In today’s digital age, protecting sensitive information has become a top priority for individuals and organizations alike. Encryption is one of the most effective ways to safeguard data, and it involves converting plain text into a code that can only be deciphered by authorized parties. However, not all files need to be encrypted, and knowing which ones do can save time and resources while also ensuring that data is kept secure.
So, which files need to be encrypted with extensions? The answer depends on the type of information being stored and the level of risk involved in its exposure. In general, files that contain personal information, financial data, or confidential business plans should be encrypted to prevent unauthorized access. Examples of such files include spreadsheets, Word documents, PDFs, and databases. Additionally, any files that are sent or received via email or through online file sharing platforms should be encrypted to ensure that they cannot be intercepted or accessed by cybercriminals.
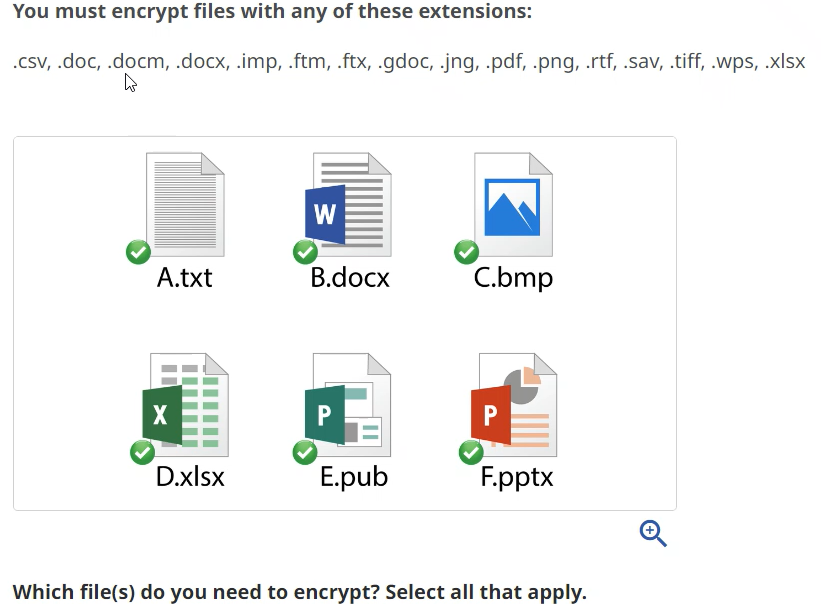
Important files that need to be encrypted typically have extensions such as .doc, .txt, .pdf, .xls, .ppt, .jpg, .gif, .png, and .zip. To securely encrypt these files, you will need to use a third-party encryption tool that meets the security requirements for your industry.
What are Encrypted Files?
Encrypted files are files that have been encoded so that only those with the correct encryption key can access them. They are used to protect confidential information stored on computers and on the internet. Encrypted files are more secure than unencrypted files because they are much harder to crack.
Encrypted files are typically used in business settings to protect sensitive data from unauthorized access and to ensure that data is not tampered with. In addition, encrypted files can be used to protect personal information such as passwords and credit card numbers.
What Files Need to be Encrypted with Extensions?
When it comes to encryption, there are a variety of file types that should be encrypted. These include documents, spreadsheets, images, audio, and video files. Documents such as Word documents, Excel spreadsheets, and PowerPoint presentations should be encrypted using extensions such as .docx, .xlsx, and .pptx. Image files such as JPEGs and PNGs should be encrypted using extensions such as .jpg and .png, respectively. Audio and video files should be encrypted using extensions such as .mp3 and .mp4.
In addition to these types of files, any files that contain sensitive information should also be encrypted. This includes files that contain passwords, financial information, customer information, or any other confidential data. These files should be encrypted using extensions such as .enc, .gpg, and .asc.
What is Encryption?
Encryption is a process of encoding data so that only those with the correct encryption key can access it. It is used to protect confidential information stored on computers and on the internet. Encryption is typically used in business settings to protect sensitive data from unauthorized access and to ensure that data is not tampered with.
Encryption is done using a variety of algorithms and tools. These algorithms and tools vary depending on the type of encryption being used. For example, symmetric encryption is used for data encryption between two parties, while asymmetric encryption is used for data encryption between more than two parties. Encryption keys are used to encrypt and decrypt data, and these keys must be kept secret at all times.
How to Implement Encryption?
Implementing encryption on a file or system requires careful planning and execution. The first step is to determine what type of encryption is needed. Once the type of encryption is determined, the encryption algorithm must be chosen and the encryption key must be generated. This key will be used to encrypt and decrypt the data.
The next step is to implement the encryption on the file or system. This involves encrypting the file or system using the encryption algorithm and key. In addition, the encryption key must be securely stored and protected from unauthorized access. It is also important to regularly review the encryption system to make sure it is working as expected.
Conclusion
Encrypting files is an important step in protecting sensitive data from unauthorized access. When it comes to encryption, documents, spreadsheets, images, audio, and video files should be encrypted using extensions such as .docx, .xlsx, .jpg, .png, .mp3, and .mp4. Any files that contain sensitive information should also be encrypted using extensions such as .enc, .gpg, and .asc. Implementing encryption requires careful planning and execution and the encryption key must be securely stored and protected at all times.
Frequently Asked Questions
What files need to be encrypted with extensions?
Encryption is the process of encoding data so that it is only readable by authorized personnel. Any type of file may need to be encrypted, depending on the sensitivity of the data and the security requirements of the organization. Generally, the most common types of files that need to be encrypted are those containing confidential or sensitive information, such as financial records, customer data, and personal or health information.
What types of files need to be encrypted?
The types of files that need to be encrypted depend on the sensitivity of the data and the security requirements of the organization. Generally, the most common types of files that need to be encrypted are those containing confidential or sensitive information, such as financial records, customer data, and personal or health information. It is also important to consider encrypting files that are shared with external parties, such as contracts, documents, and other sensitive information.
What file extensions should be encrypted?
Typically, any file that contains sensitive or confidential information should be encrypted. This includes files with extensions such as .doc, .xls, .pdf, .zip, and .ppt. It is important to note that encrypting files with these extensions will prevent unauthorized personnel from accessing the data contained in the file. However, it is also important to consider encrypting files with other extensions such as .jpg, .png, and .gif, as these files may contain sensitive information as well.
What are the benefits of encrypting files?
Encrypting files provides numerous benefits, including increased security and privacy. By encrypting files, organizations can ensure that information is only accessible by authorized personnel, thus protecting it from unauthorized access. Additionally, encrypting files can help protect against data breaches, as encrypted files are much more difficult to access and manipulate. Furthermore, encrypting files can help organizations comply with data protection regulations, such as the General Data Protection Regulation (GDPR).
How can I encrypt files?
There are a number of ways to encrypt files. One of the most common methods involves using encryption software, such as BitLocker or Microsoft Office 365. This software is designed to protect data by encrypting it at the file level and providing a secure key to access the data. Additionally, there are a number of third-party encryption tools available, such as VeraCrypt and AxCrypt, which can be used to encrypt files. Finally, organizations can also encrypt files manually by using a password-protected zip file.
How Does Individual File Encryption Work?
In conclusion, encryption is a crucial aspect of cybersecurity, and knowing which files to encrypt is essential to keeping sensitive data safe. While the list of file extensions that need to be encrypted may vary depending on your industry, it is always better to be safe than sorry. By encrypting your files, you are taking a proactive approach to protecting yourself and your clients from cyber threats.
So, if you are not sure which files need to be encrypted, start by identifying the information that could be harmful if it ended up in the wrong hands. Once you have done that, take the necessary steps to encrypt those files, and make sure that you are using a reliable encryption tool. With the right precautions in place, you can rest assured that your sensitive data is well-protected. Remember, encryption is not just an option, it is a necessity in today’s digital age.