As technology continues to advance, the need for network security becomes increasingly important. With the rise of cyber threats, it has become essential for businesses to protect their sensitive information from unauthorized access. One way to do this is through network hardening, which involves implementing security measures to prevent and mitigate potential attacks. However, even with the best intentions, it is possible to overlook certain areas that need to be hardened.
In this article, we will explore the topic of network hardening and specifically focus on one question: which is not a common hole for network hardening? By understanding the common vulnerabilities in network security, we can take steps to ensure that our networks are fortified against potential threats. So, let’s dive in and explore the various aspects of network hardening to discover which holes are commonly overlooked.
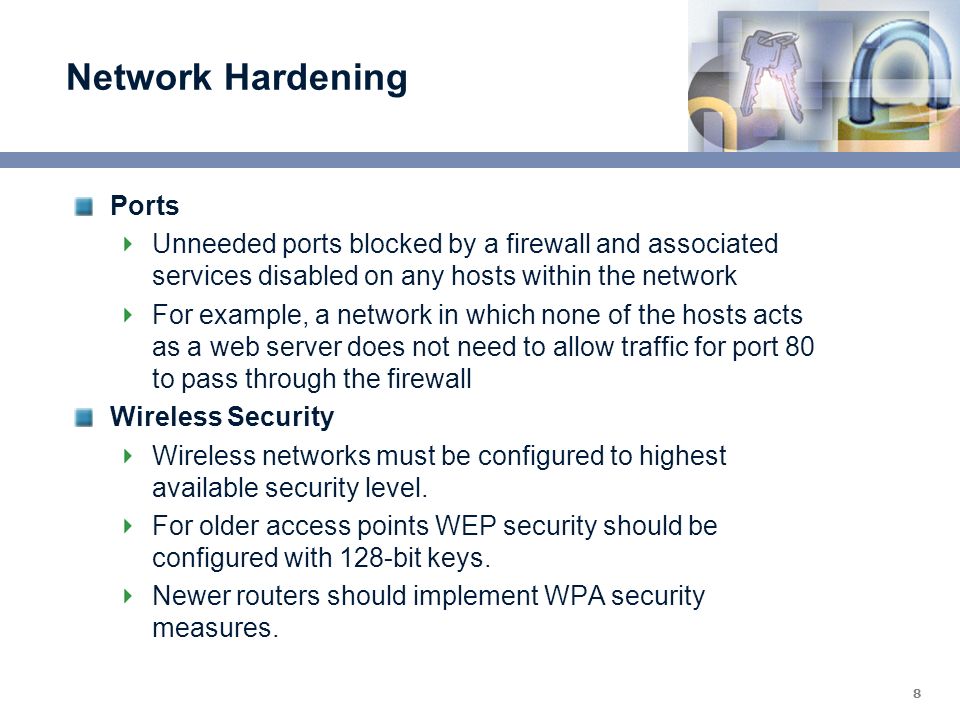
Network Hardening: What it is and What it Isn’t
Network hardening is the process of securing a network by reducing its attack surface. It involves taking steps to reduce the potential avenues of attack and ensure that any vulnerabilities that exist in the network are minimized. The goal of network hardening is to ensure that the network is as secure as possible from malicious actors or attacks.
Network hardening includes measures such as patching and updating systems, using encryption and authentication protocols, and implementing access control measures. It also involves physical security measures, such as secure data centers, locked cabinets, and access control policies.
What is a Common Hole for Network Hardening?
One of the most common holes for network hardening is the use of weak passwords. Passwords are the first line of defense against malicious actors or attackers, and using weak passwords can leave a network vulnerable to attack. It is important to use strong passwords that are difficult to guess and change them regularly.
Another common hole for network hardening is the use of unsecured Wi-Fi networks. Unsecured Wi-Fi networks are vulnerable to attack, as they do not require authentication or encryption protocols. It is important to use secure Wi-Fi networks that require authentication and encryption protocols to protect the network.
Which is Not a Common Hole for Network Hardening?
One hole that is not commonly considered when it comes to network hardening is the use of outdated software and hardware. While it is important to keep systems up-to-date with the latest patches and security updates, outdated software and hardware can also be a security risk. Outdated operating systems and software may have vulnerabilities that have not been patched or addressed, and outdated hardware can be vulnerable to attacks that have been discovered since the hardware was released. It is important to keep systems up-to-date in order to ensure that any known vulnerabilities are addressed.
Frequently Asked Questions
Below are the answers to some frequently asked questions about network hardening.
What is network hardening?
Network hardening is the process of enhancing the security of a computer network by strengthening the existing defenses and closing any potential vulnerabilities. It involves implementing measures such as updating software, establishing firewall rules, implementing access control mechanisms, and deploying intrusion detection systems.
What are the benefits of network hardening?
Network hardening can help protect a network from malicious actors, malware, and other threats. By strengthening the existing defenses, it can help protect the network from unauthorized access and data breaches. Additionally, network hardening can help reduce the risk of data loss, as well as help ensure compliance with industry and legal regulations.
What are some of the most common holes for network hardening?
Some of the most common holes for network hardening include weak passwords, outdated software, lack of two-factor authentication, unencrypted data, and open ports. It is important to identify and address these vulnerabilities in order to ensure the security of the network.
What is not a common hole for network hardening?
Physical security is not a common hole for network hardening. Physical security refers to the protection of physical assets, such as computers, servers, and other equipment, from unauthorized access or damage. While physical security is an important part of overall network security, it is not typically addressed through network hardening.
What measures can be taken to harden a network?
There are many measures that can be taken to harden a network. These include updating software, implementing access control mechanisms, establishing firewall rules, deploying intrusion detection systems, and using encryption. Additionally, regular patching should be done to ensure that any newly discovered vulnerabilities are addressed. It is also important to monitor the network for any suspicious activity.
Network Hardening – N10-008 CompTIA Network+ : 4.3
In conclusion, network hardening is a critical aspect of securing any computer network. It involves taking proactive measures to protect a network from malicious attacks and unauthorized access. While there are several common holes that attackers can exploit, it is equally important to be aware of the less obvious vulnerabilities that may exist. By regularly assessing and updating security protocols, network administrators can ensure that their networks remain secure and protected against potential threats.
In summary, while there is no foolproof method for network hardening, being aware of the less common holes can go a long way in preventing attacks. Network administrators must remain vigilant in their efforts to secure their networks, and stay up-to-date with the latest security trends and best practices. Ultimately, a proactive approach to network hardening can help to minimize the risk of data breaches, and ensure the safety and security of sensitive information.