In today’s world, privacy is a top concern for many smartphone users. With the increasing number of security breaches, it has become more important than ever to keep our personal data secure. One of the ways to achieve this is by encrypting our phones. Encryption is the process of converting data into a code that only authorized individuals can decipher. However, what happens when you forget your phone’s password or PIN, or maybe you have inherited an encrypted phone and you need to access the data? That’s where the need to decrypt an encrypted phone arises.
Decryption is the process of converting encrypted data back into its original form. It may seem like a daunting task, but with the right tools and techniques, it is possible to decrypt an encrypted phone. In this article, we will explore the methods that can be used to decrypt an encrypted phone and recover your data. Whether you are an individual looking to access your own encrypted phone or a professional who needs to decrypt a phone for forensic purposes, this article will provide you with the necessary information to get the job done. So, let’s dive in!
To decrypt an encrypted phone, you will need a secure PIN or password. First, unlock your device and open the Settings app. Next, select Security and enter your PIN or password to unlock the encryption. You will then be prompted to enter a new PIN or password. Once that is done, your device will be decrypted and you can access all of your data. If you ever forget your PIN or password, you may need to wipe your device in order to decrypt it.
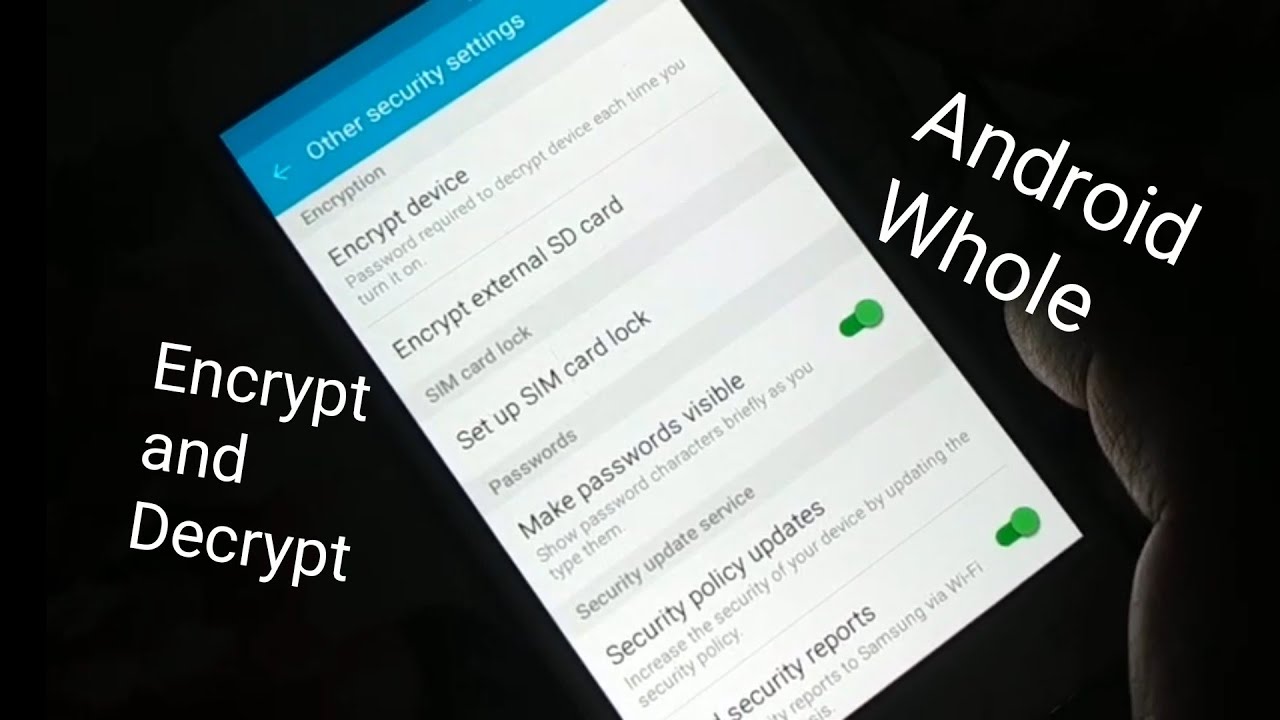
How to Decrypt an Encrypted Phone?
When it comes to encryption, it’s essential to understand the process of how to decrypt an encrypted phone. Encryption is a way to protect data from unauthorized access, and it’s used to protect sensitive information from being stolen or misused. It’s important to know the steps to decrypt a phone so that you can make sure that your data is secure.
Check the Encryption Method
The first step in decrypting a phone is to check the encryption method. Depending on the type of device, there are different methods of encryption that can be used. For example, some devices may use a passcode to gain access to the device, while other devices may use a special encryption key. It’s important to know the type of encryption that’s being used on the device, so that you can properly decrypt it.
Once you’ve determined the encryption method, you’ll need to check the device’s security settings. Depending on which type of encryption is being used, there may be certain settings that need to be changed in order to decrypt the device. For example, if the device is using a passcode, you may need to enter a new passcode in order to gain access to the device.
Decrypt the Device
Once you have the right encryption method and settings, you can decrypt the device. Depending on the type of encryption, this may involve entering a passcode or a special encryption key. Once the device is decrypted, you’ll be able to access the data stored on it.
It’s also important to remember that when you’re decrypting a phone, you’ll need to keep the device secure. This means that you should never share the encryption key or passcode with anyone else, and you should always keep the device in a secure location. By doing this, you can ensure that your data is safe and secure.
Frequently Asked Questions
Here you will find the answers to some common questions about decrypting an encrypted phone.
What is encryption?
Encryption is a process that makes data unreadable and unaccessible by encrypting the data with a cryptographic key. Encryption is used to protect sensitive data from unauthorized access, and can be used to ensure that data remains confidential even when it is sent over an insecure network. Data that is encrypted is often referred to as “ciphertext” because it is unreadable until it is decrypted back to its original form.
How do I decrypt an encrypted phone?
In order to decrypt an encrypted phone, you will need to have the necessary keys or passwords. Depending on the type of encryption used, the keys may be stored in the phone itself or on a server. Once you have the keys, you can use a decryption program to decrypt the data on the phone. The program will use the keys to decrypt the data and make it readable again.
What is the difference between encryption and decryption?
Encryption is the process of scrambling data so that it cannot be read by anyone without the correct key or password. Decryption is the opposite of encryption – it is the process of unscrambling the data so that it can be read by anyone with the correct key or password. Encryption is used to protect data from unauthorized access, while decryption is used to make data readable again.
What are the risks of decrypting an encrypted phone?
Decrypting an encrypted phone can be risky, as it opens up the possibility of unauthorized access to the data on the phone. If the phone is not properly secured, it is possible for malicious actors to gain access to the data. Additionally, if the keys used to encrypt the data are not properly secured, it is possible for them to be stolen and used to decrypt the data.
What should I do if I forget the keys to decrypt my phone?
If you have forgotten the keys used to encrypt your phone, you may have to reset the device in order to regain access to the data. This will erase all the data on the device, so it is important to make sure that you have backed up any important data before attempting to reset the phone. If you have not backed up the data, you may be able to recover it with the help of a data recovery specialist.
In conclusion, decrypting an encrypted phone requires a certain level of technical expertise and patience. It is not a task that can be achieved easily, but with the right tools and knowledge, it can be done successfully. It is important to note that decrypting a phone without the owner’s consent is illegal and can lead to serious consequences. Therefore, it is crucial to only attempt this process on your own phone or with the owner’s permission.
It is always wise to keep your phone encrypted to protect your sensitive information from falling into the wrong hands. However, in the event that you forget your password or need to access encrypted data on someone else’s phone, the above steps should help you decrypt an encrypted phone successfully. Remember to always seek professional help if you are not confident in your abilities and to never attempt to decrypt a phone without proper authorization.



