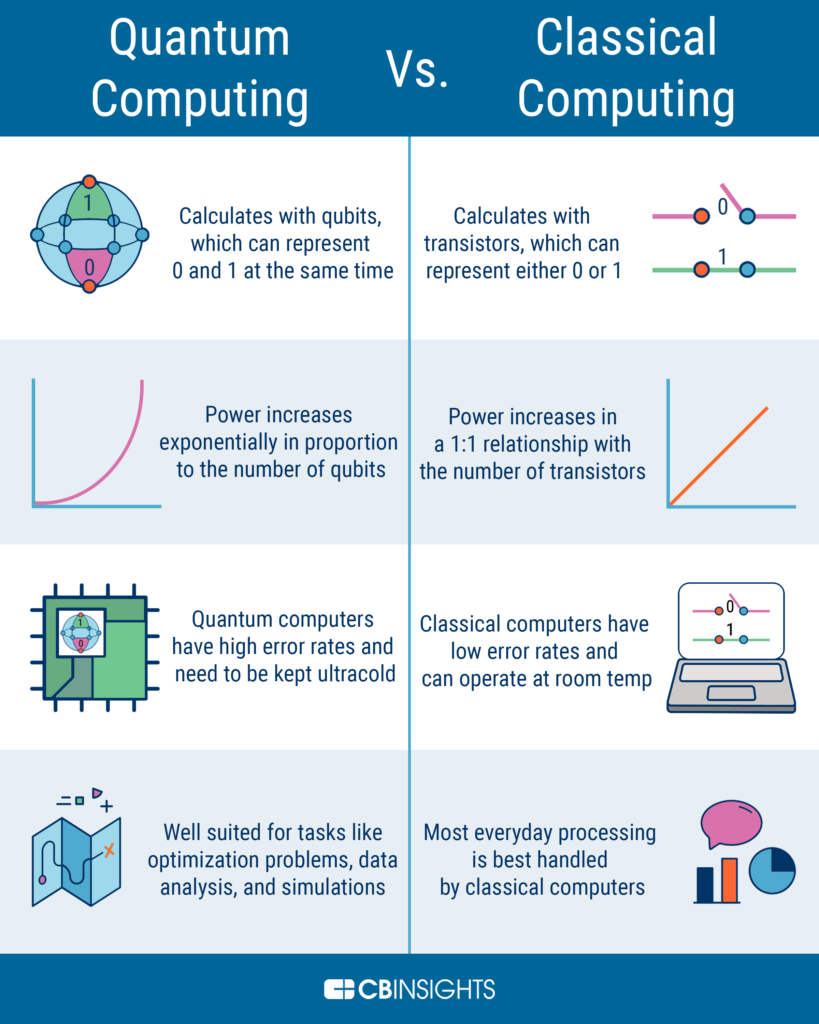
In the world of cryptography, the need for secure communication has never been more pressing. With advancements in technology and the rise of quantum computing, traditional encryption methods are no longer sufficient. As a result, researchers have turned to a new approach: elliptic curve cryptography. But the question remains, is it quantum proof?
Elliptic curve cryptography is a form of public key encryption that relies on the difficulty of solving mathematical problems related to elliptic curves. It is widely used in modern cryptography and has been praised for its efficiency and security. However, with the advent of quantum computing, there is growing concern that elliptic curve cryptography may no longer be a viable solution. In this article, we will explore the capabilities of quantum computing and examine whether or not elliptic curve cryptography can withstand its power.
Elliptic Curve Cryptography (ECC) is not currently quantum proof. However, it is believed that ECC can be made quantum-resistant by increasing the key size and using larger parameters. Currently, there are several proposals for making ECC quantum-resistant, but none of them have been fully implemented yet.

What is Elliptic Curve Cryptography?
Elliptic Curve Cryptography (ECC) is a type of public-key cryptography which is based on the algebraic structure of elliptic curves over finite fields. It is used to securely transfer data, especially in applications such as online banking, digital signatures, and authentication. ECC is considered to be more efficient and secure than other forms of cryptography.
How Does Elliptic Curve Cryptography Work?
Elliptic Curve Cryptography works by using the properties of an elliptic curve, which is a type of mathematical equation. The equation is used to generate points on the curve, which are then used to generate keys. The public key is used to encrypt data, while the private key is used to decrypt it. The keys are generated in such a way that it is impossible to derive the private key from the public key.
Is Elliptic Curve Cryptography Quantum Proof?
The security of Elliptic Curve Cryptography is based on the difficulty of solving the Elliptic Curve Discrete Logarithm Problem (ECDLP). This problem is based on the assumption that it is difficult to compute discrete logarithms in a finite field. However, with the advent of quantum computers, it is now possible to solve ECDLP in polynomial time, which would make ECC vulnerable to attack.
In order to make Elliptic Curve Cryptography quantum proof, it must be combined with other cryptographic algorithms. One such algorithm is post-quantum cryptography, which is based on mathematical problems that are believed to be resistant to quantum attacks. Post-quantum cryptography can be used in combination with ECC to provide a secure encryption system that is resistant to quantum attacks.
Advantages and Disadvantages of Elliptic Curve Cryptography
One of the main advantages of Elliptic Curve Cryptography is that it is more efficient than other forms of cryptography, requiring smaller key sizes for the same level of security. This makes it the ideal choice for applications where data needs to be transferred quickly. Additionally, ECC is considered to be more secure than other forms of cryptography, making it ideal for applications where security is paramount.
On the other hand, Elliptic Curve Cryptography is vulnerable to quantum attacks and must be combined with other forms of cryptography in order to be quantum proof. Additionally, it is more difficult to implement than other forms of cryptography, which can be a challenge for developers.
Frequently Asked Questions
Elliptic Curve Cryptography (ECC) is a mathematical cryptography tool used to secure digital data and communications. It is quantum proof, meaning that it is resistant to attacks from quantum computers.
What is elliptic curve cryptography?
Elliptic Curve Cryptography (ECC) is a type of encryption used to secure digital data and communications. It provides a higher level of security than traditional encryption methods by using a mathematical curve to generate a unique key. The curve is defined by a set of mathematical equations, which makes it difficult to crack.
ECC is used in a variety of applications, including secure communications, digital signatures, and key exchange. It is also used to protect online financial transactions and to secure sensitive data stored on servers.
Why is elliptic curve cryptography quantum proof?
ECC is quantum proof because it is resistant to attacks from quantum computers. Quantum computers are powerful enough to break traditional encryption methods, but ECC is designed to be resistant to these attacks. This is because ECC relies on the difficulty of solving a mathematical equation, which is difficult for quantum computers to do.
Additionally, ECC generates unique keys for each transaction, which makes it difficult for hackers to break the encryption. The keys are generated using a random number generator, which ensures that each key is unique and unpredictable. This makes it very difficult for hackers to figure out the key and gain access to the data.
What are the advantages of elliptic curve cryptography?
One of the main advantages of ECC is that it is quantum proof and therefore resistant to attacks from quantum computers. Additionally, ECC is more efficient than traditional encryption methods, which means that it can be used to secure more data with less computing power. This makes it ideal for applications that require a high level of encryption, such as online banking and secure communications.
ECC is also more secure than traditional encryption methods because it generates unique keys for each transaction. This makes it difficult for hackers to gain access to the data, as they would need to figure out the key in order to decrypt the data.
What are the disadvantages of elliptic curve cryptography?
One of the main disadvantages of ECC is that it is more difficult to implement than traditional encryption methods. This is due to the complexity of the mathematical equations used to generate the keys. Additionally, ECC is more computationally expensive than traditional encryption methods, which can make it less attractive for applications that require low latency or low power consumption.
Additionally, ECC is vulnerable to certain types of attacks, such as side-channel attacks. Side-channel attacks involve analyzing the data being transmitted in order to gain access to the data. However, these attacks can be mitigated by using countermeasures, such as randomizing the data being transmitted.
What are the applications of elliptic curve cryptography?
ECC is used in a variety of applications, including secure communications, digital signatures, and key exchange. It is also used to protect online financial transactions and to secure sensitive data stored on servers.
Additionally, ECC is used in the medical field to secure patient data and to protect medical devices from malicious attacks. Additionally, ECC is used in the automotive industry to secure vehicle data and communications. Finally, ECC is used in the military to secure sensitive communications and data.
Elliptic Curve and Quantum Cryptography – CompTIA Security+ SY0-401: 6.1
In conclusion, the debate on whether elliptic curve cryptography is quantum proof is still ongoing. While quantum computers pose a significant threat to traditional cryptographic systems, recent research has shown that ECC can still be secure against quantum attacks if the appropriate key sizes and algorithms are used. However, as quantum technology continues to advance, it is essential for the cryptographic community to remain vigilant and adapt their techniques accordingly.
It is important to note that quantum-proof cryptography is not only a matter of theoretical research but a practical necessity in today’s world. The security of our online transactions, data storage, and communication depends on the strength of cryptographic algorithms. As quantum computers become more powerful, the need for quantum-proof cryptography will only increase. Therefore, it is crucial for researchers, businesses, and governments to work together to develop and implement secure cryptographic systems that can withstand the challenges of the quantum era.