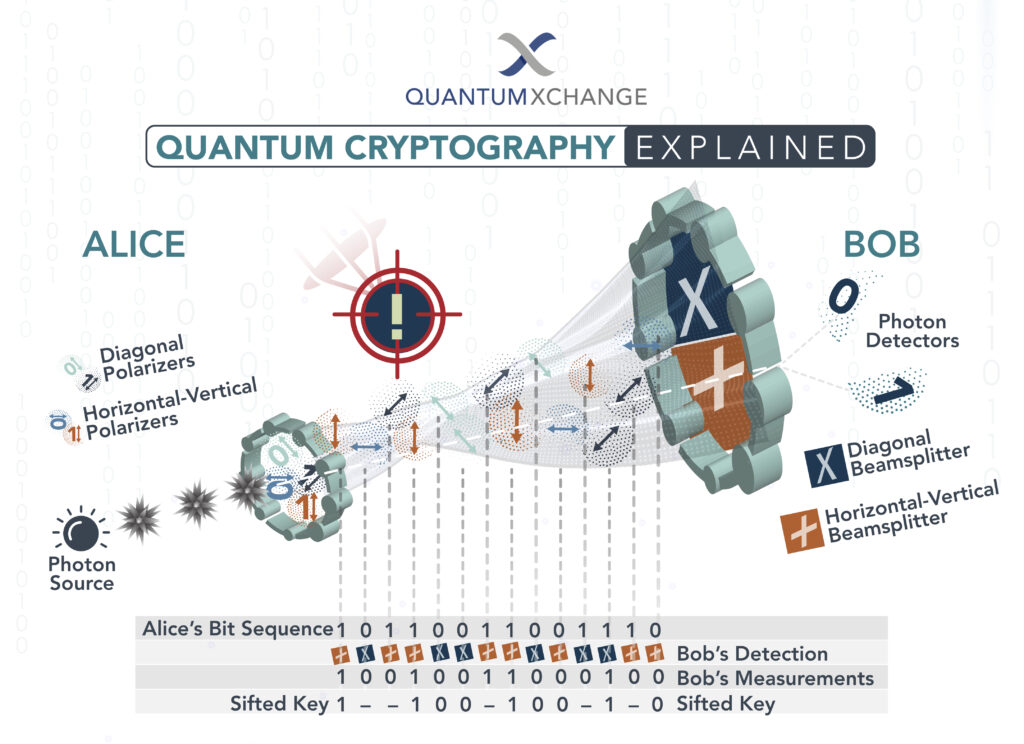
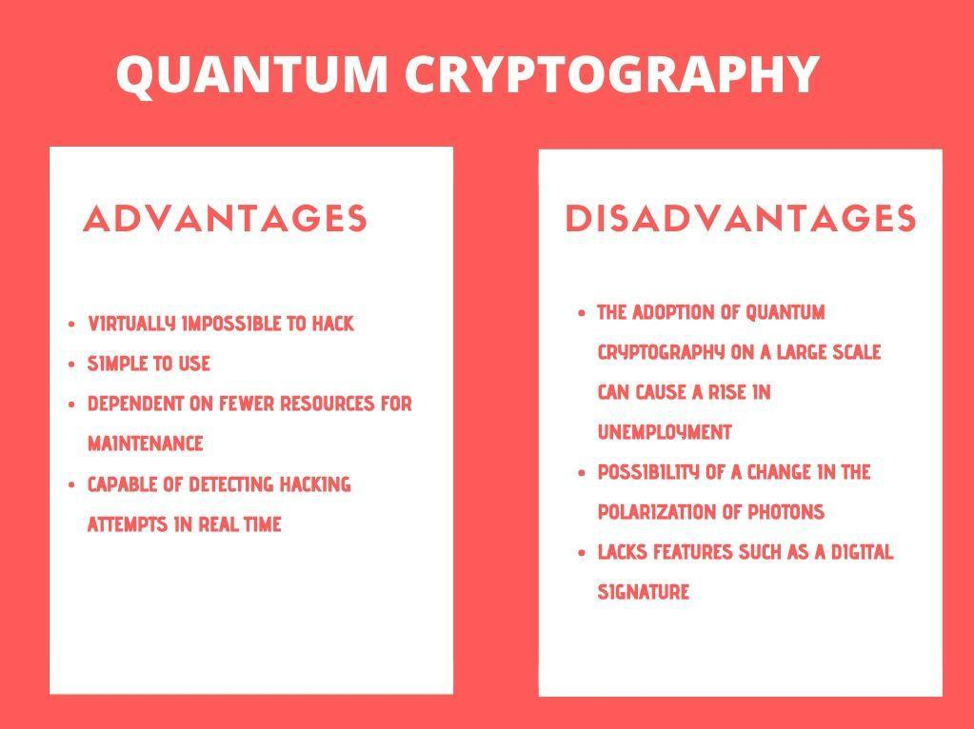
As technology continues to advance, so do the threats posed to our cybersecurity. The rise of quantum computing has led to concerns that traditional cryptographic methods may soon be rendered obsolete. This has led to the development of post-quantum cryptography, a new form of encryption that aims to protect our digital information from quantum-based attacks.
The purpose of post-quantum cryptography is to ensure that our digital information remains secure even in the face of quantum computing. Traditional cryptographic methods rely on mathematical problems that are difficult for classical computers to solve, but quantum computers have the potential to solve these problems with ease. Post-quantum cryptography, on the other hand, relies on mathematical problems that are believed to be difficult for both classical and quantum computers to solve. By using these new cryptographic methods, we can protect our digital information from the threats posed by quantum computing and ensure that our data remains secure.
Post-quantum cryptography is a form of cryptography which is secure against attacks by quantum computers. It is an emerging area of research which seeks to develop cryptographic algorithms that are secure against an attack by a quantum computer. The goal is to create algorithms that are secure against a quantum computer, even if one is built in the future.
What is the Purpose of Post-Quantum Cryptography?
Post-quantum cryptography is an emerging field of cryptography that is focused on developing cryptographic algorithms that are secure against attacks by quantum computers. The purpose of post-quantum cryptography is to provide a secure way to exchange data that is resistant to attacks by quantum computers, which are expected to become available in the near future.
As quantum computers become more powerful and capable of faster calculations, they will be able to break many of the current cryptography algorithms, making the data that is encrypted with them vulnerable. Post-quantum cryptography is designed to provide a secure way to exchange data that is resistant to attacks by quantum computers, thus ensuring that sensitive data remains secure.
How Does Post-Quantum Cryptography Work?
Post-quantum cryptography is based on mathematical problems that are believed to be too difficult for quantum computers to solve. These problems are generally related to number theory, algebra or coding theory, and involve solving problems that involve large numbers or finding patterns in random data. By using these mathematical problems as the basis for their cryptographic algorithms, post-quantum cryptography can provide a secure way to exchange data that is resistant to attacks by quantum computers.
Post-quantum cryptography algorithms can be implemented in software or hardware, and are designed to be interoperable with existing cryptographic algorithms. This allows organizations to transition to post-quantum cryptography gradually, allowing them to transition to the more secure algorithms as quantum computers become more powerful.
What Are the Benefits of Post-Quantum Cryptography?
Post-quantum cryptography offers organizations a secure way to exchange data that is resistant to attacks by quantum computers. By using post-quantum cryptography, organizations can ensure that their data remains secure even as quantum computers become more powerful and capable of breaking existing cryptographic algorithms.
In addition, post-quantum cryptography algorithms are designed to be interoperable with existing cryptographic algorithms. This allows organizations to transition to post-quantum cryptography gradually, allowing them to transition to the more secure algorithms as quantum computers become more powerful.
What Are the Challenges of Post-Quantum Cryptography?
The primary challenge faced by post-quantum cryptography is that it is not yet widely used. As quantum computers become more powerful, it is likely that post-quantum cryptography will become more widely adopted, but for now it is still relatively new and not widely used.
In addition, post-quantum cryptography algorithms are computationally intensive, meaning that they require more computing power than traditional cryptography algorithms. This can make them more expensive to implement, and may require organizations to upgrade their hardware in order to use post-quantum cryptography.
Conclusion
Post-quantum cryptography is an emerging field of cryptography that is focused on developing cryptographic algorithms that are secure against attacks by quantum computers. The purpose of post-quantum cryptography is to provide a secure way to exchange data that is resistant to attacks by quantum computers, which are expected to become available in the near future. Post-quantum cryptography offers organizations a secure way to exchange data, but it is not yet widely used and can be computationally intensive, requiring organizations to upgrade their hardware in order to use it.
Frequently Asked Questions About Post-Quantum Cryptography Brainly
Post-quantum cryptography brainly is a form of cryptography that is resistant to attacks from quantum computers. It is an advanced form of cryptography that uses complex algorithms to keep data secure and protected from malicious attacks.
What Is Post-Quantum Cryptography Brainly?
Post-quantum cryptography brainly is an advanced form of cryptography that uses complex algorithms to protect data from quantum computer attacks. This form of cryptography is designed to be resistant to the powerful computing power of a quantum computer, which would be able to break traditional encryption algorithms. Post-quantum cryptography brainly utilizes algorithms based on mathematical problems that are difficult for a quantum computer to solve.
What Are the Benefits of Post-Quantum Cryptography Brainly?
Post-quantum cryptography brainly provides a greater degree of security than traditional encryption algorithms. It is designed to be resistant to the powerful computing power of a quantum computer, which would be able to break traditional encryption algorithms. This form of cryptography can also protect data from malicious attacks, such as those that could be conducted by a quantum computer. Additionally, post-quantum cryptography brainly is designed to be more efficient, allowing for faster data encryption and decryption.
What Are the Disadvantages of Post-Quantum Cryptography Brainly?
The main disadvantage of post-quantum cryptography brainly is that it is still relatively new and unproven. It is not widely used yet, so there is a lack of testing and experience with this form of cryptography. Additionally, post-quantum cryptography brainly requires a greater amount of computing power than traditional encryption algorithms. This can cause performance issues and increase the cost of implementing this form of cryptography.
What Kind of Data Can Be Protected With Post-Quantum Cryptography Brainly?
Post-quantum cryptography brainly is designed to protect any type of data, such as confidential documents, financial information, and passwords. It is also suitable for protecting data that is stored on a quantum computer, as it is designed to be resistant to the powerful computing power of a quantum computer.
How Secure Is Post-Quantum Cryptography Brainly?
Post-quantum cryptography brainly is designed to be highly secure. It is designed to be resistant to the powerful computing power of a quantum computer, which would be able to break traditional encryption algorithms. Additionally, post-quantum cryptography brainly utilizes algorithms based on mathematical problems that are difficult for a quantum computer to solve. This makes it more difficult for malicious actors to break the encryption and access the data.
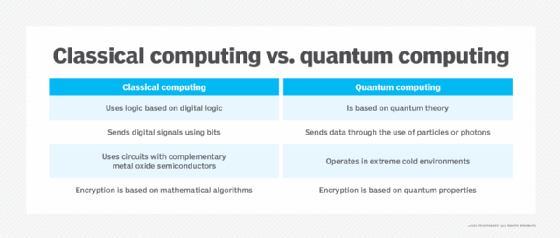
In conclusion, the purpose of post-quantum cryptography is to secure information in a world where quantum computers are becoming more powerful. Quantum computers have the potential to break traditional encryption methods, leaving sensitive information vulnerable to theft and misuse. Post-quantum cryptography provides a solution by developing new encryption algorithms that are resistant to attacks by quantum computers. This technology is essential for protecting sensitive information like financial data, personal information, and government secrets.
As we continue to rely more and more on digital technology, the need for secure encryption methods becomes increasingly important. Post-quantum cryptography is the next step in the evolution of digital security, providing a solution to the potential threat of quantum computers. With the development of post-quantum cryptography, we can ensure that our information is secure and protected from malicious attacks. In short, the purpose of post-quantum cryptography is to ensure that we can continue to live in a digital world without fear of our information being compromised.