Major-General Jonathan Shaw’s expertise in cybersecurity and defence strategy has significantly influenced the future of national security. As the first Head of the Defence Cyber Security Programme at the UK Ministry of Defence, he played a pivotal role in spearheading modern cyber defence initiatives. We had the opportunity to sit down with Jonathan to delve into how organizations can enhance their cybersecurity measures, navigate evolving threats, and cultivate resilience in the age of digital warfare.
Reflecting on your tenure as Head of the Defence Cybersecurity Programme at the Ministry of Defence, what stands out as your most notable achievement in this capacity?


My proudest achievement was transitioning from a novice in the realm of cybersecurity to someone capable of articulating the conceptual nuances of this domain. While cybersecurity is undeniably technical, I quickly grasped that its broader implications were equally significant – particularly in how cyber technology permeates every facet of our lives.
Mastering the ability to elucidate a digital subject matter in an analog manner, thereby making it accessible to individuals with varying levels of understanding, stands out as my most significant accomplishment.
Effective leadership in cybersecurity demands a unique approach due to the disruptive nature of technology. Based on your experience, what characterizes effective cybersecurity leadership, and how should it adapt to confront the dynamic challenges of this swiftly evolving landscape?
Cyber poses inherent disruptions, particularly concerning information, which in turn disrupts the conventional hierarchy of knowledge transmission within organizations. While traditional structures are designed for senior leaders to receive information first, this paradigm does not align with the realities of the cyber realm.
Many of the senior leaders I encountered could be described as ‘cyber tourists’ – possessing a basic awareness but lacking profound expertise. Consequently, cybersecurity leadership must evolve to empower, educate, and entrust frontline individuals who possess a more profound comprehension of cyber threats.
This necessitates a shift away from rigid top-down directives towards a decentralized approach, akin to ‘mission command’ in the military. This model enables swifter decision-making and a more agile response to emerging threats.
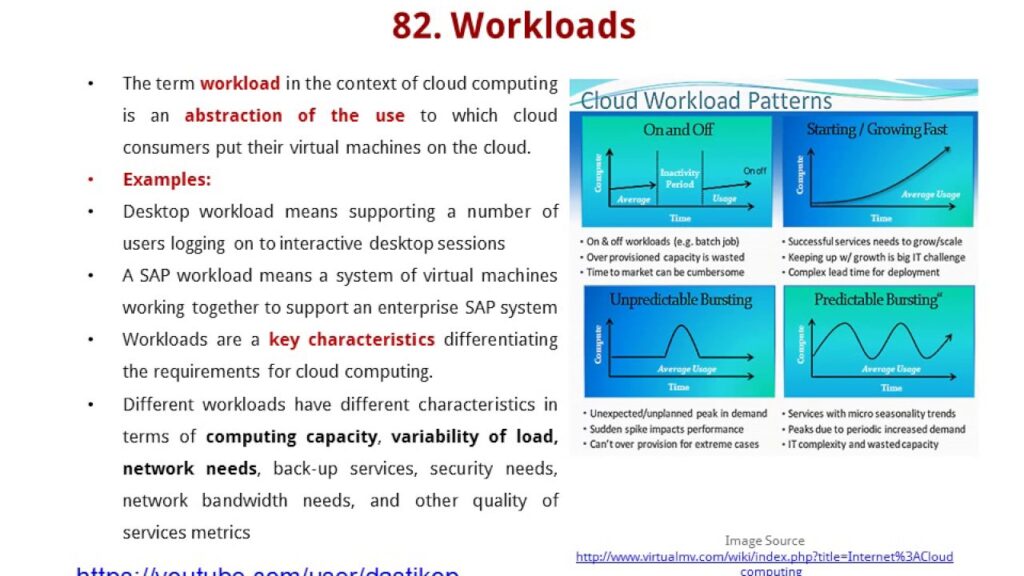
Organizations are increasingly vulnerable to cybercrime. What are the top three actionable steps they can take to fortify their defenses and enhance resilience against cyberattacks?
When devising defense strategies, most individuals concentrate on shields and barriers, akin to safeguarding a vehicle against assaults. However, a military analogy can provide valuable insights. In vehicular defense, multiple layers exist, with only one being a physical shield. The foremost and critical step is to remain undetected – to maintain invisibility.
Operate under the assumption that cyberspace is inherently insecure and adjust your practices accordingly. Heightened online visibility increases susceptibility to targeting. Although this may conflict with marketing imperatives, organizations must strike a balance. Additionally, individuals must cease trading privacy for convenience, a practice many have unwittingly engaged in.
The subsequent step involves acknowledging the inevitability of potential breaches. The more successful an organization, the likelier it is to be targeted. Hence, readiness is paramount. Foster resilience, establish redundancies, and equip your team with the capacity to respond effectively to breaches.
The final step entails ensuring that your entire supply chain adheres to stringent cybersecurity protocols. Vulnerabilities frequently stem from third-party vendors rather than internal systems. Therefore, cyber hygiene must extend beyond organizational boundaries to encompass partner networks. In essence, minimize exposure, prepare for potential breaches, and enforce high cybersecurity standards across your supply chain.
National infrastructure is susceptible to significant disruption from cyberattacks. To what extent can a national cyberattack impact daily life?
An exemplar of this vulnerability is the 2007 cyberattack launched by Russia in response to Estonia’s decision to relocate a statue. The attack effectively paralyzed Estonia, incapacitating banking systems, governmental operations, and media outlets, resulting in prolonged dysfunction within the country.
This incident prompted Estonia to emerge as a global frontrunner in cybersecurity. Subsequently, they established a national cyber defense unit, recognizing that cybersecurity is a shared responsibility. Their approach has since been hailed as best practice within Europe and beyond.
This case underscores the gravity of cyberattacks and underscores the imperative of national preparedness. A significant cyberattack can disrupt essential services, impede communication channels, and precipitate enduring economic repercussions. It serves as a poignant reminder that cybersecurity transcends governmental concerns, impacting individuals at all levels.
With technology evolving at a rapid pace, what do you foresee as the next major cyberattack type, and what emerging threats should we remain vigilant about?
Cyberspace’s inherent vulnerability is exemplified by instances such as Russia’s infiltration of the NSA database, wherein they discovered deliberate backdoors in various systems. Armed with a repository of vulnerabilities, cyber adversaries are poised to exploit such weaknesses. The SolarWinds breach is but one manifestation of this trend, with more occurrences likely on the horizon.
Another immediate concern revolves around the unwarranted faith in blockchain technology as an infallible security solution. While many regard it as a panacea, the reality is starkly different. Blockchain harbors vulnerabilities, has been breached previously, and contains zero-day exploits. The notion that blockchain guarantees cyber resilience is fundamentally flawed.
In the long run, this issue transcends mere cybersecurity concerns to become a cultural quandary. We are witnessing a transition from what is colloquially termed ‘United States digital colonialism’ – where Western values underpinned digital technology development – to ‘Chinese digital colonialism’. The former head of cybersecurity at the Pentagon has contended that the West has already ceded ground in the artificial intelligence realm, with China poised to dominate the AI landscape.
This paradigm shift will fundamentally redefine the underpinnings of software development. As AI assumes a more pervasive role, we must navigate a landscape where software and cybersecurity frameworks are shaped by divergent cultural and strategic imperatives.
What is the likelihood of a successful cyberattack on national infrastructure, and what factors influence the probability of such an event?
If adversaries identify vulnerabilities, they will exploit them. The question does not revolve around the feasibility of a national cyberattack, but rather how effectively we can mitigate its repercussions.
Notably, major states refrain from direct cyber warfare due to the principle of mutually assured destruction. The prospect of a full-fledged cyberattack is unappealing to nations like China and Britain, as both parties recognize the catastrophic fallout such a scenario would entail.
Conversely, criminal entities serve as proxies for state actors, presenting a more formidable threat. These non-state groups lack infrastructure that can be retaliated against, rendering them more elusive. Some contend that these groups operate under indirect state control, a proposition that warrants scrutiny.
However, given that cybercriminals operate from physical locales, they remain susceptible to pressure. These entities are not enigmatic entities but are rooted in countries like Russia, China, and Bulgaria. Governments possess the means to disrupt their activities through diplomatic and economic interventions.
Despite the expansive attack surface the internet presents, tangible repercussions can be imposed on cybercriminals. Ultimately, if an attack is imminent, its success is almost inevitable, underscoring the criticality of preparedness and mitigation strategies.
If you could offer a piece of advice to your younger self, what would it be?
Unrelated to cybersecurity, my advice would center on seizing opportunities and fostering self-assurance. Reflecting on my journey, I lament not the actions I took, but the paths I chose not to explore. Embracing opportunities with greater confidence could have yielded substantial dividends.
Life is not a dress rehearsal – one must seize the moment and capitalize on the present, for time passes swiftly. At 63, I harbor a sense of accomplishment, yet I am cognizant that greater feats could have been achieved. The present always offers opportunities for growth and advancement.
Image by Free stock photos from www.rupixen.com from Pixabay, and Champions Speakers.
This interview with Jonathan Shaw was conducted by Mark Matthews.
Keen to delve deeper into cybersecurity and cloud technology insights from industry experts? Explore the Cyber Security & Cloud Expo events in Amsterdam, California, and London.
Discover additional forthcoming enterprise technology events and webinars facilitated by TechForge here.