network to a wireless network. It typically consists of a radio transceiver, an antenna, and a network connection. A wireless router is used to allow wireless devices to connect to a wired network and access the internet.
When configuring a wireless router, it is important to use a secure encryption protocol and a strong password or passphrase. Additionally, it is important to disable any unnecessary services or features that could be exploited by malicious actors. Additionally, it is important to regularly update the firmware on your router to ensure it is running the latest security patches.
In conclusion, ensuring the security of wireless networks is crucial in today’s digital age. Two statements that can characterize wireless network security are the need for strong encryption protocols and the importance of regular network monitoring. Implementing robust encryption techniques such as WPA2 or WPA3 can significantly reduce the risk of unauthorized access to the network. Additionally, regular monitoring of network traffic can help detect suspicious activities and prevent potential security breaches.
As technology continues to advance, so do the methods used by cybercriminals to exploit vulnerabilities in wireless networks. Therefore, it is essential to stay up-to-date with the latest security protocols and best practices. By implementing strong encryption techniques and regularly monitoring network traffic, organizations can significantly reduce the risk of cyber attacks and protect their sensitive data. Ultimately, wireless network security is not a one-time investment, but an ongoing process that requires continuous attention and improvement.


Appreciate it for helping out, excellent info. “You must do the things you think you cannot do.” by Eleanor Roosevelt.
This is a topic close to my heart cheers, where are your contact details though?