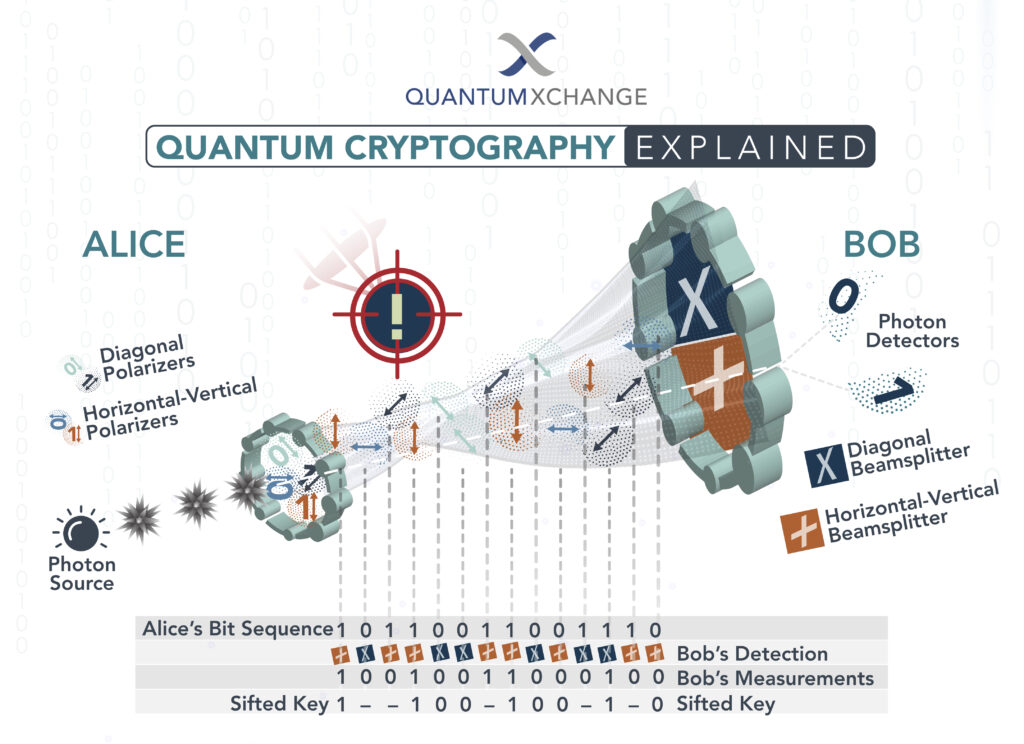
Cybersecurity threats are evolving at an alarming rate, and every day, hackers are finding new ways to breach systems and steal sensitive data. To combat this, the field of cryptography has been developed, which involves the use of mathematical algorithms to secure communication and protect data from unauthorized access. However, with the advancement of quantum computing, traditional cryptographic methods are becoming obsolete, and there is a need for new post-quantum cryptography replacements.
Post-quantum cryptography refers to cryptographic algorithms that are secure against attacks by quantum computers. These algorithms are being developed to replace traditional cryptographic methods, which will become vulnerable to quantum computers once they become powerful enough. The development of post-quantum cryptography is a crucial step in ensuring that our data remains secure in the future. In this article, we will explore some of the post-quantum cryptography replacements that are currently being developed and their potential to secure our digital world.
What is Post Quantum Cryptography?
Post-quantum cryptography is a type of cryptography that is designed to be secure even against an attacker with a quantum computing device. It is an emerging field of cryptography that has been gaining attention in recent years, as the development of quantum computers has become more of a reality. Post-quantum cryptography is designed to protect data from being decrypted by a quantum computer, which would otherwise be able to break traditional encryption algorithms.
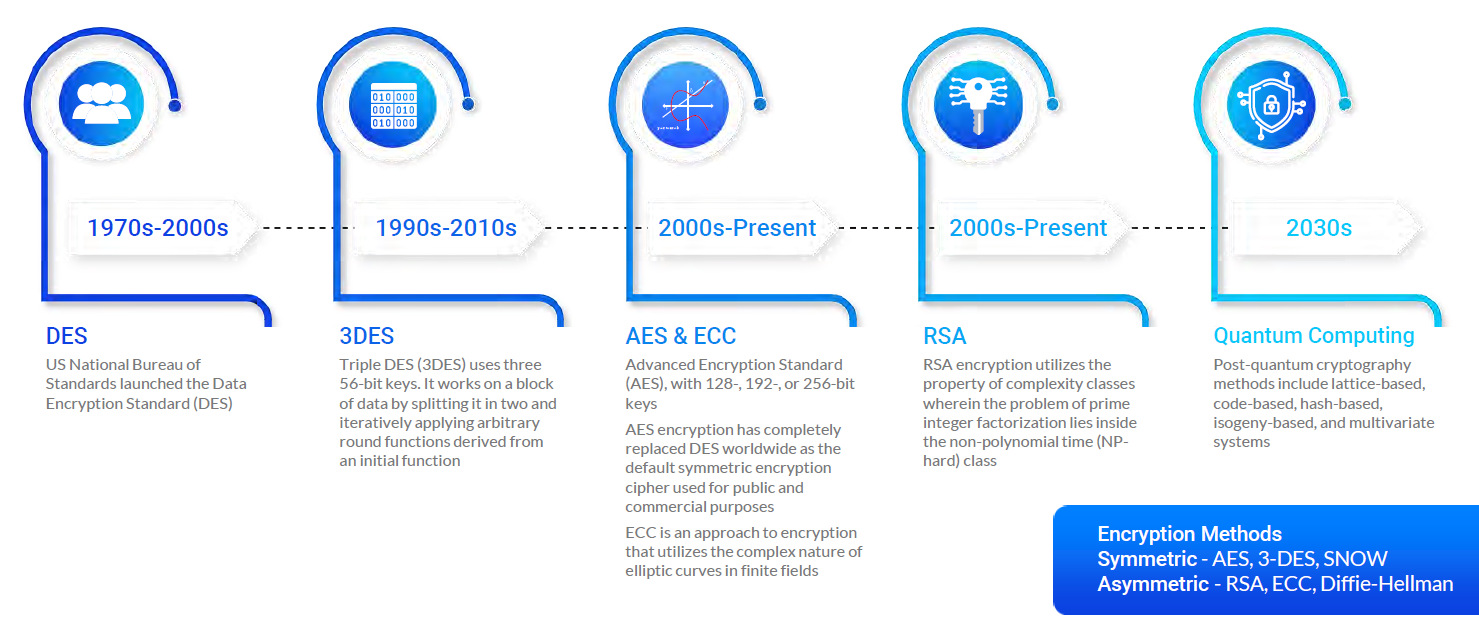
Post Quantum Cryptography Replacements
Post-quantum cryptography is still a relatively new field, so there are currently no widely accepted standards for these types of encryption algorithms. However, there are a number of proposed post-quantum cryptographic algorithms that are currently being developed and tested. Examples of these include McEliece, NTRU, and Supersingular Isogeny Diffie-Hellman (SIDH). Each of these algorithms has its own unique strengths and weaknesses, and it is important to understand the differences between them before selecting one for use.
McEliece Cryptography
McEliece cryptography is a public-key cryptosystem that is based on the idea of error-correcting codes. It is considered to be one of the most secure post-quantum cryptographic algorithms currently available. The main advantage of McEliece cryptography is that it is resistant to quantum computing attacks, as it is based on a hard mathematical problem that is believed to be difficult for a quantum computer to solve. However, McEliece cryptography is not as efficient as some of the other post-quantum cryptographic algorithms, which can make it more difficult to implement.
NTRU Cryptography
NTRU cryptography is a lattice-based cryptosystem that is designed to be resistant to quantum computing attacks. It has several advantages over other post-quantum cryptographic algorithms, including high speed, low memory usage, and low complexity. The main disadvantage of NTRU cryptography is that it is not as secure as some of the other post-quantum cryptographic algorithms, as it is vulnerable to attacks that exploit lattice-based algorithms.
Supersingular Isogeny Diffie-Hellman (SIDH)
Supersingular Isogeny Diffie-Hellman (SIDH) is an elliptic-curve-based post-quantum cryptographic algorithm that is designed to be resistant to quantum computing attacks. It is based on the discrete logarithm problem, which is believed to be difficult for a quantum computer to solve. SIDH is considered to be one of the most secure post-quantum cryptographic algorithms currently available, and it has the advantage of being relatively fast and efficient. However, it is not as widely used as some of the other post-quantum cryptographic algorithms due to its complexity.
Frequently Asked Questions – Post Quantum Cryptography Replacements
Post-quantum cryptography (PQC) is a type of cryptography that is being developed to protect data from attacks by quantum computers. PQC is designed to replace existing cryptographic algorithms, such as those used for digital signatures, which are vulnerable to attacks by quantum computers.
What is Post Quantum Cryptography?
Post-quantum cryptography (PQC) is a type of cryptography that is designed to be resistant to attacks from quantum computers. While traditional cryptographic algorithms are secure against attacks by classical computers, they are vulnerable to attacks from quantum computers. PQC is designed to replace existing cryptographic algorithms and provide a secure solution for data protection against quantum computer attacks.
PQC algorithms are being developed by cryptographers and mathematicians to provide a secure alternative to the existing cryptographic algorithms. The algorithms are designed to be resistant to attacks from quantum computers, and they use techniques such as error correcting codes, lattice-based cryptography, multivariate polynomials, and hash-based cryptography.
What is the Difference Between Classical and Quantum Cryptography?
The main difference between classical and quantum cryptography is in the way they protect data. Classical cryptography uses techniques such as encryption and digital signatures to protect data. These techniques are vulnerable to attacks from powerful computers. Quantum cryptography, on the other hand, uses techniques such as quantum key distribution, which allows two parties to securely exchange a key without it being intercepted.
These techniques are designed to be resistant to attacks from quantum computers, and they use quantum mechanics to protect data. For example, quantum key distribution uses the principles of quantum physics to ensure that the key shared between two parties has not been intercepted. This makes it much more secure than traditional cryptography.
What are the Advantages of Post Quantum Cryptography?
The main advantage of post-quantum cryptography is that it provides a secure solution for data protection against attacks from quantum computers. As quantum computers become more powerful, they will be able to break the existing cryptographic algorithms. PQC algorithms provide an alternative that is resistant to attacks from quantum computers.
PQC algorithms are also more efficient than traditional cryptographic algorithms, meaning they require less computing power. This makes them suitable for use in applications where speed and efficiency are important, such as in embedded systems or mobile devices.
What are the Disadvantages of Post Quantum Cryptography?
The main disadvantage of post-quantum cryptography is that it is still in the development stage. While the algorithms have been designed to be resistant to attacks from quantum computers, they are not yet widely used and there is still a lot of research being done to ensure they are secure. This means that there is still a risk that the algorithms could be broken by quantum computers in the future.
Another disadvantage is that PQC algorithms are more complex than traditional cryptographic algorithms, and this can make them difficult to implement. This means that they may be more expensive to use than traditional algorithms, and they may require more computing power.
What is the Future of Post Quantum Cryptography?
The future of post-quantum cryptography is promising. As quantum computers become more powerful, it is clear that traditional cryptographic algorithms will become increasingly vulnerable to attacks. PQC algorithms provide a secure alternative that is designed to be resistant to attacks from quantum computers.
PQC algorithms are still being researched and developed, and it is likely that they will become more widely used in the future. As the technology matures, it is likely that the algorithms will become more efficient and cost-effective, making them suitable for use in a wide range of applications.
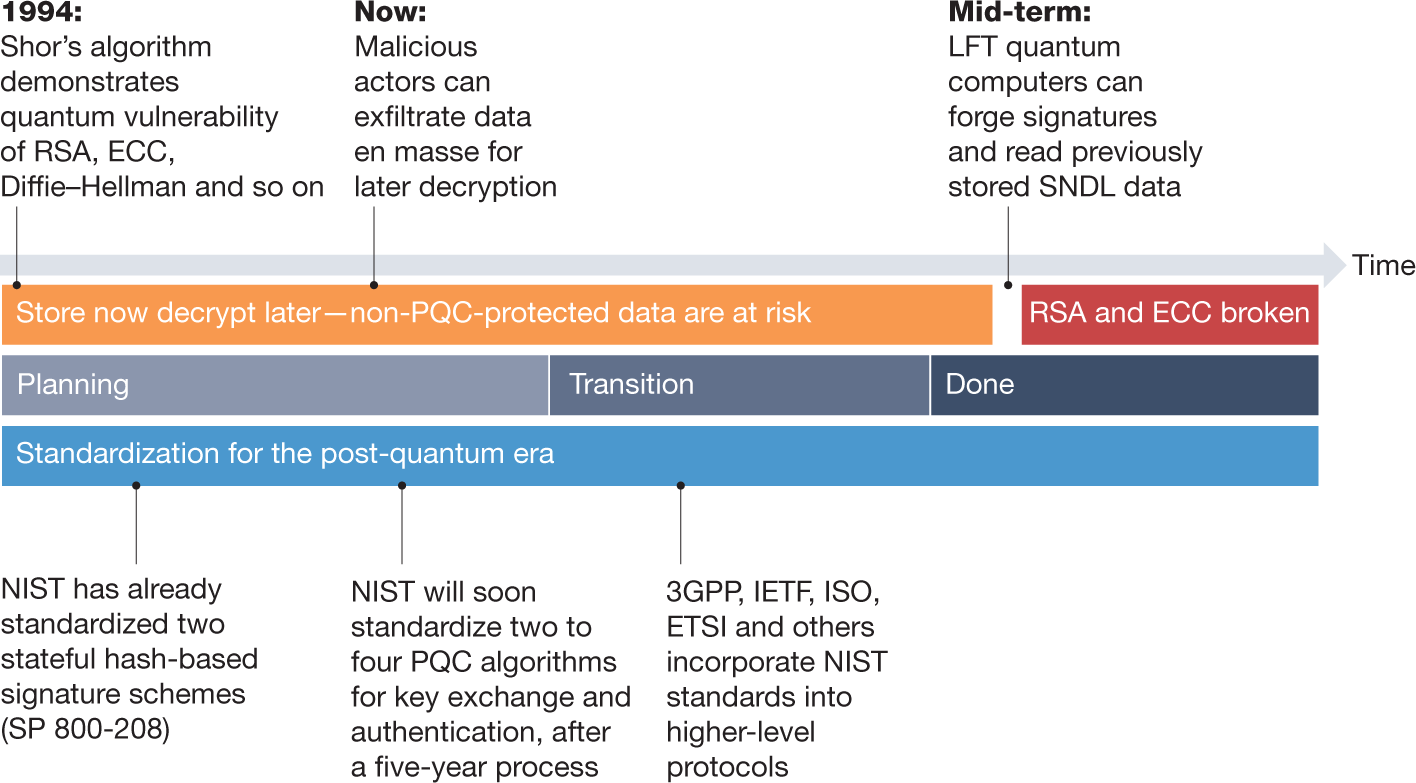
In conclusion, the world of cryptography is constantly evolving, and as technology advances, so do the methods of encryption. As we move towards the era of quantum computing, the need for post-quantum cryptography becomes increasingly important. The replacements for classical cryptographic techniques are being developed to ensure that we are able to protect sensitive information in a world where quantum computers can break traditional encryption methods in a matter of seconds.
While post-quantum cryptography is still in its infancy, many researchers and companies are dedicating resources to developing new and innovative methods of encryption that will be resistant to quantum computing. It is important for individuals and organizations to stay informed about these developments and to start planning for the transition to post-quantum cryptography. By taking action now, we can ensure that our data remains secure in a world where quantum computers are becoming increasingly powerful.