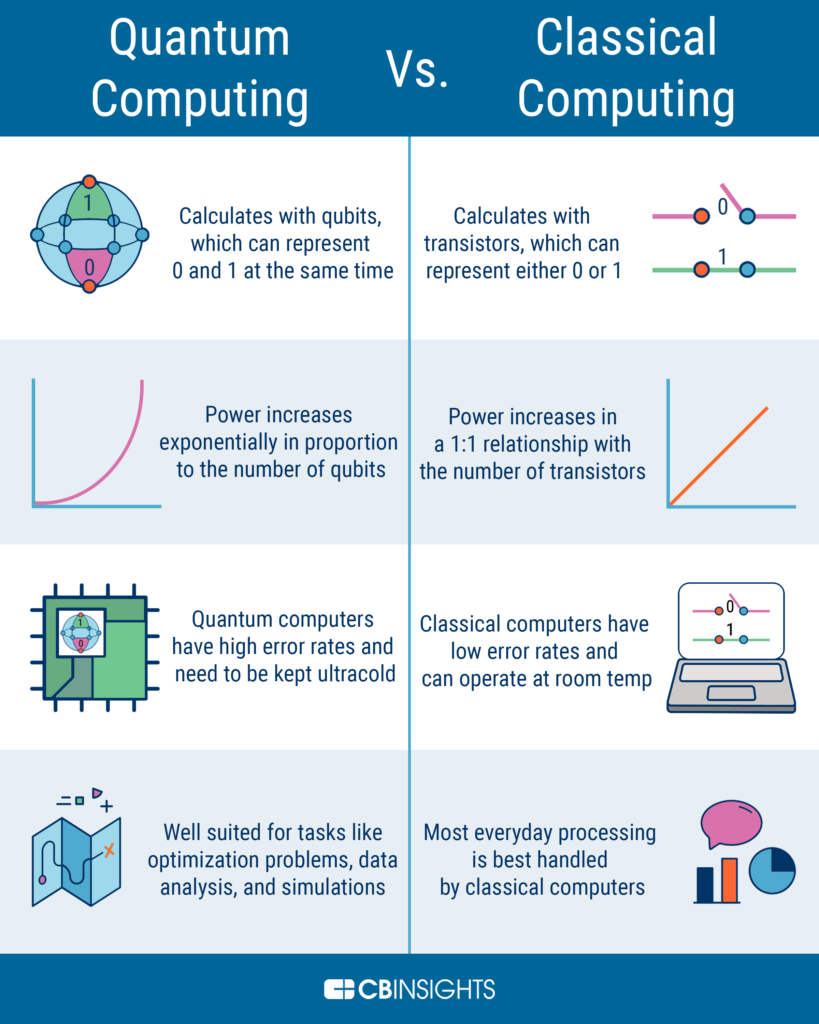
In the world of technology and data security, quantum key cryptography has emerged as a cutting-edge technique for securing sensitive information. This advanced form of cryptography offers a level of security that is virtually impossible to break, making it an ideal solution for businesses and organizations that require top-level data protection. While the concept of quantum key cryptography may seem intimidating at first, implementing it can be a straightforward process with the right tools and knowledge.
If you’re looking to implement quantum key cryptography on Quora, there are a few key steps you’ll need to follow. From understanding the basics of quantum technology to selecting the right software and encryption methods, this guide will provide you with everything you need to know to get started. Whether you’re a seasoned IT professional or a newcomer to the world of cryptography, this guide will help you take your data protection to the next level with quantum key cryptography.
- Step 1: Generate an entangled pair of photons
- Step 2: Exchange the entangled pair of photons between Alice and Bob
- Step 3: Generate a secret key using the entangled pair of photons
- Step 4: Exchange the secret key between Alice and Bob
- Step 5: Use the secret key to encrypt and decrypt messages between Alice and Bob
- Step 6: Periodically update the secret key
Introduction to Quantum Key Cryptography
Quantum key cryptography, also known as quantum cryptography, is an emerging field of cryptography that makes use of quantum mechanics to encrypt data. It is considered to be more secure than traditional cryptography, as it is resistant to hacking and other forms of attack. This form of cryptography is becoming increasingly popular due to its ability to protect sensitive data from unauthorized access.
How to Implement Quantum Key Cryptography
Step 1: Generate a Quantum Key
The first step in implementing quantum key cryptography is to generate a quantum key. This key is generated using quantum bits (qubits) and is used to encrypt the data. The key is generated using a quantum algorithm, which is used to generate a unique key that cannot be replicated by an unauthorized party. The key is then used to encrypt the data and is exchanged between two parties in order to decrypt the data.
Step 2: Exchange the Quantum Key
Once the quantum key has been generated, it must be exchanged between the two parties. This is done using a secure communication channel, such as the internet. The key is then used to encrypt the data and is exchanged between the two parties in order to decrypt the data. The key must be kept secure and is only used to encrypt and decrypt the data.
Step 3: Store the Quantum Key
Once the quantum key has been exchanged, it must be stored securely. This is done using a secure storage solution, such as a hardware-based key storage device. The key must be kept secure and is only used to encrypt and decrypt the data.
Step 4: Use the Quantum Key for Encryption
Once the quantum key has been stored securely, it can be used to encrypt data. This is done using a quantum algorithm, which is used to encrypt the data using the quantum key. The data is then encrypted and can only be decrypted using the quantum key.
Step 5: Exchange the Encrypted Data
Once the data has been encrypted, it must be exchanged between the two parties. This is done using a secure communication channel, such as the internet. The encrypted data is then exchanged between the two parties in order to decrypt the data. The data must be kept secure and is only used to encrypt and decrypt the data.
Step 6: Decrypt the Encrypted Data
Once the encrypted data has been exchanged, it must be decrypted using the quantum key. This is done using a quantum algorithm, which is used to decrypt the data using the quantum key. The data is then decrypted and can only be encrypted using the quantum key.
Step 7: Verify the Data
Once the data has been decrypted, it must be verified to ensure that it is authentic and has not been tampered with. This is done using a digital signature, which is used to verify the authenticity of the data. The data must be kept secure and is only used to verify the authenticity of the data.
Frequently Asked Questions about Quantum Key Cryptography
Quantum key cryptography is a secure communication technique that uses quantum mechanical properties to share a cryptographic key between two parties. The key is then used to encrypt and decrypt a message.
What is Quantum Key Cryptography?
Quantum key cryptography is a method of securely exchanging cryptographic keys between two parties. A quantum key is generated by combining quantum mechanical properties, such as the polarization of photons, with classical communication techniques. This key can then be used to encrypt and decrypt messages in a secure manner.
How does Quantum Key Cryptography work?
Quantum key cryptography works by sending a stream of photons through a quantum channel, such as a fiber optic cable. These photons have a certain polarization, which can either be vertical or horizontal. The two parties at either end of the channel measure the polarization of the photons and compare their results. If the polarization is the same, then the two parties have the same key. The key is then used to encrypt and decrypt messages.
What is the advantage of using Quantum Key Cryptography?
The main advantage of using quantum key cryptography is that it provides a secure method for exchanging encryption keys. This means that the key cannot be intercepted or deciphered by an eavesdropper. This is because of the fundamental laws of quantum mechanics, which prevent any observer from gathering information about the quantum state of a system without actually measuring it.
How secure is Quantum Key Cryptography?
Quantum key cryptography is considered to be one of the most secure forms of encryption. This is because of the inherent properties of quantum mechanics, which make it impossible for any observer to intercept or decipher the key without actually measuring it. This means that the key cannot be stolen or deciphered by an eavesdropper.
What are the limitations of Quantum Key Cryptography?
The main limitation of quantum key cryptography is that it requires a quantum channel, such as a fiber optic cable, in order to send the photons. This means that it is limited to point-to-point communication. Additionally, the amount of time required to generate a key can be quite long, which can make it difficult to use for real-time applications.
In conclusion, implementing quantum key cryptography is an ambitious yet essential step towards a more secure future in the digital age. By utilizing the fundamental principles of quantum mechanics, we can ensure that our sensitive information remains private and protected from potential cyber attacks. While the implementation process may seem daunting, with the right resources and guidance, anyone can successfully apply this technology to their systems.
Ultimately, the benefits of quantum key cryptography are undeniable. As technology continues to advance and our dependence on digital communication grows, it’s crucial that we prioritize the security and privacy of our data. By taking the necessary steps to implement quantum key cryptography, we can safeguard ourselves and our information from potential threats, and pave the way for a safer and more secure digital future.