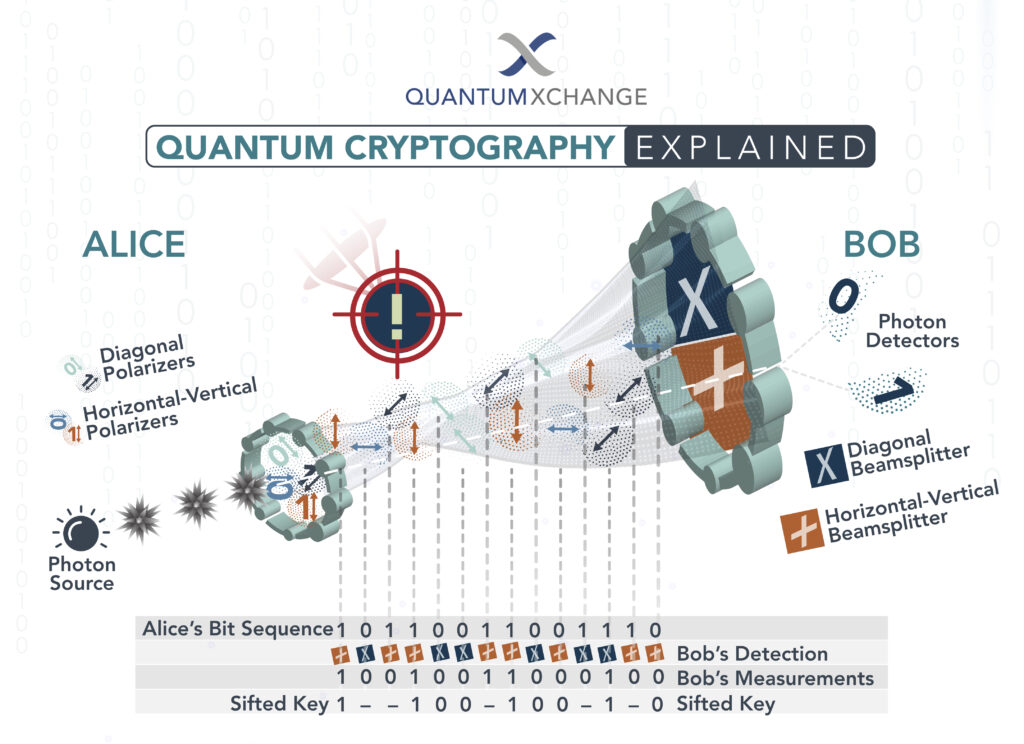
In today’s digital age, information security has become more crucial than ever. With the increasing use of the internet for communication, online transactions, and data storage, the need for robust encryption technologies has become paramount. Cryptography, the practice of secure communication, has been used for centuries to protect sensitive information. However, with the advent of quantum computers, traditional encryption methods are becoming increasingly vulnerable. This is where post-quantum cryptography comes in.
Post-quantum cryptography refers to cryptographic algorithms that are designed to resist attacks from quantum computers. These algorithms are based on mathematical problems that are believed to be hard to solve even for quantum computers. In this guide to post-quantum cryptography, we will explore the basics of quantum computing and how it threatens traditional cryptography. We will also delve into the different post-quantum cryptographic algorithms that are being developed and their potential applications. Whether you are a cybersecurity professional, an IT manager, or simply interested in the latest advancements in cryptography, this guide will provide you with the knowledge you need to understand the future of information security.

What is Post-Quantum Cryptography?
Post-Quantum Cryptography (PQC) is a new form of cryptography that is designed to protect data from attacks by quantum computers. Unlike traditional encryption methods, PQC is designed to be resistant to quantum computing attacks, providing a higher level of security for digital data. This is achieved by using larger and more complex keys, as well as advanced algorithms that are designed to be resistant to quantum computing attacks.
A Guide to Post-Quantum Cryptography
What is Quantum Computing and How Does it Affect Cryptography?
Quantum computing is a new type of computing technology that uses quantum-mechanical phenomena to perform calculations. It is much faster and more powerful than traditional computing, and has the potential to revolutionize the way we use computers. Quantum computing also has the potential to break current encryption methods, which could have serious implications for data security. This is why post-quantum cryptography is so important.
The main difference between traditional cryptography and post-quantum cryptography is that traditional cryptography is vulnerable to quantum computing attacks. Post-quantum cryptography, on the other hand, is designed to be resistant to these attacks. This is done by using larger and more complex keys, as well as advanced algorithms that are designed to be resistant to quantum computing attacks.
How Does Post-Quantum Cryptography Work?
Post-Quantum Cryptography works by using larger and more complex keys than traditional cryptography. These larger keys provide a higher level of security, as they are more difficult for quantum computers to break. Post-Quantum Cryptography also relies on advanced algorithms that are designed to be resistant to quantum computing attacks. These algorithms use mathematical techniques such as lattice-based cryptography and code-based cryptography to protect data from quantum computing attacks.
In addition to larger and more complex keys, Post-Quantum Cryptography also incorporates other security measures such as digital signatures and key exchange protocols. These measures help ensure that the data is secure even if the encryption is broken. Post-Quantum Cryptography also includes measures to ensure that data is not tampered with during transmission.
What Are the Advantages of Post-Quantum Cryptography?
Post-Quantum Cryptography offers a number of advantages over traditional cryptography. The most significant advantage is that it is more secure, as it is designed to resist attacks from quantum computers. Additionally, Post-Quantum Cryptography is faster and more efficient than traditional cryptography, making it a better choice for large-scale data encryption. Finally, Post-Quantum Cryptography is more reliable, as the algorithms used are designed to be resistant to quantum computing attacks.
What Are the Disadvantages of Post-Quantum Cryptography?
Although Post-Quantum Cryptography offers a number of advantages over traditional cryptography, there are some drawbacks as well. The most significant drawback is that Post-Quantum Cryptography is more expensive than traditional cryptography. Additionally, Post-Quantum Cryptography is more complex than traditional cryptography, which can make it more difficult to implement. Finally, Post-Quantum Cryptography is still in its early stages of development, which means that it may be vulnerable to attacks that are not yet known.
Conclusion
Post-Quantum Cryptography is a new form of cryptography that is designed to resist attacks from quantum computers. It offers a higher level of security than traditional cryptography, as well as faster speeds and more efficient algorithms. However, Post-Quantum Cryptography is more expensive and more complex than traditional cryptography, and it is still in its early stages of development. Nevertheless, Post-Quantum Cryptography is an important step forward in data security, and is likely to become more widely used as quantum computing technology advances.
Frequently Asked Questions about Post Quantum Cryptography
Post quantum cryptography (PQC) is a type of cryptography that is designed to secure data from potential quantum computing attacks. It is a relatively new field of cryptography and is the subject of ongoing research and development.
What is Post Quantum Cryptography?
Post quantum cryptography (PQC) is a type of cryptography that is designed to be secure against attacks from quantum computers. It is based on mathematical algorithms and techniques that are designed to be resistant to attacks from quantum computing algorithms. PQC is a relatively new field of cryptography and is still under development, but it has the potential to provide an additional layer of security beyond what traditional cryptographic algorithms can provide.
PQC includes a variety of cryptographic algorithms, such as lattice-based cryptography, code-based cryptography, hash-based cryptography, and multivariate cryptography. These algorithms make use of mathematical problems that are believed to be difficult for quantum computers to solve. This makes them resistant to attacks from quantum computing algorithms, thus providing a higher level of security.
What is the Difference Between Post Quantum Cryptography and Traditional Cryptography?
The difference between post quantum cryptography and traditional cryptography is that post quantum cryptography is designed to be secure against attacks from quantum computers while traditional cryptography is not. Traditional cryptography is based on mathematical algorithms and techniques that are believed to be resistant to attacks from classical computing algorithms, but they are not resistant to attacks from quantum computing algorithms.
Post quantum cryptography is designed to address this issue by making use of mathematical problems that are believed to be difficult for quantum computers to solve. This makes them resistant to attacks from quantum computing algorithms, thus providing a higher level of security. Additionally, post quantum cryptography is still in its early stages of development, and there are still a number of challenges that need to be addressed before it can be widely adopted.
What Are the Advantages of Post Quantum Cryptography?
The main advantage of post quantum cryptography is that it provides a higher level of security than traditional cryptography. Traditional cryptography is based on mathematical algorithms and techniques that are believed to be resistant to attacks from classical computing algorithms, but they are not resistant to attacks from quantum computing algorithms. Post quantum cryptography is designed to address this issue by making use of mathematical problems that are believed to be difficult for quantum computers to solve.
Additionally, post quantum cryptography is still in its early stages of development, and there are a number of advantages that can be gained by using it. For example, it can provide a higher level of security than traditional cryptography, as well as more flexibility and scalability. Additionally, it can allow for more efficient use of computing resources, as it can be faster and require fewer resources to process data.
What Are the Disadvantages of Post Quantum Cryptography?
The main disadvantage of post quantum cryptography is that it is still in its early stages of development and there are a number of challenges that need to be addressed before it can be widely adopted. Additionally, post quantum cryptography is more computationally intensive than traditional cryptography and requires more computing resources to process data. This can make it more expensive and less efficient than traditional cryptography.
Additionally, post quantum cryptography is still relatively new and there is still a lack of understanding of how it works and how to properly use it. This can make it difficult to implement, as there is still a lack of guidance and resources available to help organizations implement post quantum cryptography.
What Are the Benefits of Using Post Quantum Cryptography?
The main benefit of using post quantum cryptography is that it provides a higher level of security than traditional cryptography. As mentioned above, traditional cryptography is based on mathematical algorithms and techniques that are believed to be resistant to attacks from classical computing algorithms, but they are not resistant to attacks from quantum computing algorithms. Post quantum cryptography is designed to address this issue by making use of mathematical problems that are believed to be difficult for quantum computers to solve.
Additionally, post quantum cryptography provides more flexibility and scalability than traditional cryptography, as it can be used to process data more efficiently. Additionally, post quantum cryptography can provide a higher level of security for data transmission and storage, as it can be used to encrypt data in a way that is resistant to quantum computing attacks. Finally, post quantum cryptography can also provide improved authentication and access control, as it can be used to verify the identity of users and ensure that only authorized users can access data.

In conclusion, post-quantum cryptography is an emerging field that offers a promising solution to the impending threat of quantum computers. With the rise of quantum computing, traditional cryptographic algorithms may no longer be secure, leading to a need for new and innovative solutions. Post-quantum cryptography offers a wide range of cryptographic techniques that are designed to withstand quantum attacks, ensuring that data remains secure even in the face of quantum computing.
As technology continues to advance, it is essential to keep up with the latest developments in cryptography. Post-quantum cryptography is an exciting area that promises to revolutionize the world of cybersecurity by providing robust and resilient cryptographic solutions that can withstand the power of quantum computing. As we move forward into a future that is increasingly reliant on technology, post-quantum cryptography will undoubtedly play a significant role in ensuring the security of our digital world.