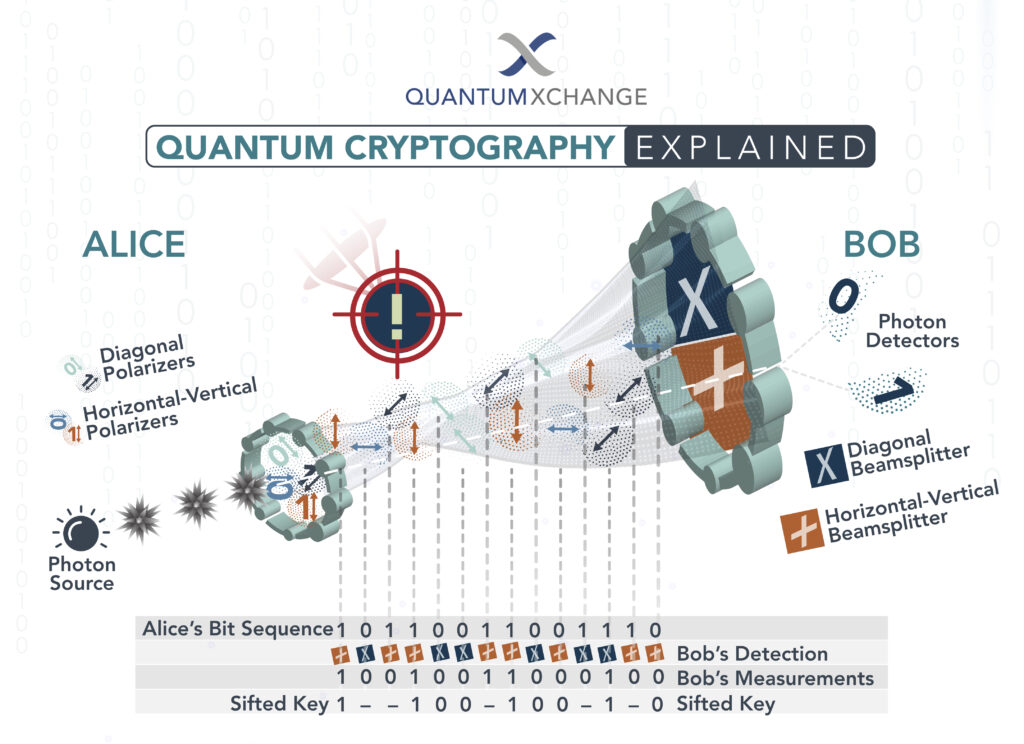
Post-quantum cryptography is a buzzword that has been gaining popularity in recent years. In the age of quantum computing, traditional cryptographic methods are considered vulnerable to attacks. Post-quantum cryptography aims to develop new cryptographic algorithms that are resistant to quantum computing-based attacks. The purpose of post-quantum cryptography is to secure the digital world against the threats posed by quantum computing.
As quantum computing is becoming more advanced, it poses a significant threat to the security of sensitive information. Cryptographic methods that have been considered secure for decades may become vulnerable to attacks with the advent of quantum computers. The purpose of post-quantum cryptography is to develop new cryptographic methods that are resistant to such attacks. This would ensure that sensitive information, such as financial transactions, personal data, and national security secrets, remain secure even in the age of quantum computing. In this article, we will explore the purpose of post-quantum cryptography in greater detail and examine the potential benefits of this innovative field.
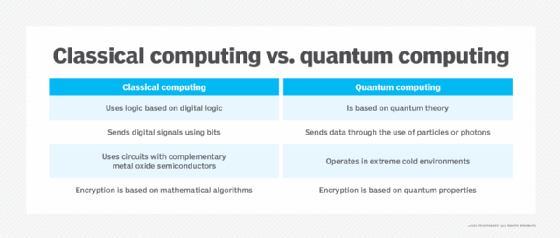
Purpose of Post Quantum Cryptography
Post quantum cryptography, also known as quantum-resistant cryptography, is an emerging cryptographic technology that is designed to protect data from attacks by quantum computers. Post quantum cryptography is different from traditional cryptography, which is vulnerable to attack by quantum computers. Post quantum cryptography is designed to be resistant to such attacks and provides an extra layer of security for data that may be vulnerable to attack.
Advantages
Post quantum cryptography offers a number of advantages compared to traditional cryptography. First, it provides improved security against attacks by quantum computers. Traditional cryptography is vulnerable to attack by quantum computers, while post quantum cryptography is designed to be resistant to such attacks. Additionally, post quantum cryptography is designed to be more efficient than traditional cryptography, allowing for faster encryption and decryption of data. Finally, post quantum cryptography is designed to be more secure against other types of attacks, such as brute force attacks, which can be used to gain access to data.
Post quantum cryptography also provides an additional layer of security for data that may be vulnerable to attack. By using post quantum cryptography, data can be encrypted in such a way that even if a quantum computer is used to gain access to the data, the data would remain secure. This is because post quantum cryptography is designed to be resistant to quantum computing attacks, and thus, the data would remain secure even in the case of a quantum computer attack.
Disadvantages
Post quantum cryptography also has some disadvantages. One of the main disadvantages is that it is not yet widely available. Post quantum cryptography is still in the early stages of development and is not yet widely used in the industry. Additionally, post quantum cryptography is not yet compatible with many existing systems and applications, which can limit its use. Finally, post quantum cryptography is more expensive than traditional cryptography, which can be a barrier to its use.
Post quantum cryptography is also a complex technology and requires a high level of expertise to implement. This means that it is not suitable for use by non-experts, as it can be difficult to understand and use. Additionally, post quantum cryptography is not the only solution to protecting data from quantum computer attacks, and other technologies may be more suitable for certain applications.
Frequently Asked Questions
Post Quantum Cryptography (PQC) is a form of cryptography that is designed to be secure against attacks by quantum computers. It is an actively researched field of cryptography, with the goal of developing technologies that will be secure even against potential quantum computing attacks.
What is the purpose of Post Quantum Cryptography?
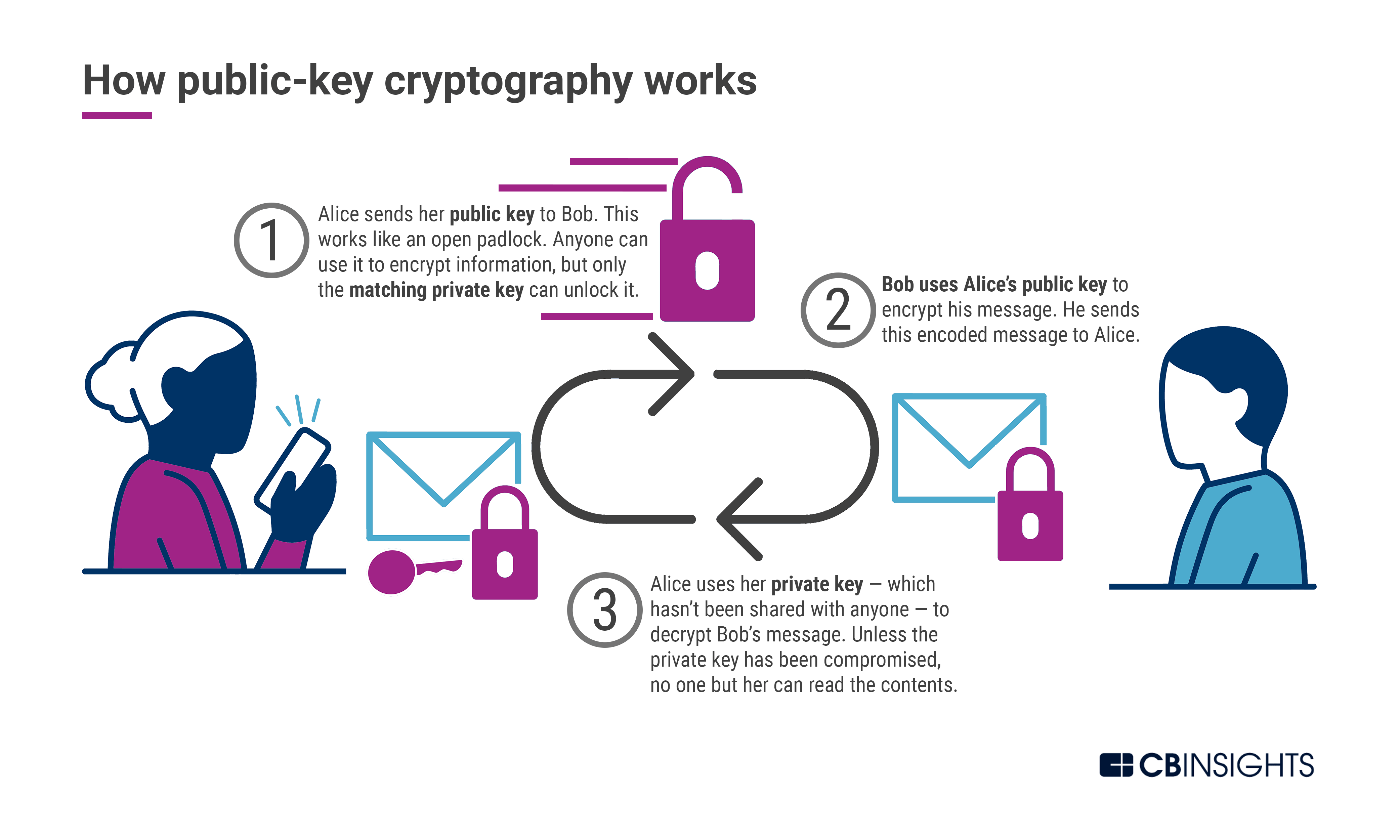
The purpose of Post Quantum Cryptography is to provide secure encryption even in the face of quantum computing attacks. Traditional encryption algorithms, such as the RSA algorithm, are vulnerable to attack by quantum computers, and thus PQC is needed in order to maintain security in the face of such attacks. PQC algorithms are designed to be resistant to quantum computing attacks, and thus provide a higher level of security than traditional encryption algorithms.
PQC algorithms are used in a variety of applications, including secure communication and data storage. PQC algorithms are also used for authentication and authorization, in order to provide strong security for online transactions. PQC is also used in government and military operations, in order to ensure the highest levels of security for sensitive communications. In short, PQC provides a secure solution to the challenges posed by quantum computing attacks.
What are the advantages of Post Quantum Cryptography?
The main advantage of Post Quantum Cryptography is its ability to provide secure encryption even in the face of quantum computing attacks. PQC algorithms are designed to be resistant to quantum computing attacks, and thus provide a higher level of security than traditional encryption algorithms. This means that even if a quantum computer is used to attack a system, the data will remain secure.
PQC algorithms are also designed to be efficient, and can be implemented quickly and securely. This means that PQC algorithms can be used in a variety of applications, allowing for secure communication and data storage. Furthermore, PQC algorithms are designed to be secure even against future advances in quantum computing technology, meaning that data encrypted using PQC algorithms will remain secure for many years to come.
What is the difference between Post Quantum Cryptography and traditional cryptography?
The main difference between Post Quantum Cryptography and traditional cryptography is that PQC algorithms are designed to be resistant to attack by quantum computers. Traditional cryptography algorithms, such as the RSA algorithm, are vulnerable to attack by quantum computers, and thus PQC is needed in order to maintain security in the face of such attacks. This means that data that is encrypted using PQC algorithms will remain secure even if a quantum computer is used to try and decrypt it.
In addition, traditional encryption algorithms are not designed to be secure against future advances in quantum computing technology, whereas PQC algorithms are. This means that data encrypted using PQC algorithms will remain secure for many years to come, even if quantum computing technology advances.
What are the limitations of Post Quantum Cryptography?
One of the main limitations of Post Quantum Cryptography is that it is not yet widely available. Currently, most encryption algorithms are based on traditional cryptography, and thus are not designed to be resistant to attack by quantum computers. As such, most systems are not currently using PQC algorithms, and thus are not secure against potential quantum computing attacks.
In addition, PQC algorithms are still relatively new, and as such have not been widely tested. This means that there is still a risk that PQC algorithms may be vulnerable to attack, and thus may not provide the level of security that is needed. As such, it is important to ensure that PQC algorithms are regularly tested and updated in order to ensure that they remain secure.
What is the future of Post Quantum Cryptography?
The future of Post Quantum Cryptography is very promising. As quantum computing technology continues to advance, PQC algorithms will become increasingly important in order to ensure that data remains secure. As such, PQC algorithms are likely to become increasingly common, with more and more systems using them in order to ensure secure communication and data storage.
In addition, as PQC algorithms become more widely used, they are likely to become more closely scrutinized. This means that PQC algorithms will be regularly tested and updated in order to ensure that they remain secure against quantum computers. As such, the future of PQC looks very bright, and it is likely to play an increasingly important role in the security of data in the future.
In conclusion, the purpose of post-quantum cryptography is to provide a secure method of data communication in the face of rapidly advancing quantum computing technology. With traditional cryptographic methods becoming increasingly vulnerable to attacks from quantum computers, post-quantum cryptography offers a solution that can withstand these threats. By using mathematical algorithms that are resistant to quantum computing, post-quantum cryptography ensures that sensitive information remains confidential and secure.
Furthermore, the development of post-quantum cryptography is crucial for the future of internet security as it will help to safeguard against potential threats posed by quantum computers. As quantum computing technology continues to improve, it’s important that we stay ahead of the game and implement security measures that can withstand these advancements. By investing in post-quantum cryptography, we can protect our digital infrastructure and ensure that our sensitive information remains safe from prying eyes. In essence, post-quantum cryptography is the key to securing our digital future.