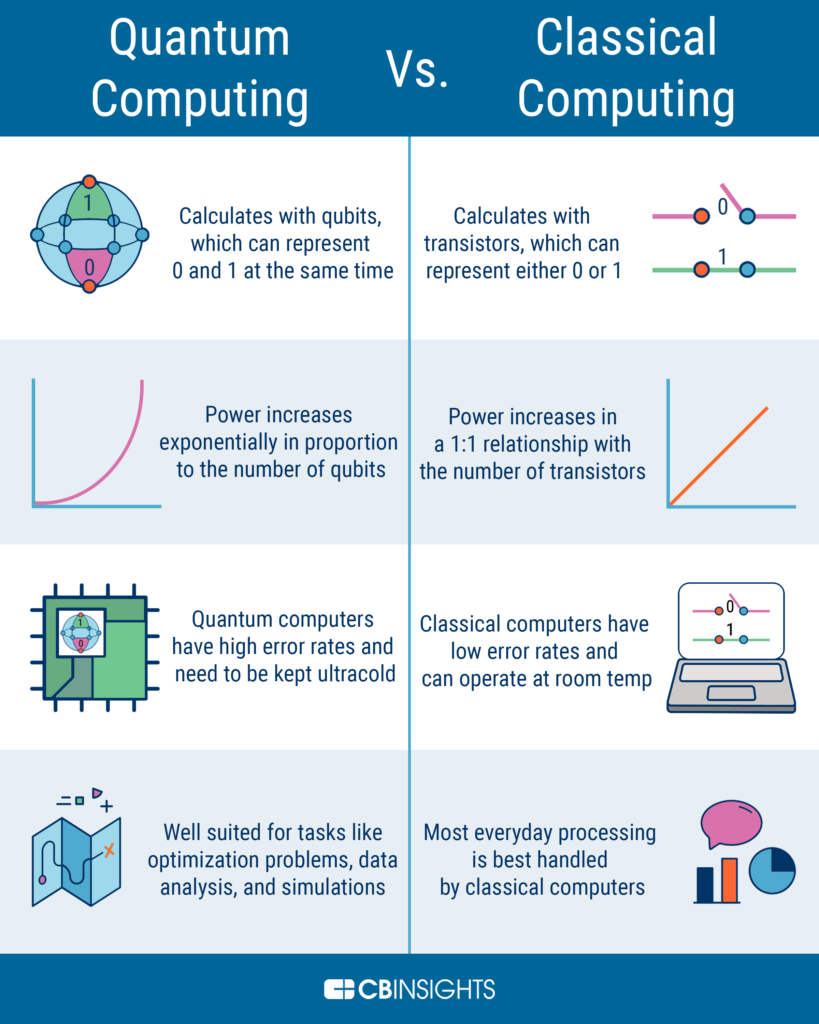
As technology continues to rapidly advance, the threat of cyber attacks becomes increasingly prevalent. One type of attack that has gained attention in recent years is quantum computing attacks, which can easily break through traditional encryption methods. This has led to the development of quantum secure algorithms, which are specifically designed to resist quantum computing attacks. However, not all algorithms are created equal, and some are still vulnerable to quantum threats.
In this article, we will explore the question of which algorithms are not quantum secure. We will discuss the various types of algorithms and their strengths and weaknesses when it comes to quantum computing attacks. Understanding the limitations of different algorithms is important for organizations and individuals who want to ensure the security of their sensitive information in an age where cyber threats are becoming more sophisticated and prevalent.
Non-quantum secure algorithms are those which are not resistant to quantum computing attacks. These include DES, 3DES, RSA, ECC, Blowfish, Twofish, and many other symmetric and asymmetric encryption algorithms. The most secure quantum-safe algorithms are those based on quantum key distribution and quantum random number generation.

Which Algorithms Are Not Quantum Secure?
Quantum computers are revolutionizing the world of computing, allowing for much faster and more efficient solutions to complex problems. However, one of the downsides of quantum computing is that some of the algorithms used in traditional computing are not quantum secure. This article will explore which algorithms are not quantum secure and how they can be made more secure.
What is Quantum Computing?
Quantum computing is the use of quantum mechanical phenomena such as superposition and entanglement to perform computation. This type of computing is much faster than traditional computing and can solve problems that traditional computers can’t. However, quantum computing is still in its infancy and many of the algorithms used in traditional computing are not quantum secure.
Which Algorithms Are Not Quantum Secure?
Many of the algorithms used for encryption, authentication, and digital signatures are not quantum secure. This includes algorithms such as RSA, Diffie-Hellman, and Elliptic Curve Cryptography. These algorithms use mathematical operations that can be easily broken by quantum computers. As a result, data encrypted with these algorithms can be easily stolen or modified without the user’s knowledge.
In addition, many of the algorithms used for authentication and digital signatures are not quantum secure. These algorithms include HMAC, SHA-1, SHA-2, and MD5. These algorithms use mathematical operations that can be easily broken by quantum computers. As a result, data signed with these algorithms can be easily forged or modified without the user’s knowledge.
How Can Algorithms Be Made Quantum Secure?
One way to make algorithms quantum secure is to use quantum-resistant algorithms. These algorithms use mathematical operations that are resistant to quantum computing attacks. Examples of quantum-resistant algorithms include Lamport Signatures, Post-Quantum Cryptography, and Hash-Based Signatures. These algorithms can be used to encrypt data and sign digital signatures in a way that is secure against quantum computers.
Another way to make algorithms quantum secure is to use quantum computing itself. By using quantum computing, algorithms can be designed that are resistant to quantum computing attacks. Examples of quantum-secure algorithms include Grover’s Algorithm, Shor’s Algorithm, and Quantum Key Distribution. These algorithms can be used to securely encrypt data and sign digital signatures in a way that is secure against quantum computers.
What Are the Benefits of Quantum Secure Algorithms?
The use of quantum secure algorithms provides several benefits. First, it ensures that data is secure against quantum computing attacks. This makes it much more difficult for adversaries to steal or modify data without the user’s knowledge. Secondly, it makes it much more difficult for adversaries to forge digital signatures. This helps to ensure the authenticity and integrity of digital signatures. Lastly, it provides a way to securely communicate data over long distances without the need for a physical connection.
Conclusion
In conclusion, many of the algorithms used for encryption, authentication, and digital signatures are not quantum secure. To make algorithms quantum secure, it is necessary to use quantum-resistant algorithms or quantum computing itself. Using quantum secure algorithms provides several benefits, including increased security, authenticity, and integrity of digital signatures, as well as the ability to securely communicate data over long distances.
Frequently Asked Questions
A quantum secure algorithm is an algorithm that is resistant to attack from a quantum computer. In this article we discuss which algorithms are not quantum secure.
What is a quantum secure algorithm?
A quantum secure algorithm is an algorithm which is resistant to attack from a quantum computer. It is a cryptographic algorithm which is designed to be resistant to attack from a quantum computer, which can break traditional algorithms. Quantum secure algorithms are designed to be resistant to attacks from a quantum computer and can be used in place of traditional algorithms to provide a higher level of security.
What algorithms are not quantum secure?
Traditional algorithms, such as RSA and Elliptic Curve Cryptography (ECC), are not quantum secure. These algorithms are vulnerable to attack by a quantum computer and should not be used for sensitive data. Additionally, symmetric algorithms, such as AES and 3DES, are also not quantum secure, as they can be broken by a quantum computer.
What algorithms are quantum secure?
Quantum secure algorithms, such as those based on post-quantum cryptography, are designed to be resistant to attack from a quantum computer. These algorithms include lattice-based cryptography, such as NTRUEncrypt, code-based cryptography, such as McEliece, and hash-based cryptography, such as SHA-3.
How do I know if an algorithm is quantum secure?
The best way to determine if an algorithm is quantum secure is to consult a reputable source. The National Institute of Standards and Technology (NIST) is currently running a competition to select a post-quantum cryptography algorithm for use in the US government. The competition is open to submissions from private companies and researchers, and the winning algorithm will be selected based on security and performance.
What is the best way to protect data against quantum attacks?
The best way to protect data against quantum attacks is to use a quantum secure algorithm. As mentioned above, NIST is currently running a competition to select a post-quantum cryptography algorithm for use in the US government. Additionally, there are other quantum secure algorithms available, such as those based on lattice-based cryptography, code-based cryptography, and hash-based cryptography. For best results, it is important to use an algorithm that is updated regularly and tested for security. Additionally, it is important to use strong key sizes and keep keys secure.

NIST Announces First Four Quantum-Resistant Cryptographic Algorithms
In conclusion, the world of cryptography is constantly evolving, and the advent of quantum computing is set to revolutionize the field. While quantum computers offer unprecedented computational power, they also pose a significant threat to traditional cryptographic algorithms. As such, it is crucial for individuals and organizations to be aware of which algorithms are vulnerable to quantum attacks and to take the necessary steps to secure their sensitive data.
In the coming years, it is likely that we will see a shift towards quantum-safe cryptography, as individuals and organizations alike begin to recognize the importance of protecting their data from the threats posed by quantum computers. While the transition may be challenging, it is ultimately necessary for the continued security of our digital world. By staying informed about the latest developments in the field, we can take proactive steps to safeguard our data and ensure that our sensitive information remains secure in the face of growing technological advancements.