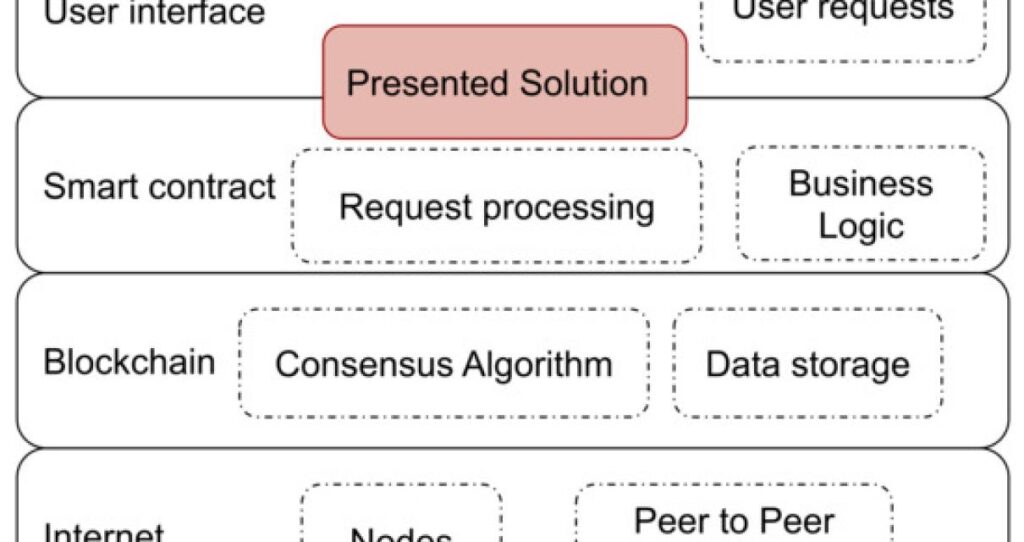
Blockchain technology has revolutionized the way we carry out transactions. Its decentralized and secure nature has made it one of the most popular transaction platforms in the world. However, despite its advanced security features, blockchain technology is not entirely immune to hacking attempts. One of the most common types of hacking attempts is the manipulation of unconfirmed transactions. Hackers often target unconfirmed transactions as they are easier to manipulate and can result in significant financial losses.
But how do hackers hack blockchain unconfirmed transactions? This is a question that has been on the minds of many blockchain users. In this article, we will explore some of the techniques used by hackers to hack blockchain unconfirmed transactions. We will also provide some tips on how to protect yourself from these hacking attempts. So, whether you are a blockchain enthusiast, a business owner, or an individual user, this article is for you. Stay tuned for some valuable insights on how to protect your blockchain transactions from hacking attempts.
Hacking unconfirmed blockchain transactions is not an easy process. It requires knowledge of programming, cryptography, and blockchain technologies. The process involves using a third-party service known as a double-spend transaction to manipulate the transaction records.
To begin, you must first obtain the unconfirmed transaction data from the blockchain network. Then, you must analyze the data in order to determine the transaction outputs and inputs. Once you have identified the data, you must create a double-spend transaction to replace the original one. Finally, you must broadcast this new transaction to the network in order to confirm the transaction.
This process is not recommended for those without programming or cryptographic knowledge. It is also not recommended for those without the necessary resources to properly execute the process. It is highly recommended that you consult with a professional before attempting to hack unconfirmed blockchain transactions.

How to Hack Blockchain Unconfirmed Transactions?
Hacking blockchain unconfirmed transactions is a complex process that requires a lot of technical knowledge and experience. It can be a lucrative way to make money, but it also carries a lot of risk. In this article we will explore the basics of hacking blockchain unconfirmed transactions, and provide some tips on how to do it safely and securely.
What are Unconfirmed Transactions?
Unconfirmed transactions are transactions that have not yet been added to the blockchain. This means that they have not been processed, verified, or added to the public ledger. When a transaction is unconfirmed, it is still pending and not yet part of the blockchain. Unconfirmed transactions can be vulnerable to attack, as there is no way to verify the authenticity of the transaction.
Unconfirmed transactions are often used by attackers who are looking to double spend their funds, or to send funds to an address that does not exist. Attackers can also use unconfirmed transactions to try and manipulate the blockchain, or to perform a 51% attack. It is important to note that unconfirmed transactions are risky and should be avoided unless absolutely necessary.
How to Hack Blockchain Unconfirmed Transactions?
Before attempting to hack blockchain unconfirmed transactions, it is important to understand the risks involved. Hacking unconfirmed transactions can be difficult, and there is a chance that it could lead to the loss of funds. It is also important to note that hacking unconfirmed transactions is illegal in most countries.
When hacking blockchain unconfirmed transactions, the most common method is to use a “blockchain splitter”. This tool splits the blockchain into two separate chains, allowing the hacker to access the funds in the unconfirmed transactions. This method is often used by attackers to double spend their funds, or to send them to an address that does not exist. It is important to note that this method is risky and should not be attempted without a thorough understanding of the process.
What are the Risks of Hacking Unconfirmed Transactions?
Hacking unconfirmed transactions carries a number of risks, including the potential for financial loss, legal repercussions, and the possibility of damaging the blockchain itself. It is important to remember that hacking unconfirmed transactions is illegal in most countries, and can lead to serious legal consequences. Additionally, hacking unconfirmed transactions can also lead to a loss of funds, as the hacker will not be able to access the funds in the unconfirmed transactions.
In addition to the financial and legal risks, hacking unconfirmed transactions can also lead to the manipulation of the blockchain. This can lead to a variety of problems, including double spending, 51% attacks, and more. It is important to note that these risks are serious, and should not be taken lightly.
How to Protect Yourself When Hacking Unconfirmed Transactions?
When attempting to hack unconfirmed transactions, it is important to take steps to protect yourself. It is important to use a reputable service that specializes in blockchain security, as this will help to protect your funds and keep them secure. Additionally, it is important to use a secure connection when accessing the blockchain, as this will help to prevent attackers from accessing your funds.
It is also important to use a secure wallet when storing your funds. A secure wallet will help to ensure that your funds are safe, and that they cannot be accessed by hackers. Additionally, it is important to use two-factor authentication when accessing the blockchain, as this will help to protect your funds from being stolen. Finally, it is important to use a secure password when accessing the blockchain, as this will help to protect your funds from being stolen.
Frequently Asked Questions
Blockchain unconfirmed transactions are highly secure and typically take a few minutes to process. However, in some cases, the transaction may take longer than usual. This can be due to a variety of reasons, such as network congestion or a low transaction fee.
What is a blockchain unconfirmed transaction?
A blockchain unconfirmed transaction is a digital transfer of funds between two parties that has not yet been approved by the blockchain network. This means that the transaction has not yet been added to the blockchain and is still pending. It is important to note that the funds are still in the possession of the sender until the transaction is confirmed.
How can I hack an unconfirmed transaction?
Hacking an unconfirmed transaction is not possible. The blockchain is a highly secure system that uses cryptography and distributed computing to verify and process transactions. This means that it is virtually impossible to hack a blockchain transaction.
What is double spending?
Double spending is a type of attack on the blockchain in which a user tries to spend their funds more than once. In order to do this, the user would need to alter the transaction history on the blockchain, which is virtually impossible due to the security measures in place.
How can I speed up my unconfirmed transaction?
If your transaction is taking longer than usual to process, there are a few things you can do to speed up the process. The first is to increase the transaction fee. This will incentivize miners to prioritize your transaction and process it faster. You can also try resending the transaction. This will create a new transaction with a higher fee, which may be processed faster.
What is transaction malleability?
Transaction malleability is a type of attack on the blockchain in which a user attempts to modify the transaction ID. This is done by changing the data in the transaction, such as the amount or the recipient. This can lead to the transaction being rejected by the network, or the funds being sent to an unintended recipient.
HOW TO HIJACK UNCONFIRMED BITCOIN TRANSACTION TO YOUR BLOCKCHAIN WALLET+2022 NEW UPDATE
In conclusion, the idea of hacking blockchain unconfirmed transactions is not only unethical but also illegal. The blockchain technology has been designed to ensure transparency, security, and immutability. Any attempt to manipulate the blockchain system will only lead to severe consequences. Instead of trying to hack the blockchain network, it is essential to follow the recommended procedures and wait for the confirmation of your transaction. This will not only guarantee the security of your funds but also maintain the integrity of the blockchain technology.
Finally, it is crucial to note that the blockchain technology is still in its infancy, and there is much to be discovered. As the technology continues to evolve, so do the security measures that protect it. Therefore, it is essential to stay updated with the latest trends and developments in the blockchain space. In conclusion, the blockchain technology has the potential to revolutionize the world, and it is our responsibility to ensure its security and sustainability.