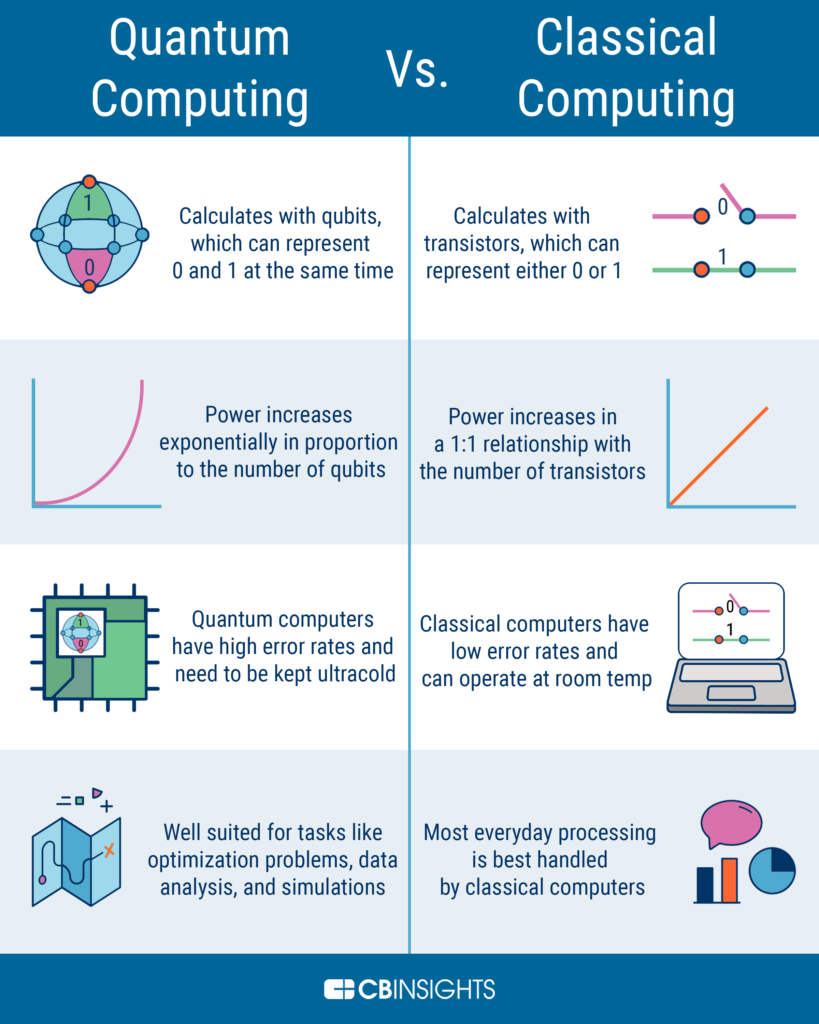
In today’s digital age, cryptography has become an essential part of our daily lives as we rely heavily on secure communication channels for everything from online banking to confidential business transactions. However, with the emergence of quantum computers, the security of traditional cryptographic methods has come under question. One of the most widely used cryptographic algorithms is the Hash-based Message Authentication Code (HMAC), but the question remains: is this algorithm quantum-resistant?
HMAC is a cryptographic algorithm that uses a cryptographic hash function to authenticate messages. It is widely used in internet security protocols such as SSL/TLS, IPsec, and SSH, among others. However, with the advancement of quantum computers, there is a growing concern that traditional cryptographic methods may no longer be secure. In this article, we will explore the question of whether HMAC is quantum-resistant and what steps can be taken to ensure the security of our digital communication in the quantum computing era.

What is Hase Base Cryptography?
Hase base cryptography is a type of cryptographic algorithm that uses the principles of hashing to encrypt data. It is an important part of many secure communication protocols, as it is designed to produce a unique, cryptographic fingerprint for any given set of data. This allows for the data to be securely transmitted over an unreliable medium, such as the internet. Hase base cryptography is also used for authentication, digital signatures, and data integrity.
Hase base cryptography is based on a mathematical hash function, which is a one-way mathematical algorithm. This algorithm takes a given set of data, such as a string of characters, and returns a unique, fixed-length string of characters. This fixed-length string is known as the hash value or digest. Each time the hash function is used on the same set of data, the same hash value will be produced. If the data is changed in any way, the hash value will also change. This makes it difficult for malicious actors to alter data without alerting the receiver.
Is Hase Base Cryptography Quantum Resistant?
Hase base cryptography is not considered to be quantum resistant. This is because the hash functions that are used in Hase base cryptography are not designed to be secure against quantum computing algorithms. As quantum computing becomes more powerful, it is possible that these algorithms will be able to reverse-engineer the hash values, allowing malicious actors to access the encrypted data.
The security of Hase base cryptography can be improved by increasing the length of the hash values, as this makes it more difficult for quantum computers to reverse-engineer the data. However, this also increases the time and resources needed to generate and verify the hash values. As such, it is not recommended to rely solely on Hase base cryptography for secure communication, as it may not be sufficient to protect against quantum computing attacks.
What Are Some Alternatives to Hase Base Cryptography?
There are a number of alternative cryptographic algorithms that are designed to be quantum resistant. Post-quantum cryptography (PQC) is a type of cryptography that is specifically designed to be resistant to quantum computing attacks. PQC algorithms use mathematical problems that are difficult to solve with quantum computers, such as the Learning with Errors (LWE) problem.
Other quantum-resistant algorithms include lattice-based cryptography, code-based cryptography, and multivariate cryptography. All of these algorithms use mathematical problems that are difficult for quantum computers to solve, making them more secure than Hase base cryptography.
How Can I Implement Quantum-Resistant Cryptography?
If you are looking to secure your data against quantum computing attacks, it is recommended to use one or more of the quantum-resistant algorithms discussed above. However, these algorithms are relatively new, and may not be supported by all applications. As such, it is important to research the different algorithms and choose one that is supported by the software you are using.
Once you have selected an algorithm, it is important to use a strong key to encrypt the data. This key should be at least 256 bits in length and should be generated using a cryptographically secure random number generator. It is also important to regularly change the key, as this will reduce the chances of a malicious actor guessing the key.
Finally, it is important to keep your data secure at all times. This means encrypting the data before it is sent over the internet, and ensuring that it is stored securely on your computer or server. It is also important to use secure communication protocols, such as TLS or IPSec, to ensure that the data is not intercepted while in transit.
Frequently Asked Questions About Hase Base Cryptography Quantum Resistant
Hase base cryptography quantum resistant is a type of encryption system that is designed to be resistant to attacks from quantum computers. It is considered to be one of the most secure forms of encryption available today.
What Is Hase Base Cryptography Quantum Resistant?
Hase base cryptography quantum resistant is an advanced form of encryption that is designed to be resistant to attacks from quantum computers. This type of encryption system utilizes a combination of public and private key cryptography, as well as a form of post-quantum cryptography, to create a very secure encryption system. The system is designed to be more secure than traditional encryption systems, as it is able to resist the computing power of quantum computers.
Why Is Hase Base Cryptography Quantum Resistant Necessary?
Hase base cryptography quantum resistant is necessary because of the threat posed by quantum computers. Quantum computers are able to process and store large amounts of data at an incredibly fast rate and are able to solve problems that traditional computers are unable to. This makes them a threat to traditional encryption methods, as they could potentially be used to crack an encryption key. Hase base cryptography quantum resistant is designed to be resistant to these attacks, allowing for more secure communications and data storage.
How Does Hase Base Cryptography Quantum Resistant Work?
Hase base cryptography quantum resistant works by using a combination of public and private key cryptography, and post-quantum cryptography. Public and private key cryptography involves the use of two different keys – a public key and a private key – to encrypt and decrypt data. Post-quantum cryptography is a form of encryption that is designed to be resistant to quantum computers. This type of encryption is designed to be significantly more secure than traditional encryption methods.
What Are The Benefits Of Hase Base Cryptography Quantum Resistant?
The primary benefit of Hase base cryptography quantum resistant is that it is designed to be resistant to attacks from quantum computers. This makes it a much more secure form of encryption than traditional methods, as it is able to resist the computing power of quantum computers. Additionally, Hase base cryptography quantum resistant utilizes public and private key cryptography, which can help to provide additional security to both the sender and the recipient of the data.
Are There Any Drawbacks To Hase Base Cryptography Quantum Resistant?
The primary drawback to Hase base cryptography quantum resistant is that it is more complex than traditional encryption methods. This can make it more difficult to implement and maintain, as it requires more computing power and expertise than traditional encryption systems. Additionally, it can be more expensive to implement, as it requires specialized hardware and software.

In conclusion, while hash-based cryptography has shown promise in being quantum resistant, it is not a foolproof solution. The technology is still relatively new and has not been widely adopted, which means it has not been thoroughly tested in real-world scenarios. Furthermore, quantum computing is developing rapidly, and there is always the possibility that a breakthrough in quantum algorithms could render hash-based cryptography vulnerable.
Despite these limitations, hash-based cryptography remains a promising option for those looking to future-proof their security measures. It offers a level of protection that is not available with traditional encryption methods and may be an excellent choice for organizations that handle sensitive data. As the threat of quantum computing grows, it is essential to explore all available options to ensure that our data remains secure.