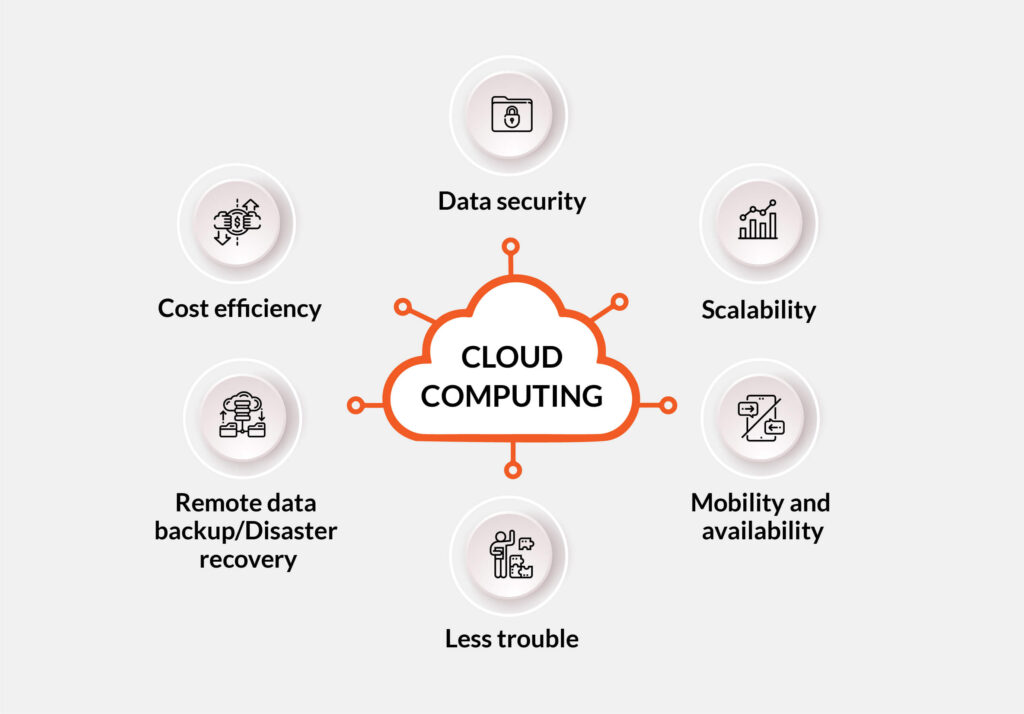
Cloud computing has become an integral part of modern-day businesses, enabling them to save on costs, scale more easily, and respond faster to market changes. However, with these benefits come potential risks, especially in terms of data security. As a business owner or IT professional, it is crucial to evaluate the security of your cloud service provider to ensure that your data is well-protected. This article will provide you with a comprehensive guide on how to evaluate cloud service provider security and make informed decisions to safeguard your data.
The evaluation process can be overwhelming, especially for startups or small businesses without dedicated IT teams. However, the good news is that evaluating cloud service provider security is not rocket science. With the right knowledge and approach, anyone can perform a thorough evaluation to ensure that their cloud provider meets the necessary security standards. In this article, we will provide you with a step-by-step guide, highlighting the essential factors to consider when evaluating cloud service provider security. So, whether you are a small business owner or an IT professional, read on to learn how to evaluate cloud service provider security and safeguard your data.
When evaluating a cloud service provider’s security, it is important to consider the following:
- Service Level Agreement: Review the Service Level Agreement (SLA) to ensure the cloud provider is offering the security features you need.
- Security Certifications: Check if the cloud provider is certified by a third-party security organization.
- Data Residency: Ensure that the provider is able to store data in the locations required by your organization.
- Data Encryption: Confirm that the provider is able to encrypt data at rest and in transit.
- Access Control: Verify that the provider can control access to data based on user roles.
- Audit Logging: Confirm that the provider can log user activities for auditing purposes.

Evaluating Cloud Service Provider Security
Cloud Service Providers (CSPs) offer cloud-based services to their customers, allowing them to access remote storage and computing resources. However, with the increasing usage of cloud services, it is becoming more important than ever to evaluate the security of CSPs. This article will discuss various aspects to consider when evaluating a CSP’s security, such as its data encryption capabilities, authentication methods, and incident response plans.
Data Encryption
Data encryption is one of the most important aspects of cloud security. It ensures that sensitive data is protected from unauthorized access and tampering. CSPs should use strong encryption algorithms, such as AES-256, and should encrypt data both in transit and at rest. In addition, they should also use additional measures, such as code signing, to ensure that the encryption keys are not compromised.
When evaluating a CSP’s data encryption capabilities, it is important to check that the CSP is compliant with relevant security standards, such as the Payment Card Industry Data Security Standard (PCI DSS). In addition, it is also important to check that the CSP provides detailed documentation on its encryption policies and procedures.
Authentication Methods
Authentication methods are used to verify the identity of users before allowing them to access cloud services. CSPs should use strong authentication methods, such as two-factor authentication, to ensure that only authorized users can access cloud services. In addition, they should also use access control measures, such as role-based access control, to limit user access to sensitive data and resources.
When evaluating a CSP’s authentication methods, it is important to check that the CSP is compliant with relevant security standards, such as the National Institute of Standards and Technology (NIST) Special Publication 800-53. In addition, it is also important to check that the CSP provides detailed documentation on its authentication policies and procedures.
Incident Response Plans
Incident response plans are used to identify and respond to security incidents in a timely and effective manner. CSPs should have robust incident response plans, including procedures for responding to security incidents, such as data breaches, denial-of-service attacks, and malicious insider threats. The plans should also include procedures for reporting security incidents to the appropriate authorities, such as law enforcement agencies.
When evaluating a CSP’s incident response plans, it is important to check that the CSP is compliant with relevant security standards, such as the NIST Special Publication 800-61. In addition, it is also important to check that the CSP provides detailed documentation on its incident response policies and procedures.
Third-Party Audits
Third-party audits are an important way to ensure that CSPs are adhering to security standards and best practices. CSPs should undergo regular audits to ensure that their systems and processes are secure and compliant with applicable laws and regulations. The audits should cover all aspects of the CSP’s security, including data encryption, authentication methods, and incident response plans.
When evaluating a CSP’s third-party audits, it is important to check that the CSP is compliant with relevant security standards, such as the International Organization for Standardization (ISO) 27001. In addition, it is also important to check that the CSP has provided detailed documentation on its audit results and processes.
Conclusion
Evaluating a CSP’s security is an important task for any organization that is considering using cloud services. It is important to evaluate each aspect of the CSP’s security, including data encryption, authentication methods, incident response plans, and third-party audits. Checking that the CSP is compliant with relevant security standards and has detailed documentation on its security policies and procedures is also important. By taking the time to evaluate a CSP’s security before using its services, organizations can ensure that their data is secure and protected.
Frequently Asked Questions about How to Evaluate Cloud Service Provider Security
Evaluating a cloud service provider’s security measures is important to ensure your data is protected and safe from malicious actors. Whether you’re using a public cloud, private cloud, or a hybrid cloud solution, understanding your cloud service provider’s security capabilities is key to keeping your data secure.
What Security Measures Should I Look for in a Cloud Service Provider?
When evaluating a cloud service provider’s security measures, there are a variety of factors to consider. It’s important to look for a provider that offers robust encryption, authentication, and access control capabilities. Additionally, look for providers that offer strong physical security measures, such as multiple firewalls and intrusion detection systems. It’s also important to look for providers who are proactive in terms of patching vulnerabilities and responding to security incidents.
What Are the Benefits of Choosing a Secure Cloud Service Provider?
Choosing a secure cloud service provider has a number of benefits, including improved data protection and better compliance with laws and regulations. Having a secure cloud storage solution in place can help protect your data from malicious actors, as well as from accidental data loss or destruction. Additionally, having a secure cloud solution in place can help you meet the requirements of various laws and regulations, such as the GDPR and HIPAA.
What Are the Risks of Using an Insecure Cloud Service Provider?
The risks of using an insecure cloud service provider are numerous. Without the proper security measures in place, your data may be vulnerable to malicious actors, such as hackers and identity thieves. Additionally, your data may be exposed to accidental data loss or destruction. Furthermore, if your provider is not compliant with various laws and regulations, you may be subject to fines and penalties.
What Should I Do if I Suspect My Cloud Service Provider Is Insecure?
If you suspect your cloud service provider is not secure, it’s important to take action right away. Contact your provider and inquire about their security measures. It may also be a good idea to conduct an audit of your provider’s security capabilities. This will help you identify any potential vulnerabilities and ensure your data is as secure as possible.
How Can I Ensure My Cloud Service Provider Is Secure?
The best way to ensure your cloud service provider is secure is to conduct regular audits and reviews of their security capabilities. Additionally, you should stay up-to-date on the latest security trends and technologies, and ensure your provider is using the latest security measures. Finally, it’s important to look for providers who are proactive in terms of patching vulnerabilities and responding to security incidents.

In conclusion, evaluating cloud service provider security is a crucial step for any organization that wants to ensure the safety and privacy of their data. It is important to understand the risks associated with cloud computing and choose a provider that prioritizes security measures. By following the tips outlined in this article, such as conducting a thorough security assessment, reviewing the provider’s compliance certifications and security protocols, and assessing their incident response plan, organizations can make informed decisions about their cloud service provider.
Ultimately, the responsibility of securing data in the cloud lies with both the organization and the cloud service provider. By working together and continually monitoring and updating security measures, the risk of data breaches and cyber attacks can be greatly reduced. It is important for organizations to prioritize security when choosing a cloud service provider and to regularly evaluate and update their security measures to ensure the safety and privacy of their data in the cloud.