As the world becomes increasingly digital, businesses and organizations are flocking to cloud computing services for their data storage and software needs. The benefits of cloud computing are numerous, including increased flexibility, scalability, and accessibility. However, with these benefits also come potential security risks, especially when it comes to sensitive information. In this article, we will explore the security risks of cloud computing, specifically in relation to the popular platform Fresco Play.
Fresco Play is a cloud-based platform that provides e-learning solutions to businesses and organizations. While it is a highly effective tool for training and development, the platform is not immune to security threats. As more and more businesses move their operations to the cloud, it is essential to understand the potential risks involved and take appropriate measures to protect sensitive data. Join us as we delve into the security risks of cloud computing with a focus on Fresco Play, and explore ways to mitigate those risks for a safer and more secure cloud computing experience.
The security risks of cloud computing with Fresco Play include data breaches, unauthorized access, malicious attacks, and data loss. Businesses should take certain measures to protect their data when using cloud services, such as encryption, authentication, and monitoring.

What is Cloud Computing?
Cloud computing is a form of computing that allows users to access resources, applications, and services hosted in the cloud. It is a distributed computing system that provides resources such as storage, processing, and networking over the Internet. Cloud computing is also known as “on-demand computing” because it allows users to access the resources they need, when they need them.
What are the Security Risks of Cloud Computing Fresco Play?
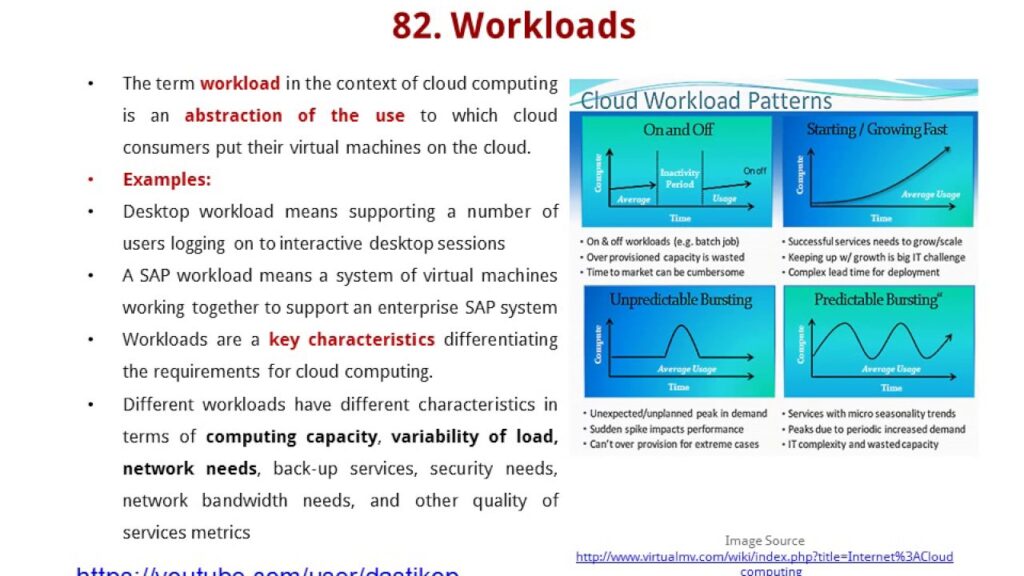
Cloud computing has numerous security risks that need to be addressed. The most common security risks associated with cloud computing are data loss, unauthorized access, and data leakage. Additionally, cloud computing services may be vulnerable to malicious attacks, such as Distributed Denial of Service (DDoS) attacks, which can cause disruption to the service.
Data Loss
Data loss is one of the most common security risks associated with cloud computing. Data loss can occur due to hardware or software failures, human error, malicious attacks, or natural disasters. It is important to ensure that data is backed up regularly to minimize the risk of data loss. Additionally, data should be stored in multiple locations to ensure that it is accessible in the event of a data loss.
Unauthorized Access
Unauthorized access is another security risk associated with cloud computing. Unauthorized access can occur if users do not use strong passwords or if user accounts are not properly managed. Additionally, cloud computing systems can be vulnerable to malicious attacks, such as brute force attacks, which can be used to gain unauthorized access to accounts. To mitigate this risk, it is important to ensure that users have strong passwords and that user accounts are properly managed.
Data Leakage
Data leakage is a risk that occurs when sensitive data is inadvertently exposed to unauthorized parties. This can occur due to a lack of proper security measures or if users do not follow security best practices. To mitigate this risk, it is important to ensure that data is encrypted and that proper security measures are in place. Additionally, users should be educated on the importance of following security best practices.
Malicious Attacks
Malicious attacks, such as Distributed Denial of Service (DDoS) attacks, are a security risk associated with cloud computing. DDoS attacks are a type of attack that can be used to disrupt the service of a cloud computing system. To mitigate this risk, it is important to ensure that the system is properly secured and that measures are in place to detect and respond to malicious attacks.
Credential Theft
Credential theft is another security risk associated with cloud computing. Credential theft can occur if users do not use strong passwords or if user accounts are not properly managed. Additionally, attackers can use techniques such as phishing or keylogging to gain access to user credentials. To mitigate this risk, it is important to ensure that users have strong passwords and that user accounts are properly managed.
Insecure APIs
Insecure application programming interfaces (APIs) are a security risk associated with cloud computing. APIs are used to allow applications to communicate with one another, however, if they are not properly secured, they can be vulnerable to malicious attacks. To mitigate this risk, it is important to ensure that APIs are securely configured and that proper security measures are in place.
Insider Threats
Insider threats are another security risk associated with cloud computing. Insider threats can occur if users do not follow security best practices, or if malicious insiders gain access to the system. To mitigate this risk, it is important to ensure that users are educated on the importance of following security best practices, and that proper security measures are in place to detect and respond to malicious insiders.
Frequently Asked Questions
This page provides answers to some of the most frequently asked questions about the security risks of cloud computing fresco play.
What are the security risks of cloud computing fresco play?
Cloud computing Fresco Play is a cloud-based platform that allows users to create, store, and share multimedia content such as videos and images. While the platform provides a convenient and efficient way to store and share content, there are some security risks that need to be taken into consideration.
The main security risks of cloud computing Fresco Play are the potential for unauthorized access to the data, the possibility of data being altered, and the risk of data being stolen. Unauthorized access is a risk because the cloud platform stores user data and content on servers that are accessible by anyone with internet access. Furthermore, if the data is stored on a public cloud, it is possible for malicious actors to access the data and alter or steal it. Additionally, the cloud platform may not be able to protect the data from being altered or stolen due to weak security measures.
What measures are in place to protect user data?
Cloud computing Fresco Play has implemented several security measures to protect user data. For example, the platform encrypts all data stored on its servers, meaning that the data is unreadable unless the user has the encryption key. Additionally, the platform implements user authentication protocols to ensure that only authorized individuals can access the data. Finally, the platform has implemented a data backup and recovery system to ensure that user data is not lost in the event of a system failure.
Furthermore, the platform also provides users with the ability to control access to their data, allowing them to grant access to only certain individuals or groups. This allows users to control who has access to their data and helps prevent unauthorized access to the data. Additionally, users can also set up two-factor authentication, which requires users to enter a code or password sent to their phone or email in order to access the data.
How can users ensure their data is secure?
In order to ensure that their data is secure, users should take steps to protect their data. Firstly, they should ensure that they are using strong passwords and two-factor authentication, as this will help prevent unauthorized access to their data. Additionally, they should only grant access to trusted individuals and groups, and regularly review the list of individuals who have access to their data.
Furthermore, users should create backups of their data and store them in an off-site location, as this will help ensure that their data is still accessible in the event of a system failure. Additionally, users should also ensure that their cloud platform is regularly updated with the latest security patches and updates, as this will help ensure that their data is protected against the latest threats.
What should users do if their data is compromised?
If users suspect that their data has been compromised, they should take immediate action to protect their data and prevent further damage. Firstly, they should immediately change their passwords and two-factor authentication codes. Additionally, they should review the list of individuals who have access to their data and revoke access to any suspicious individuals or groups.
Furthermore, users should also contact the cloud platform provider and request that they investigate the issue and take any necessary measures to protect the user’s data. Additionally, users should also contact their local law enforcement and report the incident, as this will help ensure that the perpetrator is brought to justice.
What other security measures should users take?
In addition to the measures mentioned above, users should ensure that their devices are secure and up-to-date. This includes ensuring that their devices are running the latest operating system updates, as well as installing antivirus and anti-malware software. Additionally, users should also be aware of phishing and other social engineering attacks, as these can be used to gain access to user data.
Finally, users should also be aware of how their data is being used and shared. Users should make sure that any third-party services they are using are secure, and that any data they share is done so securely. Additionally, users should ensure that they are only sharing data with individuals and organizations that they trust, as this will help ensure that their data remains secure.

In conclusion, the adoption of cloud computing has revolutionized the way organizations store and manage their data. However, with the numerous benefits of this technology, there are also security risks associated with it, especially for companies like Fresco Play that rely on cloud computing for their business operations. These security risks include data breaches, unauthorized access to sensitive information, and potential loss of data due to system failures.
To mitigate these risks, it is essential for organizations to implement effective security measures such as encryption, two-factor authentication, and regular security audits. Additionally, businesses should carefully evaluate their cloud service providers and ensure they have robust security protocols in place. By taking these precautions, organizations can enjoy the benefits of cloud computing while minimizing the potential security risks. As cloud computing continues to grow in popularity, it is crucial for businesses to prioritize security to protect their data and reputation.