Wireless networks have become an integral part of modern communication systems. With the increased use of mobile devices and the internet of things, more and more devices rely on wireless networks to communicate with each other. However, with these advancements come security concerns. Wireless networks are vulnerable to various threats, including attacks from hackers and unauthorized access. Therefore, it is essential to understand the characteristics of wireless network security to ensure the safety of the network and the devices connected to it.
One of the critical aspects of wireless network security is understanding what it entails. Wireless network security involves protecting the network and the devices connected to it from unauthorized access, misuse, modification, or theft. It involves implementing security measures such as authentication, encryption, and access control to safeguard the network and the data being transmitted. In this article, we will explore two statements that characterize wireless network security and their importance in ensuring the safety and security of wireless networks.
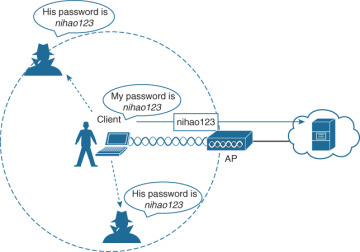
Wireless network security is best achieved through using encryption and authentication protocols. Encryption scrambles data passing through the network, making it unreadable to anyone but the intended recipient. Authentication verifies the identity of the users attempting to access the network.
Encryption can be done with WEP, WPA or WPA2 protocols. WPA2 is the most secure, while WEP is the least secure. Authentication is done with a username and password, or with a certificate-based system.
Which two statements characterize wireless network security?
Wireless network security is an important consideration for any organization or individual using a wireless network. Wireless security must be taken seriously in order to protect a network from malicious actors. In this article, we will discuss two statements that characterize wireless network security.
1. Authentication
Authentication is the process of verifying a user’s identity before allowing them access to a network. A variety of authentication methods are available, such as passwords, biometrics, or tokens. It is important to choose an authentication method that is secure and reliable. Additionally, authentication methods should be regularly updated to ensure the latest security measures are in place.
Strong authentication is essential for ensuring that only authorized users can access a network. It is also important to have policies in place that specify when and how authentication should be used. For example, an organization may require authentication to access certain sensitive data or systems, or authentication may be required when accessing a wireless network from a public location.
2. Encryption
Encryption is the process of transforming data into a secure format so that it can only be read by intended recipients. Encryption is essential for protecting data when it is transmitted over a wireless network. Without encryption, data can be easily intercepted and read by malicious actors.
There are several different types of encryption, such as WEP, WPA, and WPA2. Each type of encryption has different levels of security and should be chosen based on the needs of the organization. It is important to note that some types of encryption, such as WEP, are outdated and should be avoided. Additionally, encryption keys should be regularly updated to ensure the latest security measures are in place.
Network Monitoring
Network monitoring is a critical component of wireless security. Monitoring a network allows administrators to identify potential threats and take action to mitigate them. Network monitoring can be done manually or with the help of automated tools.
Network monitoring involves regularly scanning the network for any suspicious activity. This includes monitoring traffic to and from the network, as well as checking for any unauthorized access. Additionally, network monitoring should include regular vulnerability scans and patching of any discovered vulnerabilities. This will help ensure the network is protected from any potential threats.
Firewalls
Firewalls are an important element of wireless network security. Firewalls are used to control access to the network and block any unauthorized or malicious traffic. A firewall can be configured to allow or deny access based on certain criteria, such as the source or destination of the traffic. Additionally, firewalls can be used to detect and block suspicious activity, such as port scans or network scans.
Firewalls are essential for protecting a network from malicious actors. It is important to configure the firewall properly and regularly update it to ensure the latest security measures are in place. Additionally, the firewall should be monitored to ensure it is functioning properly.
User Education
User education is an important part of any security strategy. It is important to educate users on the importance of security and the risks associated with using a wireless network. Additionally, users should be provided with information on how to properly use the network, such as how to connect to the network securely and how to protect their data.
User education should also include information on how to detect and respond to potential threats. This can include teaching users how to identify phishing emails or malicious links. Additionally, users should be taught how to properly protect their devices, such as enabling two-factor authentication or using a secure password manager.
Program Updates
Program updates are an essential part of any security strategy. It is important to regularly update the software and hardware used on the network. This will ensure that any security vulnerabilities are patched and the latest security measures are in place. Additionally, updates should be tested before being deployed to ensure they do not adversely affect the performance of the network.
Program updates should also be monitored to ensure updates are installed correctly. This is important for ensuring that the network is secure and that updates are not causing any issues. Additionally, users should be notified when an update is available and be provided with information on how to install it.
Frequently Asked Questions
Wireless network security is essential for protecting your data, privacy, and devices from unauthorized access. This FAQ highlights some of the key aspects of wireless network security, including authentication and encryption, that you need to understand in order to secure your network.
What are the two main types of authentication used in wireless networks?
The two main types of authentication used in wireless networks are user-based authentication and device-based authentication. User-based authentication involves verifying a user’s identity by having them enter a username and password. Device-based authentication, on the other hand, involves verifying a device’s identity by having it send an authentication token. In addition, some wireless networks also use two-factor authentication, which requires users to enter a username and password plus a one-time code sent to their device.
What is the difference between WEP and WPA encryption?
WEP (Wired Equivalent Privacy) is an older encryption technology that is no longer considered secure. WEP uses a static key that is shared by all users on the network in order to encrypt data. WPA (Wi-Fi Protected Access) is a more secure encryption technology that uses dynamic keys that are generated each time a user connects to the network. WPA also provides more robust protection against unauthorized access than WEP.
What is a wireless access point (WAP)?
A wireless access point (WAP) is a networking device that allows users to connect to a wireless network. WAPs are commonly used in offices, schools, and other public places to provide users with access to the Internet and other network services. WAPs can be used to create a single wireless network or multiple wireless networks, depending on the size and needs of the environment.
What is the purpose of a virtual private network (VPN)?
A virtual private network (VPN) is a secure network that is used to connect two or more computers over the Internet. VPNs are used to protect data from unauthorized access, and they can be used to safely access resources on a private network from a remote location. VPNs use encryption to ensure that data is secure while it is in transit.
What is a firewalls and which type of security does it provide?
A firewall is a system that is used to block unauthorized access to a network or computer. Firewalls can be either software-based or hardware-based, and they are used to prevent malicious traffic from entering a network. Firewalls provide both network-level security and application-level security. Network-level security is used to block malicious traffic at the network level, while application-level security is used to block malicious traffic at the application level.
Learn Wireless Network Security in 20 Minutes – All the Basics You Need to Know
In conclusion, wireless network security is a crucial aspect of modern-day technology. It is essential to understand the two statements that characterize wireless network security. The two statements that stand out in this regard are authentication and encryption. Authentication ensures that only authorized users have access to the network, while encryption protects the data transmitted over the network from being intercepted by unauthorized individuals. Thus, it is important to prioritize these two aspects of wireless network security to prevent cybercrime and safeguard sensitive data.
In conclusion, wireless network security is an ongoing process that requires constant attention and updates. It is vital to stay up-to-date with the latest security measures and to implement them effectively. Ignoring network security can lead to severe consequences, including data breaches, financial losses, and reputational damage. Therefore, it is essential to prioritize wireless network security by implementing robust authentication and encryption protocols and continuously monitoring the network for potential security threats. By doing so, individuals and organizations can ensure that their wireless networks remain secure and protected from malicious actors.