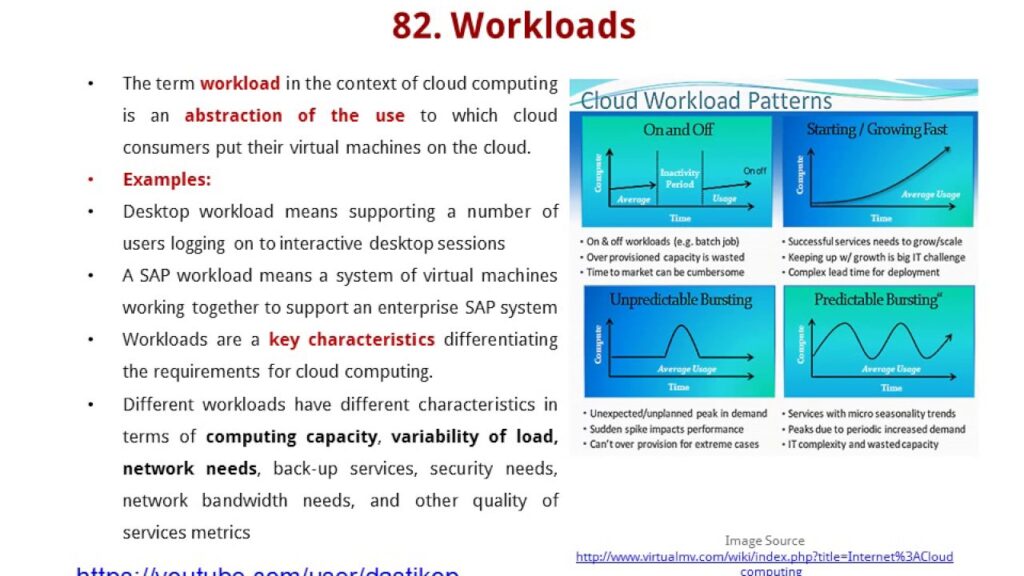
Cloud computing has revolutionized the way businesses operate by offering cost-effective, scalable, and efficient solutions for data storage, processing, and management. However, one of the major concerns that have always been associated with cloud computing is the risk of multitenancy. Multitenancy refers to the practice of hosting multiple clients on the same server or infrastructure. This poses a significant risk, as it can increase the chances of data breaches, security threats, and privacy violations. But, is there a way to remove this risk in cloud computing? In this article, we will explore the answer to this critical question.
To understand how to remove the risk of multitenancy in cloud computing, it is important to first understand what multitenancy is and why it poses a threat. Additionally, we will delve into the various techniques and technologies that can be employed to mitigate the risks associated with multitenancy. By the end of this article, you will have a comprehensive understanding of how to effectively manage multitenancy in cloud computing and ensure that your data is secure and protected. So, let’s get started and explore the world of cloud computing and multitenancy.
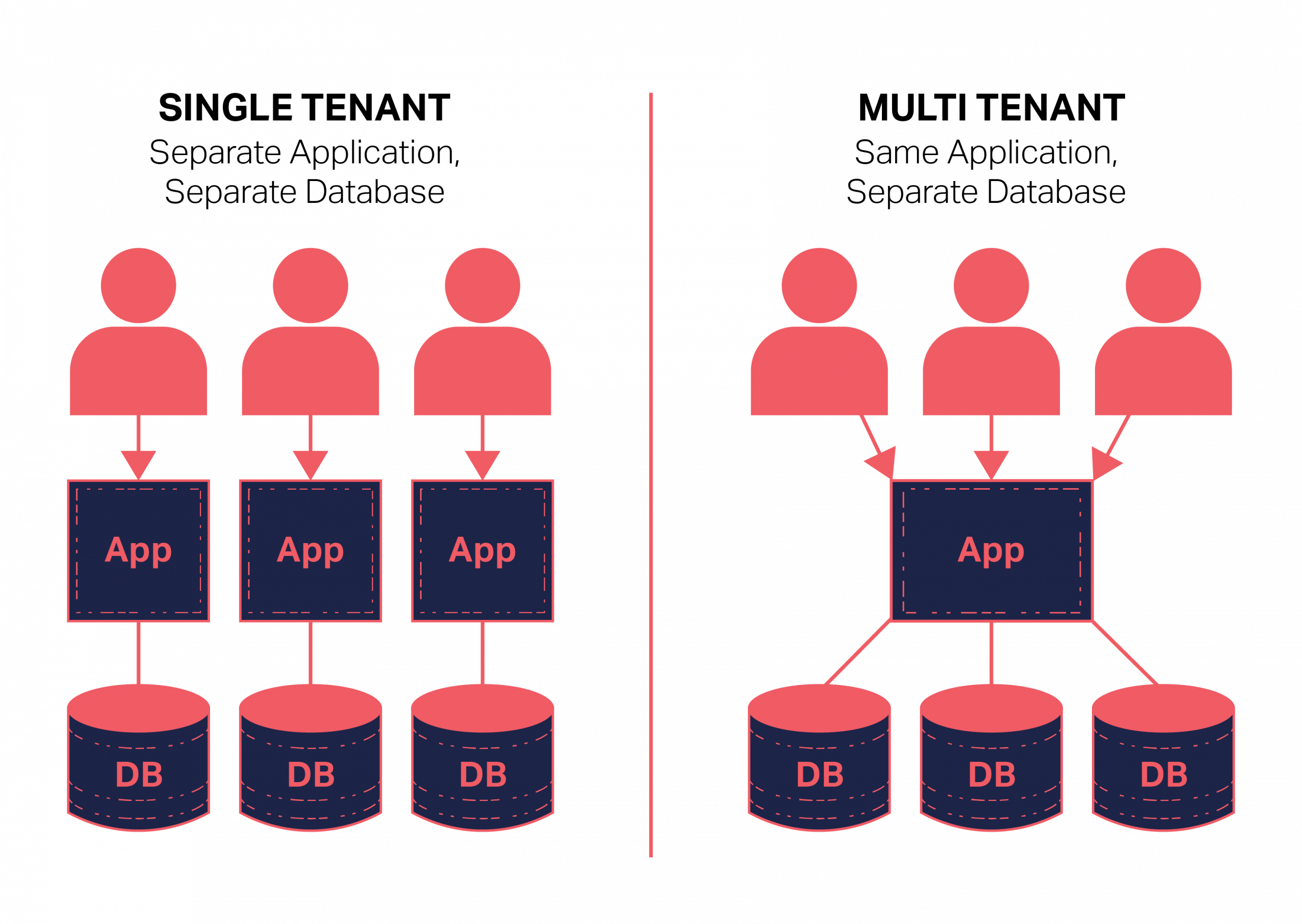
What Removes the Risk of Multitenancy in Cloud Computing?
Cloud computing has become increasingly popular in recent years, as organizations have realized the many benefits it provides, such as increased scalability, efficiency, and cost savings. However, the prevalence of multitenancy in cloud computing can pose a significant security risk. This article will explore what removes the risk of multitenancy in cloud computing.
Virtualization
One of the most effective ways to reduce the risk of multitenancy in cloud computing is through virtualization. Virtualization involves creating multiple virtual machines, each of which runs its own operating system and applications. By isolating each of these virtual machines, cloud service providers can ensure that a tenant’s data and applications are not accessible to other tenants. This isolation reduces the risk of malicious actors gaining access to sensitive data and applications. Additionally, virtualization allows tenants to customize their environment to meet their specific needs.
Secure Data Storage
Another important factor in reducing the risk of multitenancy in cloud computing is secure data storage. Cloud service providers must ensure that data is encrypted both in transit and at rest. Additionally, data should be stored in secure data centers that are monitored for suspicious activity. By implementing these measures, cloud service providers can ensure that data remains secure and protected from unauthorized access.
Multi-factor Authentication
Multi-factor authentication is also an important factor in reducing the risk of multitenancy in cloud computing. Multi-factor authentication requires users to provide multiple pieces of evidence to prove their identity, such as a password, biometric scan, or a security token. By implementing multi-factor authentication, cloud service providers can ensure that only authorized users are able to access sensitive data and applications.
Access Control
Access control is another effective way to reduce the risk of multitenancy in cloud computing. Access control involves granting users access to only the data and applications that are necessary for them to perform their job. By limiting user access, cloud service providers can ensure that malicious actors are unable to gain access to sensitive data. Additionally, access control ensures that all users are held accountable for their actions.
Security Audits and Reviews
Security audits and reviews are also an important factor in reducing the risk of multitenancy in cloud computing. Security audits involve assessing the security posture of a cloud service provider and identifying any vulnerabilities that need to be addressed. Security reviews involve continuously monitoring the security posture of a cloud service provider, and taking corrective action if any vulnerabilities are identified. By implementing security audits and reviews, cloud service providers can ensure that their systems remain secure and protected from malicious actors.
Incident Response Plans
Finally, cloud service providers should also develop incident response plans to reduce the risk of multitenancy in cloud computing. Incident response plans involve creating procedures for dealing with potential security incidents, such as data breaches or malicious actors. By developing these plans, cloud service providers can ensure that they are prepared to respond quickly and effectively to any security incidents.
Conclusion
Multitenancy in cloud computing can pose a significant security risk, but there are several measures that cloud service providers can take to reduce this risk. These measures include virtualization, secure data storage, multi-factor authentication, access control, security audits and reviews, and incident response plans. By implementing these measures, cloud service providers can ensure that their systems remain secure and protected from malicious actors.
Frequently Asked Questions
This article answers commonly asked questions about the removal of multitenancy risks in cloud computing.
What is multitenancy?
Multitenancy is the ability of a cloud service provider to provide access to multiple customers from the same cloud instance. This means that the same software and hardware resources are shared by multiple customers, allowing the cloud provider to reduce costs and maximize efficiency. However, this also increases the risk of security breaches, privacy issues, and other risks associated with multitenancy.
What removes the risk of multitenancy in cloud computing?
The removal of the risk of multitenancy in cloud computing can be achieved by using a variety of methods. Some of the most common methods include the use of virtualization technologies, such as virtual machines and containers. These technologies allow multiple customers to access the same resources without them being shared by other customers and without the risk of security breaches or privacy issues. Additionally, the use of data isolation techniques and access control can also help to reduce the risk of multitenancy in cloud computing.
Are there any other risks associated with multitenancy in cloud computing?
Yes, there are a number of other risks associated with multitenancy in cloud computing. These include the potential for data breaches, resource contention, and performance degradation. Additionally, there is also the risk of unauthorized access to customer data, which is a significant concern for cloud service providers.
What are some strategies for mitigating the risks of multitenancy in cloud computing?
Some strategies for mitigating the risks of multitenancy in cloud computing include the implementation of security protocols and procedures, such as authentication and authorization, as well as the use of encryption and other data protection techniques. Additionally, the use of resource isolation and access control techniques can also help to reduce the risk of multitenancy.
What is the most effective way to ensure the security of customer data in a multi-tenant environment?
The most effective way to ensure the security of customer data in a multi-tenant environment is to implement a comprehensive security framework. This should include the use of encryption technologies, access control protocols, and other security measures. Additionally, the use of data isolation techniques, such as virtualization, can also help to reduce the risk of unauthorized access to customer data. Finally, it is important to ensure that the cloud service provider has adequate processes in place to monitor and detect any potential security breaches.
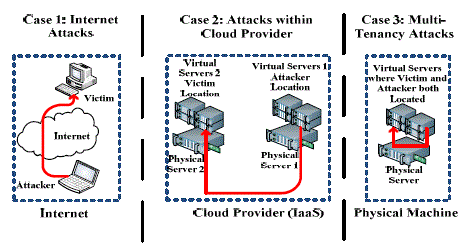
In conclusion, multi-tenancy in cloud computing can be a significant risk to the security and privacy of your data. However, with the right measures in place, you can mitigate these risks and enjoy the many benefits of cloud computing. The most effective way to remove the risk of multi-tenancy is to implement strong data encryption, access controls, and monitoring tools. These measures will ensure that your data remains private and secure, even in a shared environment.
Furthermore, working with a trusted cloud service provider can also go a long way in minimizing the risk of multi-tenancy. A reputable provider will have robust security protocols in place, such as regular audits, vulnerability testing, and compliance with industry standards. By partnering with a reliable provider, you can benefit from their expertise and resources while ensuring that your data is kept safe and secure. Ultimately, by taking the necessary precautions and working with trusted partners, you can enjoy the many advantages of cloud computing without compromising on security or privacy.