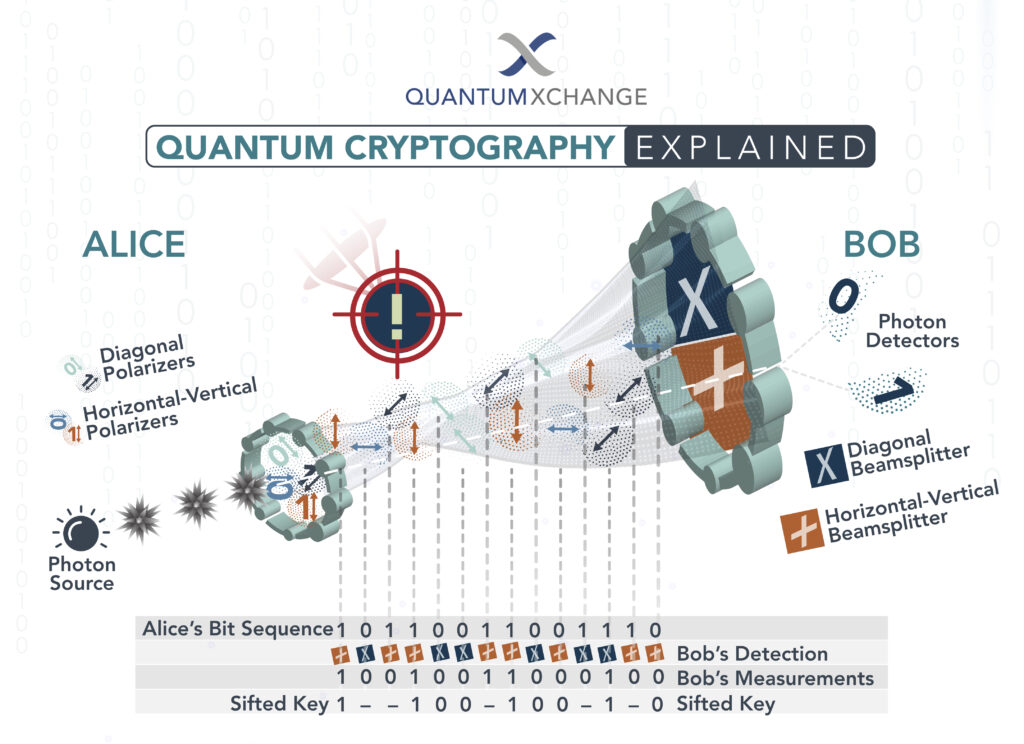
In the world of cybersecurity, post quantum cryptography has been touted as the future of secure communication. Its ability to safeguard sensitive information from prying eyes through the use of quantum-resistant algorithms has made it an attractive option for governments, businesses, and individuals alike. However, despite its promise, there are still a number of challenges that work against post quantum cryptography.
One of the main challenges is the fact that post quantum cryptography is still in its infancy. While there have been significant developments in the field, much of the research is still theoretical. This means that there are no standardized algorithms or protocols that have been widely accepted as secure. In addition, the development of quantum computers is progressing rapidly, and it is unclear whether the current post quantum cryptography algorithms will be able to withstand the power of these machines.
Post-quantum cryptography is designed to protect data against attacks from a quantum computer. It is built on algorithms that are believed to be secure against an attack by a quantum computer. To counter these algorithms, researchers have proposed various techniques, such as mathematical proofs, quantum-resistant algorithms, and quantum-proof protocols.
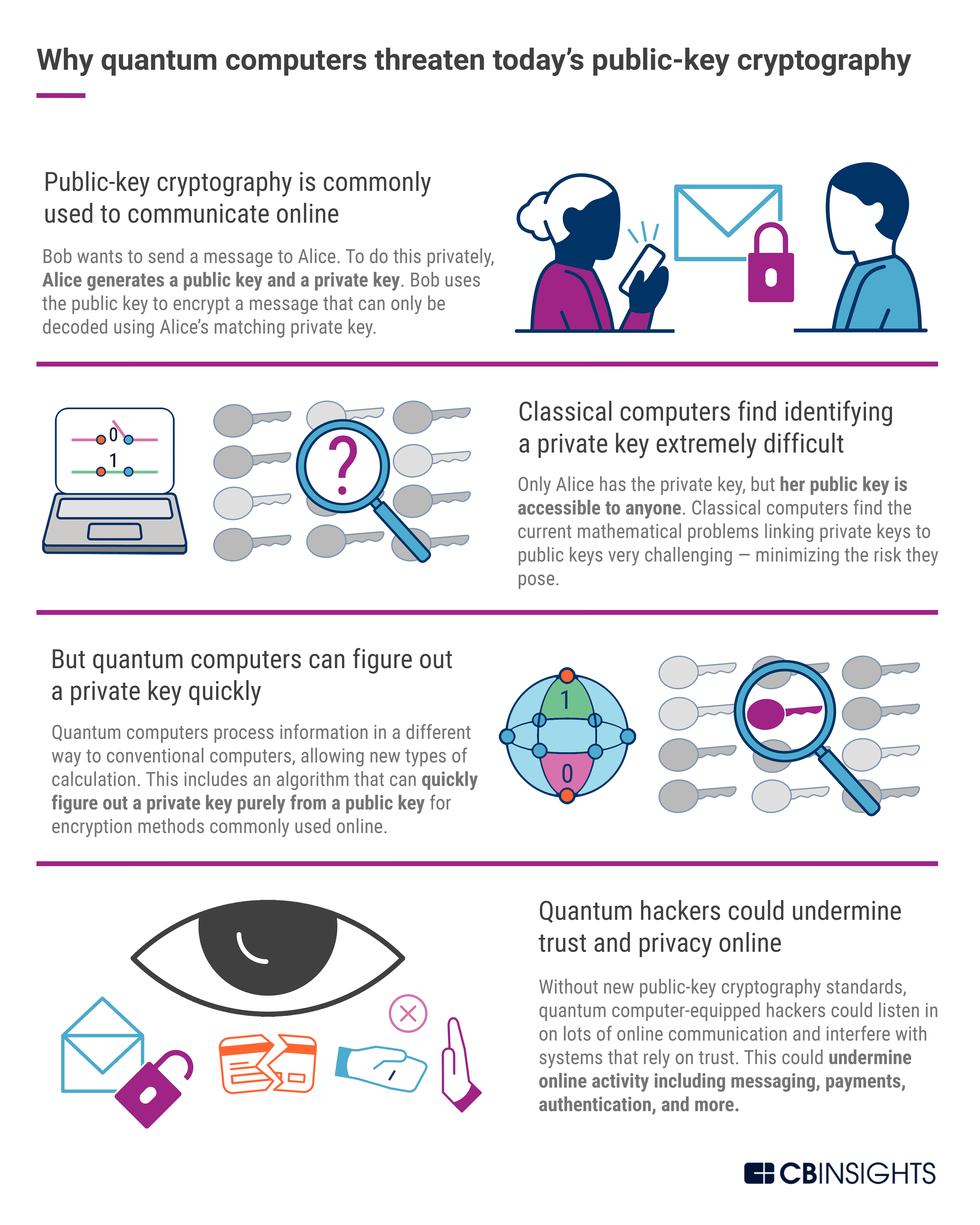
What is Post Quantum Cryptography?
Post Quantum Cryptography (PQC) is a form of encryption that is designed to withstand the power of quantum computers. It is an emerging field of cryptography which seeks to offer a secure way to store and transmit data even when confronted with the power of a quantum computer. PQC is based on the idea that a quantum computer could be used to break existing encryption schemes, such as the traditional RSA encryption. PQC seeks to provide security by using algorithms that are resistant to quantum computing attacks.
What Works Against Post Quantum Cryptography?
Quantum Computing
The most obvious threat to post quantum cryptography is quantum computing. Quantum computers are able to process data at a much faster rate than traditional computers, making them ideal for breaking existing encryption algorithms. As quantum computers become more powerful, it is likely that they will be able to break many of the encryption algorithms used by PQC. This means that PQC will need to be updated regularly to keep up with advances in quantum computing.
In addition to being able to break existing encryption schemes, quantum computers are also able to create new algorithms that are more secure than existing ones. This means that post quantum cryptography will need to be updated regularly to keep up with advances in quantum computing.
Mathematical Attacks
Another threat to post quantum cryptography is mathematical attacks. Mathematical attacks are used to exploit weaknesses in existing encryption schemes. For example, if a mathematical attack can be used to reduce the amount of time it takes to break an encryption algorithm, then post quantum cryptography is at risk. Mathematical attacks can also be used to create new algorithms that are more secure than existing ones.
Mathematical attacks can also be used to find weaknesses in existing algorithms. If an attacker is able to find a weakness in an algorithm, then they can use it to break the encryption. This means that post quantum cryptography will need to be updated regularly to keep up with advances in mathematics.
Side Channel Attacks
Side channel attacks are a type of attack that can be used to gain information about an encryption scheme. Side channel attacks use the physical characteristics of a system, such as the power consumption, to gain information about the system. Side channel attacks can be used to gain information about an encryption scheme, such as the key being used. This means that post quantum cryptography will need to be updated to protect against side channel attacks.
Side channel attacks can also be used to find weaknesses in existing algorithms. If an attacker is able to find a weakness in an algorithm, then they can use it to break the encryption. This means that post quantum cryptography will need to be updated regularly to keep up with advances in side channel attacks.
Frequently Asked Questions
Post-quantum cryptography is a form of cryptography that is designed to be secure against attack by quantum computers. It is a rapidly evolving field, and the best solutions are still being developed.
What is Post Quantum Cryptography?
Post quantum cryptography is a form of cryptography that is designed to be secure against attack by quantum computers. It is based on mathematical algorithms that are resistant to attack by quantum computers, which are computers that use the principles of quantum mechanics to perform calculations at speeds far beyond what is possible with traditional computers. Post quantum cryptography is an important step towards secure communication in the face of a future where quantum computing is a reality.
Post quantum cryptography relies on different algorithms than traditional cryptography. Traditional cryptographic algorithms use the difficulty of factoring large numbers as the basis for their security. Quantum computers, however, have the potential to quickly solve these problems and make these algorithms vulnerable. Post quantum cryptography instead relies on different mathematical problems that are not solvable by quantum computers, such as the learning with errors problem, code-based cryptography, or lattice-based cryptography.
How Does Post Quantum Cryptography Work?
Post quantum cryptography works by using algorithms that are resistant to attack by quantum computers. Instead of relying on the difficulty of factoring large numbers, these algorithms rely on other mathematical problems that are not solvable by quantum computers. These problems include the learning with errors problem, code-based cryptography, or lattice-based cryptography.
The algorithms used in post quantum cryptography are designed to be secure against attack by quantum computers, but they are not necessarily secure against attack by traditional computers. As such, post quantum cryptography is typically combined with traditional cryptography to provide the best of both worlds. This means that post quantum cryptography is used to protect the data from attack by quantum computers, while traditional cryptography is used to protect the data from attack by traditional computers.
What Are the Benefits of Post Quantum Cryptography?
The benefits of post quantum cryptography are twofold. First, it provides a level of security that is not available with traditional cryptography, as it is designed to be secure against attack by quantum computers. Second, it can be used in conjunction with traditional cryptography to provide the best of both worlds – the security of post quantum cryptography against attack by quantum computers, and the security of traditional cryptography against attack by traditional computers.
The use of post quantum cryptography is becoming increasingly important as quantum computing becomes more advanced. By using post quantum cryptography, organizations can ensure that their communications and data remain secure even in the face of a quantum computing attack. This is particularly important for industries such as finance and healthcare, which deal with sensitive data.
What Are the Drawbacks of Post Quantum Cryptography?
The main drawback of post quantum cryptography is that it is not as secure against attack by traditional computers as traditional cryptography is. While post quantum cryptography is designed to be secure against attack by quantum computers, it is not necessarily secure against attack by traditional computers. As such, it is typically used in combination with traditional cryptography to provide the best of both worlds.
Another drawback of post quantum cryptography is that it is relatively new and so there is still a lot of research and development that needs to be done in order to make it fully secure against attack by quantum computers. As such, it is important to keep up to date with the latest developments in post quantum cryptography in order to ensure that it remains secure.
What Are the Applications of Post Quantum Cryptography?
Post quantum cryptography has a wide range of applications, from secure communications to protecting data in the cloud. It is particularly important for industries such as finance and healthcare, which deal with sensitive data. Post quantum cryptography can also be used to protect the data of individuals and organizations from attack by quantum computers.
Post quantum cryptography can also be used to protect the communications of organizations and individuals, as it is designed to be secure against attack by quantum computers. This is particularly important for organizations that require secure communications, such as those in the military or government. Additionally, post quantum cryptography can be used to protect online transactions, such as those made with cryptocurrencies.
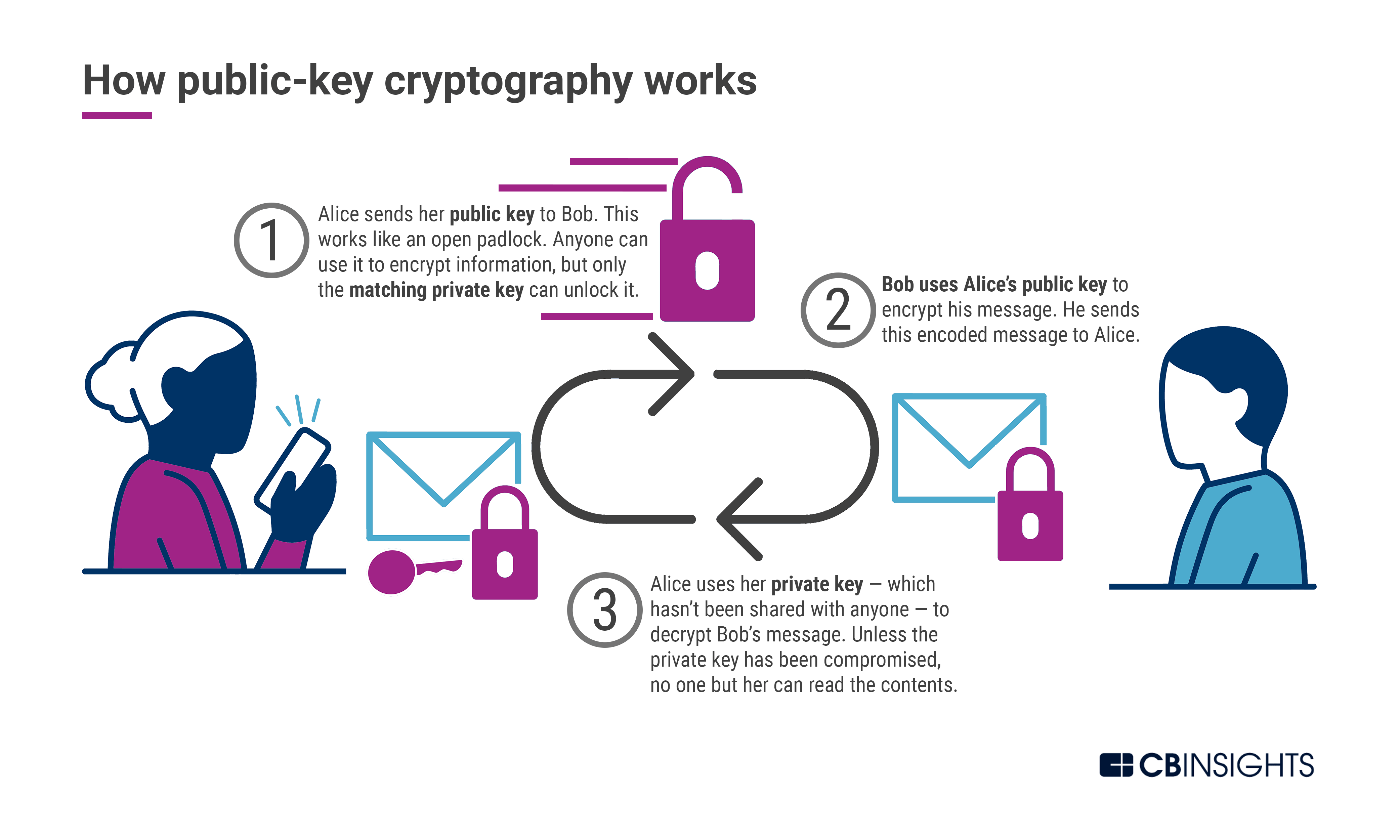
In conclusion, post-quantum cryptography is a promising solution to the security concerns posed by quantum computers. However, it is not without its challenges. The main factors that work against post-quantum cryptography include the lack of standardization, the high computational overhead, and the limited research and development in the field. Despite these challenges, researchers and industry experts are actively working towards developing and implementing post-quantum cryptography solutions that are secure and efficient.
As quantum computers continue to advance, it is essential that we address the potential security threats they pose. Post-quantum cryptography provides a promising solution to this problem, but it is still in its early stages of development. Therefore, it is crucial that we continue to invest in research and development in this field, work towards standardization, and collaborate with industry experts to ensure the widespread adoption of post-quantum cryptography. By doing so, we can ensure that our digital infrastructure remains secure and protected against potential threats posed by quantum computers.