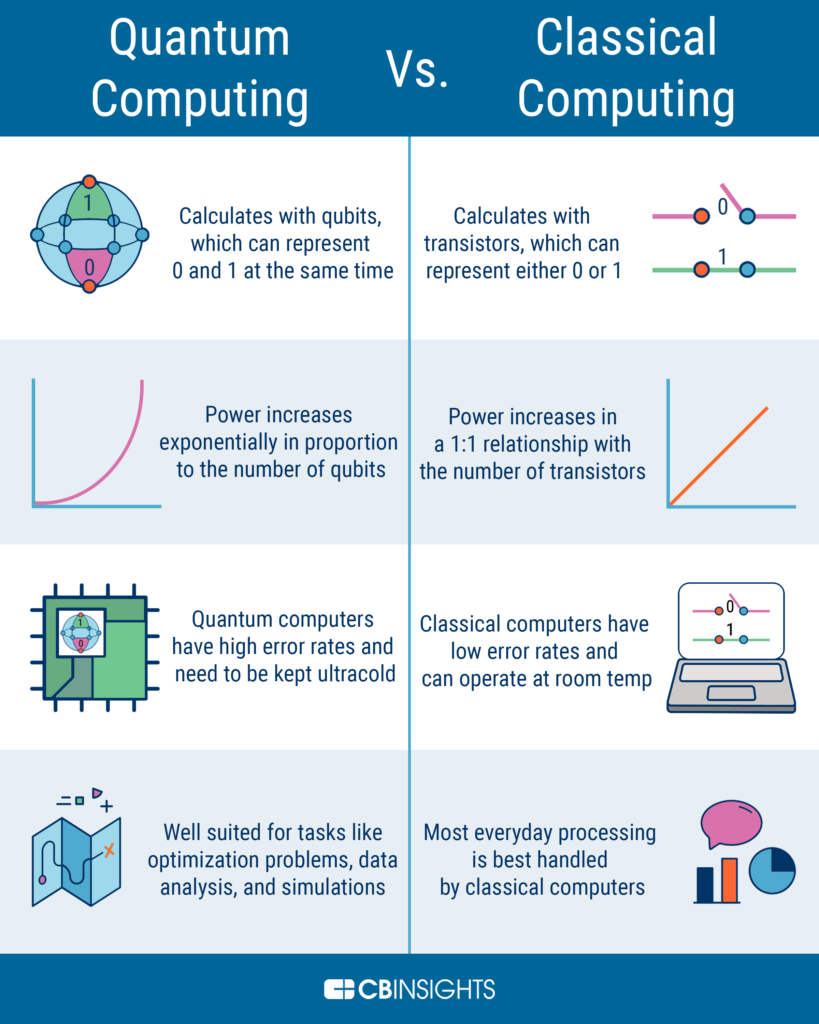
In today’s digital age, the security of private information has become increasingly important. Cryptography, the practice of secure communication in the presence of third parties, has been a critical tool in safeguarding sensitive data. However, with the advent of quantum computers, a new question has arisen: is cryptography still safe with quantum supremacy?
Quantum supremacy refers to the point at which quantum computers can perform calculations that are beyond the capabilities of classical computers. This breakthrough has significant implications for cryptography, as quantum computers could potentially break the encryption algorithms used to protect sensitive data. This presents a major challenge for the security industry, as the encryption methods that have been relied upon for decades may no longer be sufficient. In this article, we will explore the implications of quantum supremacy on cryptography and whether there are any solutions to this looming threat.
Yes, quantum supremacy makes cryptography more secure than ever before. The use of quantum computers allows for encryption keys to be generated faster and more securely than ever before. This means that data that was previously vulnerable to attacks can now be protected by quantum cryptography. Quantum computers are also able to quickly break existing codes, meaning that they are able to identify security vulnerabilities before they can be exploited.
Is Cryptography safe with Quantum Supremacy?
Cryptography is a technique used to make data secure and protected from unauthorized access. It is often used in the digital world to protect data, communications, and files. But is cryptography safe with quantum supremacy? Quantum supremacy is the term used to describe the ability of a quantum computer to solve problems that a classical computer cannot. With quantum computing, encryption techniques may become obsolete, leaving our data vulnerable to attacks. In this article, we will explore the security of cryptography in the face of quantum supremacy.
What is Quantum Supremacy?
Quantum supremacy is the term used to describe the ability of a quantum computer to solve problems that a classical computer cannot. It is the ability of a quantum computer to perform certain tasks much faster than a classical computer. Quantum computing is based on the principles of quantum mechanics, which allows for the manipulation of information at the atomic and subatomic level. This means that quantum computers can solve problems much faster than traditional computers.
Quantum computers are capable of performing calculations that are exponentially faster than classical computers. This means that they can solve problems much more quickly, making them a powerful tool for a variety of applications. In particular, they can be used to decrypt data that has been secured with traditional encryption techniques.
How is Cryptography Affected by Quantum Supremacy?
Cryptography is the process of encoding data so that it can be kept secure from unauthorized access. It is often used in the digital world to protect data, communications, and files. However, with quantum supremacy, encryption techniques may become obsolete, leaving our data vulnerable to attacks.
Most current encryption techniques rely on the fact that it is too difficult for a classical computer to try to solve the problem of breaking the encryption. However, with a quantum computer, it is much easier to solve such problems. This means that data encrypted using traditional methods could be easily decrypted using a quantum computer.
To combat this, researchers are working on developing quantum-resistant encryption algorithms. These algorithms are designed to be much harder to break using a quantum computer. However, research is still ongoing and it is unclear how effective these algorithms will be in the long run.
In addition, researchers are also looking into other methods of protecting data, such as quantum key distribution. This is a method of exchanging keys between two parties securely, using the principles of quantum mechanics. This could potentially be used to ensure secure communication between two parties, even if one of the parties is using a quantum computer.
Conclusion
Cryptography is an important tool for keeping data secure. However, with the emergence of quantum supremacy, traditional encryption techniques may become obsolete. This leaves our data vulnerable to attack from quantum computers. To combat this, researchers are developing quantum-resistant encryption algorithms and looking into other methods of protecting data, such as quantum key distribution.
While it is still too early to tell how effective these methods will be in the long run, it is clear that there is a need to develop new techniques to protect our data in the face of quantum computing.
Frequently Asked Questions about Cryptography and Quantum Supremacy
Cryptography is the practice of encrypting data in order to protect it from unauthorized access. Quantum supremacy is a term used to describe the potential of quantum computing to solve problems that are intractable with classical computing. This article answers some of the most commonly asked questions about cryptography and quantum supremacy.
Is Cryptography Safe with Quantum Supremacy?
Yes, cryptography is still safe with quantum supremacy. Even though quantum computing can solve certain problems that traditional computers cannot, it is not a threat to the security of cryptography. Cryptography is based on mathematical algorithms, and in order for a quantum computer to crack a cryptographic algorithm, it would have to break the underlying math of the algorithm, which is not possible.
The security of cryptography is dependent on the strength of the algorithm, and currently, there are no algorithms that are considered to be “quantum-proof”. However, research is ongoing to develop algorithms that are resistant to quantum computing. Some of these algorithms, such as lattice-based cryptography and post-quantum cryptography, are already in use.
What Are the Benefits of Quantum Supremacy?
The main benefit of quantum supremacy is that it can solve problems that traditional computers can’t. Quantum computing is based on quantum mechanics, and it uses the principles of quantum entanglement and superposition to process information. This enables it to solve problems much faster than traditional computers, and it can solve problems that are too complex for classical computers to handle.
For example, quantum computers can be used to quickly analyze large datasets and find patterns that are not visible to traditional computers. This makes them ideal for tasks such as machine learning, artificial intelligence, and quantum cryptography. Furthermore, quantum computing can be used to simulate quantum systems, which can help with the development of new materials and drugs.
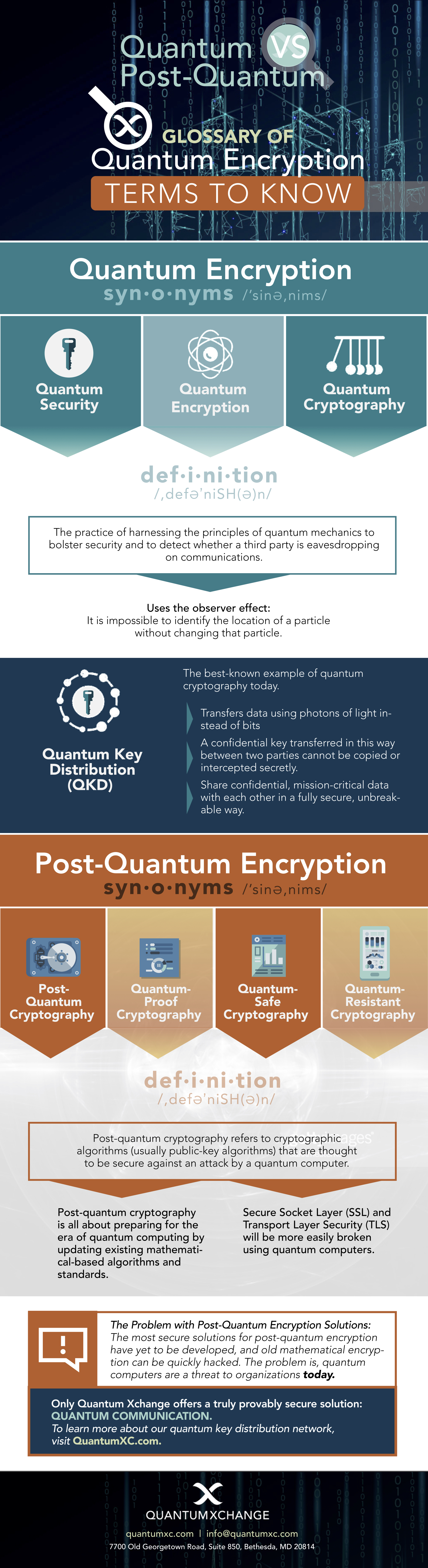
What Is Post-Quantum Cryptography?
Post-quantum cryptography is a type of cryptography that is designed to be resistant to quantum computing attacks. It is based on different mathematical algorithms than traditional cryptography and uses a different approach to security. For example, instead of relying on the difficulty of factoring large numbers, post-quantum cryptography relies on the difficulty of solving certain problems such as the shortest vector problem or the learning with errors problem.
In addition, post-quantum cryptography algorithms use larger key sizes than traditional algorithms, which makes them more secure against quantum computing attacks. Post-quantum cryptography is still in its early stages, but it is a promising approach to ensuring the security of data in a quantum computing world.
What Is Lattice-Based Cryptography?
Lattice-based cryptography is a type of cryptography that is based on the geometry of lattices. It uses mathematical algorithms that are based on the structure of lattices, which makes them resistant to certain types of quantum computing attacks.
Lattice-based cryptography is considered to be one of the most secure types of cryptography, and it is already being used in some applications. It has been adopted by the National Institute of Standards and Technology (NIST) as a potential post-quantum cryptographic algorithm, and it is being studied for potential use in other applications.
What Is Quantum Cryptography?
Quantum cryptography is a type of cryptography that is based on the principles of quantum mechanics. It uses quantum systems such as photons or atoms to securely transmit information, and it is considered to be one of the most secure forms of cryptography.
The main advantage of quantum cryptography is that it is impossible to eavesdrop on the communication without being detected. This is because any attempt to intercept the information would cause a disturbance in the quantum system, which would alert the sender and the receiver of the communication.
Quantum cryptography has already been used in some applications, such as financial transactions, and it is expected to become more widely used in the future.

Quantum Computing impact on Cryptography
In conclusion, the development of quantum computers has raised concerns about the safety of cryptography. However, it is important to note that the field of cryptography is constantly evolving and adapting to new technologies. While quantum supremacy could potentially break some of the existing cryptographic algorithms, researchers are already working on developing new ones that are resistant to quantum attacks.
Furthermore, the development of quantum computers also presents new opportunities for cryptography. Quantum cryptography, which uses the principles of quantum mechanics to secure information, has the potential to provide even stronger security than traditional cryptographic methods. Ultimately, it is up to the cryptography community to stay ahead of the curve and continue to innovate in order to ensure the safety and security of our digital world.