In today’s digital era, cyber-security threats are increasing at an alarming rate. Man-in-the-middle attacks are one of the most common forms of cyber-attacks that can cause serious damage to an individual or organization. A man-in-the-middle attack (MITM) is when an attacker intercepts communications between two parties and gains access to confidential information. It can be used for a variety of malicious purposes such as stealing passwords, hijacking accounts, or even manipulating data. As such, it is essential for individuals and businesses to know how to protect against man-in-the-middle attacks.
In this article, we will discuss the different types of man-in-the-middle attacks, the risks associated with them, and the steps you can take to protect yourself and your organization against these types of attacks. We will discuss the importance of using strong passwords, two-factor authentication, and secure networks to protect against man-in-the-middle attacks. We will also cover the importance of regularly updating your security software and staying up-to-date on the latest security threats. By following these steps, you can protect yourself and your organization from the dangers of man-in-the-middle attacks.
- Use strong encryption protocols like SSL/TLS for secure data transmission.
- Use a secure authentication method such as two-factor authentication (2FA).
- Utilize a Virtual Private Network (VPN) to help protect data from MITM attacks.

What is a Man-in-the-Middle Attack?
A man-in-the-middle (MITM) attack is when an attacker intercepts communication between two parties and manipulates the data. This type of attack can be used to gain access to sensitive information, such as passwords, credit card numbers and other personal information. The attacker can also modify or delete the data being sent, making it difficult for the two parties to communicate securely.
How to Protect Against Man-in-the-Middle Attacks?
Use Encryption Protocols
Using encryption protocols is one of the most effective ways to protect against MITM attacks. Encryption is the process of converting data into an unreadable format that can only be decoded by the intended recipient. This makes it much more difficult for an attacker to read or modify the data being sent. Common encryption protocols include SSL/TLS, IPSec, and SSH.
Use Firewalls
Using firewalls is another effective way to protect against MITM attacks. Firewalls are used to block certain types of network traffic, such as malicious traffic. Firewalls can also be used to restrict access to certain websites or services, making it more difficult for an attacker to gain access. It is important to keep your firewall up to date to ensure that it is providing the most effective protection.
Install Security Software
Installing security software is another way to protect against MITM attacks. Security software can help identify and block malicious traffic, as well as detect any suspicious activity on your network. It is important to keep your security software up to date to ensure that it is providing the most effective protection.
Be Aware of Suspicious Activity
Being aware of suspicious activity is another way to protect against MITM attacks. Look out for any strange or unexpected emails, websites, or pop-ups. Report any suspicious activity to your IT department immediately. Be wary of any requests for personal information, such as passwords or credit card numbers.
Monitor Your Network Traffic
Monitoring your network traffic is another way to protect against MITM attacks. By monitoring your network traffic, you can identify any suspicious activity or traffic. It is important to monitor your network traffic regularly to ensure that it is not being used for malicious purposes.
Update Your Software Regularly
Updating your software regularly is another way to protect against MITM attacks. Outdated software can contain vulnerabilities that can be exploited by attackers. It is important to keep your software up to date to ensure that it is providing the most effective protection.
Use Two-Factor Authentication
Using two-factor authentication is another way to protect against MITM attacks. Two-factor authentication requires users to provide two pieces of information before being able to access a system. This can help to ensure that only authorized users can access the system, making it much more difficult for an attacker to gain access.
Limit Access to Sensitive Data
Limiting access to sensitive data is another way to protect against MITM attacks. By limiting access to sensitive data, you can make it much more difficult for an attacker to gain access. It is important to only give access to those who need it, and to ensure that the data is kept secure.
Frequently Asked Questions
The man-in-the-middle attack is a form of cyber attack in which a malicious actor intercepts and relays communications between two parties who believe they are communicating directly with each other. In this article, we discuss how to protect against man-in-the-middle attacks.
What Is a Man-in-the-Middle Attack?
A man-in-the-middle attack (MITM) is a type of cyber attack in which a malicious actor intercepts and relays communications between two parties who believe they are communicating directly with each other. The malicious actor is essentially “in the middle” of the two parties, able to monitor, alter, and relay communications between them. The attacker can intercept and steal sensitive information that is being exchanged, such as login credentials, bank account information, and credit card numbers.
What Are Some Common Types of Man-in-the-Middle Attacks?
Man-in-the-middle attacks come in many forms. Some of the most common types are:
• ARP spoofing, which is a type of attack in which a malicious actor sends falsified ARP (Address Resolution Protocol) messages over a local area network. This can be used to redirect traffic away from the intended destination and towards the attacker’s device.
• DNS spoofing, which is a type of attack in which a malicious actor sends falsified DNS (Domain Name System) responses to unsuspecting users. This can be used to redirect users to malicious websites or to intercept communications between the user and the intended destination.
• SSL stripping, which is a type of attack in which a malicious actor strips away the encryption (SSL) from a secure connection. This can be used to intercept and view communications between the user and the intended destination.
How Can I Protect Against Man-in-the-Middle Attacks?
There are several steps you can take to protect against man-in-the-middle attacks. First and foremost, you should ensure that all of your software is up to date with the latest security patches. This will help ensure that any known vulnerabilities are patched and make it more difficult for attackers to exploit them.
You should also use a reliable antivirus and antimalware program to detect and remove malicious programs. Additionally, make sure you are using a secure and encrypted connection when sending sensitive information online. This will help protect your data from being intercepted and viewed by malicious actors.
What Other Security Measures Can I Take?
In addition to the steps outlined above, there are several other security measures you can take to protect yourself against man-in-the-middle attacks. It is important to use strong, unique passwords for all of your accounts and to enable two-factor authentication whenever possible. Additionally, be sure to use a secure VPN when connecting to the internet. This will help protect your data from being intercepted and viewed by malicious actors.
Finally, it is important to be aware of phishing emails and other scams designed to steal your information. Be sure to do your research before clicking on any links or downloading any files from an unknown source. If something seems suspicious, it’s best to err on the side of caution.
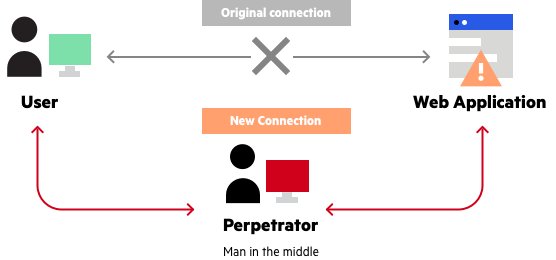
Man-in-the-middle attacks are a serious threat to the security of our online data and communications. It is essential that we take the necessary steps to protect ourselves against these attacks. By ensuring that the data and communications we send are encrypted, as well as verifying the identities of those we communicate with, we can greatly reduce our risk of being targeted by a man-in-the-middle attack. Additionally, being aware of the warning signs of a potential attack, such as strange requests for information or changes in communication patterns, can help us to identify and respond to such attacks quickly and effectively. By taking these steps, we can ensure the security of our online data and communications, and protect ourselves from the risks posed by man-in-the-middle attacks.