In today’s digital age, it’s increasingly common for companies to offer virtual appliances as a way to deliver their software and services to their customers. These appliances can take many forms, from simple virtual machines to complex multi-server configurations. While virtual appliances offer a number of benefits, there are times when it makes sense to build a closed virtual appliance. But how do you know when it’s the right choice?
There are several factors to consider when deciding whether to build a closed virtual appliance. These include the level of control you want to maintain over the software and hardware configuration, the level of security you require, and the level of support you want to offer your customers. In this article, we’ll explore these factors in more detail and offer some guidance on when it makes sense to build a closed virtual appliance. So whether you’re a software developer, a system administrator, or a business owner, read on to learn more about when a closed virtual appliance might be the right choice for your organization.
When should you build a closed virtual appliance? It depends on the specific use case, but typically, you should build it when you need to securely manage, store, and access confidential data, or when you need to run a particular set of applications on a virtual machine. In some cases, you may even need to use a closed virtual appliance to run a specific business process or to maintain a certain level of control over the data and applications running on the virtual machine.
When Should We Build a Closed Virtual Appliance?
A closed virtual appliance is an application that runs on a virtual machine (VM). It can be used to run a variety of different applications, from web servers to databases. This type of virtual appliance is often used to provide a secure and reliable environment for applications that are sensitive or critical to the business.
What is a Closed Virtual Appliance?
A closed virtual appliance is a software application that is installed and configured to run on a virtual machine. This type of appliance is designed to provide a secure and reliable environment for running applications that are sensitive or critical to the business. The appliance is typically installed and configured with the required operating system and software, and can be deployed quickly and easily.
The appliance is typically hosted in a data center, and can be accessed by users through a web browser or other network connection. The appliance is also typically configured with features such as firewalls, intrusion detection systems, and other security measures to protect the data that is stored on the appliance.
When Should We Build a Closed Virtual Appliance?
Closed virtual appliances should be used for applications that require a secure and reliable environment, such as financial transactions, customer data, or confidential documents. These applications should be hosted on a closed virtual appliance to ensure that the data is kept secure and safe from external threats.
In addition, closed virtual appliances should be used when there is a need for high levels of scalability, performance, and reliability. The appliance should be able to scale up or down depending on the needs of the applications, and should be able to provide the necessary performance and reliability that the applications require.
It is also important to ensure that the appliance is properly configured to ensure that the data is kept safe and secure. The appliance should be configured with the appropriate security measures such as firewalls, intrusion detection systems, and other measures to ensure that the data is kept secure. Finally, the appliance should be regularly monitored to ensure that it is running optimally and that any changes to the configuration are properly implemented.
Frequently Asked Questions
Information technology teams use virtual appliances to create virtual machines that are used in a wide range of applications, from web hosting to data storage. A closed virtual appliance is a type of virtual appliance that is completely self-contained and requires no outside access for its operation.
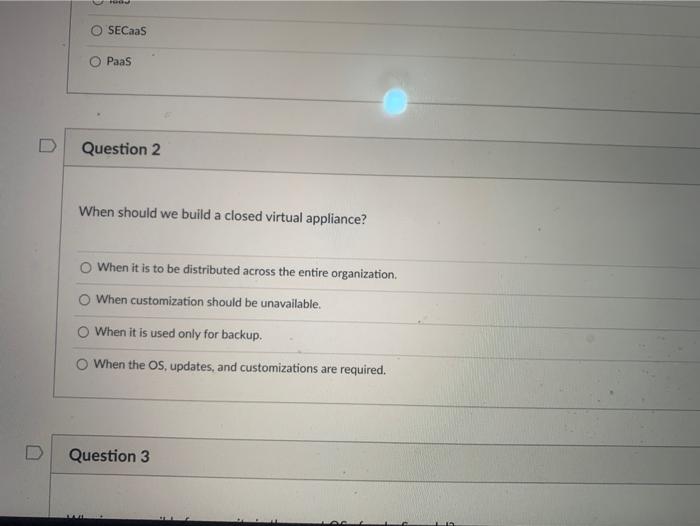
When should we build a closed virtual appliance?
A closed virtual appliance should be used when the system must be completely isolated from other networks and systems. This is often necessary for applications that require a high level of security, such as for military or government use. Additionally, closed virtual appliances are beneficial for applications that require a high degree of reliability, as there is no risk of external interference or tampering.
When building a closed virtual appliance, it is important to ensure that the system is fully hardened and secure. This includes setting up firewalls and other security measures, as well as regularly patching the system and monitoring it for changes. It is also important to ensure that all of the necessary services and applications are included, as well as adequately testing the system before deployment. Doing these steps will help ensure that the system is secure and reliable.
In conclusion, the decision to build a closed virtual appliance ultimately comes down to the specific needs and goals of the project at hand. If security and control are top priorities, a closed virtual appliance may be the best option. On the other hand, if flexibility and customization are more important, an open virtual appliance may be the better choice.
Regardless of the decision, it is important to carefully assess the requirements and potential risks before embarking on any virtual appliance project. With the right approach and careful consideration, a closed virtual appliance can provide a secure and efficient solution for a wide range of applications. As technology continues to evolve, it will be interesting to see how the role of virtual appliances in the IT landscape continues to develop and expand.

Hey! I realize this is somewhat off-topic but I needed to ask.
Does operating a well-established blog such ass yours take a massive
amount work? I am completely new to running a blog but I do write in my diary everyday.
I’d like to start a blog so I can share my own experience and views online.
Please let mme know if youu have any kind of suggestions or tips for
new aspiring blog owners. Thankyou!
https://foodrecipeai.com/