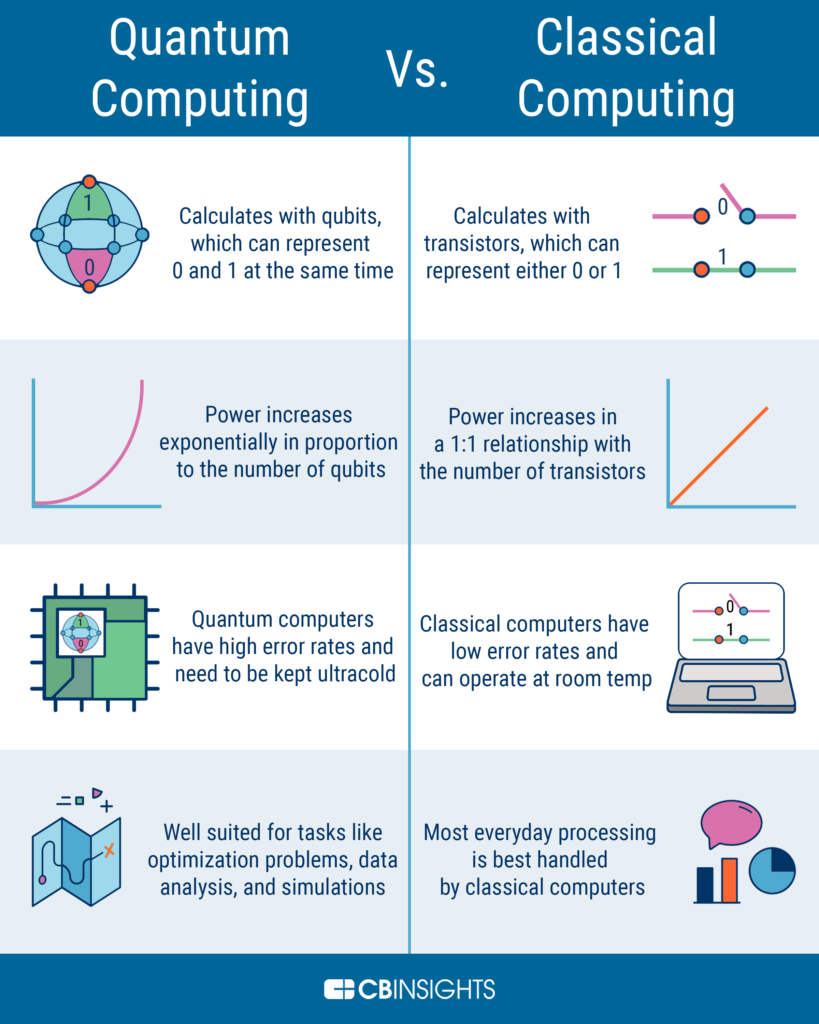
In the modern world, cryptography is a fundamental part of security systems. It is an essential tool that ensures that confidential information remains protected from malicious attacks. However, with the emergence of quantum computers, the security of traditional cryptographic systems is under threat. Quantum computers have the potential to break current encryption algorithms, leaving sensitive data vulnerable to cybercriminals. Therefore, it is crucial to explore ways to defend cryptography from quantum computers.
The challenge of defending cryptography from quantum computers requires a collaborative effort from mathematicians, computer scientists, and physicists. The development of quantum-resistant cryptography is a promising solution that can withstand quantum attacks. In this article, we will explore the different methods used to defend cryptography from quantum computers. We will also discuss the limitations and potential risks associated with these methods. By the end of this article, readers will have a comprehensive understanding of how to protect their data in the era of quantum computing.
- Implement post-quantum algorithms that are resistant to quantum computing.
- Increase key size & length to make it harder for a quantum computer to crack.
- Use elliptic curves cryptography to replace RSA.
- Combine symmetric & asymmetric cryptography for added security.
- Invest in quantum-safe hardware & software solutions.
- Encrypt data multiple times with different algorithms.
Cryptography and Quantum Computers
Cryptography is an integral part of modern-day security, but the emergence of quantum computing poses a major threat to the security of cryptographic systems. Quantum computers are able to break through many of the security measures that traditional computers are not able to, making it essential to protect cryptographic systems from these powerful machines.
How to Defend Cryptography from Quantum Computers?
In order to defend cryptography from quantum computers, it is important to understand the potential weaknesses in existing cryptographic systems and the potential solutions that can be implemented to prevent quantum attacks. Here are some of the ways to protect against quantum computers:
1. Use Strong Encryption Algorithms
One of the most important steps that can be taken to protect cryptographic systems from quantum computers is to use strong encryption algorithms. These algorithms are designed to make it much more difficult for quantum computers to break through the encryption. Some of the most commonly used encryption algorithms include AES, RSA, and ECC. These algorithms have been tested against quantum computers and have been found to be resistant to attack.
2. Implement Post-Quantum Cryptography
Another way to protect cryptographic systems from quantum computers is to implement post-quantum cryptography. Post-quantum cryptography is a type of cryptography that is designed to be resistant to attack by quantum computers. This type of cryptography uses algorithms that are based on mathematical problems that are believed to be difficult for quantum computers to solve. This makes it much more difficult for quantum computers to break through these algorithms.
3. Use Quantum-Resistant Cryptography
Another method for protecting cryptographic systems from quantum computers is to use quantum-resistant cryptography. Quantum-resistant cryptography is designed to be resistant to attack by quantum computers. This type of cryptography uses algorithms that are based on problems that are believed to be difficult for quantum computers to solve. This makes it much more difficult for quantum computers to break through these algorithms.
4. Utilize Quantum Key Distribution
One of the most effective ways to protect cryptographic systems from quantum computers is to use quantum key distribution. This type of cryptography utilizes quantum entanglement to create a secure communication channel between two parties. With quantum key distribution, the two parties can exchange information that is encrypted in such a way that it is impossible for a quantum computer to break through.
5. Implement Quantum-Secure Authentication
Another way to protect cryptographic systems from quantum computers is to implement quantum-secure authentication. This type of authentication utilizes quantum cryptography to create an authentication system that is resistant to attack by quantum computers. This authentication system is based on mathematical problems that are believed to be difficult for quantum computers to solve.
6. Utilize Quantum-Safe Storage
Another important step that can be taken to protect cryptographic systems from quantum computers is to utilize quantum-safe storage. Quantum-safe storage is a type of storage that is designed to be resistant to attack by quantum computers. This type of storage utilizes algorithms that are based on mathematical problems that are believed to be difficult for quantum computers to solve.
7. Develop Quantum-Resistant Protocols
Another way to protect cryptographic systems from quantum computers is to develop quantum-resistant protocols. Quantum-resistant protocols are designed to be resistant to attack by quantum computers. These protocols utilize algorithms that are based on mathematical problems that are believed to be difficult for quantum computers to solve.
8. Implement Quantum-Resistant Network Security
Another way to protect cryptographic systems from quantum computers is to implement quantum-resistant network security. This type of network security utilizes algorithms that are based on mathematical problems that are believed to be difficult for quantum computers to solve. This makes it much more difficult for quantum computers to gain access to a network.
9. Utilize Quantum-Secure Communications
Another important step that can be taken to protect cryptographic systems from quantum computers is to use quantum-secure communications. This type of communications utilizes algorithms that are based on mathematical problems that are believed to be difficult for quantum computers to solve. This makes it much more difficult for quantum computers to intercept communications.
10. Implement Quantum-Safe Key Management
The final step that can be taken to protect cryptographic systems from quantum computers is to implement quantum-safe key management. This type of key management utilizes algorithms that are based on mathematical problems that are believed to be difficult for quantum computers to solve. This makes it much more difficult for quantum computers to access keys and break through encryption.
Frequently Asked Questions
Cryptography is a technique used to protect data from unauthorized access. It can be used to defend against quantum computers, which are computers that use quantum mechanical principles to process data. This article will answer some of the most common questions related to defending cryptography from quantum computers.
What is Quantum Computing?
Quantum computing is a form of computing which harnesses the principles of quantum mechanics to process data in a very efficient way. This type of computing can be used to solve complex problems which would be impossible to solve with traditional computing methods. Quantum computing can also be used to break existing cryptographic algorithms, making data vulnerable to attack.
How can Cryptography be Protected from Quantum Computers?
One way to protect cryptography from quantum computers is to use post-quantum algorithms. These algorithms are designed to be resistant to attack from quantum computers, and therefore can be used to protect data from unauthorized access. Another way to protect cryptography from quantum computers is to use quantum-resistant hardware. This hardware is designed to be resistant to attack from quantum computers, and can be used to protect cryptographic keys and data.
Are Post-Quantum Algorithms Secure?
Post-quantum algorithms are designed to be secure against attack from quantum computers. However, it is important to note that no algorithm is 100% secure. Post-quantum algorithms are designed to be more secure than traditional algorithms, but they still have some weaknesses that can be exploited by attackers. It is therefore important to use post-quantum algorithms in combination with other security measures, such as hardware-backed security.
What is Hardware-Backed Security?
Hardware-backed security is a type of security that uses hardware to protect cryptographic keys and data. This type of security is designed to be resistant to attack from quantum computers, as the hardware is designed to be resistant to attack from quantum computers. Hardware-backed security can be used in combination with post-quantum algorithms to provide the highest level of security against attack from quantum computers.
What is Quantum-Resistant Hardware?
Quantum-resistant hardware is a type of hardware designed to be resistant to attack from quantum computers. This type of hardware uses principles of quantum mechanics to protect cryptographic keys and data. Quantum-resistant hardware can be used in combination with post-quantum algorithms to provide the highest level of security against attack from quantum computers.
In conclusion, the rise of quantum computing poses a significant threat to the security of our current cryptographic systems. However, it is important to remember that cryptography is an ever-evolving field, and researchers are working tirelessly to develop new algorithms and protocols that can withstand the power of quantum computers. By staying informed and engaged in the latest developments in cryptography, we can help ensure that our digital communications and transactions remain secure in the face of this emerging threat.
Ultimately, the defense of cryptography from quantum computers will require a collaborative effort from researchers, industry professionals, and policymakers. It is up to us as a society to recognize the importance of secure communication and to invest in the resources and technologies necessary to protect it. By taking a proactive approach to this challenge, we can help ensure that our digital future remains safe and secure for generations to come.