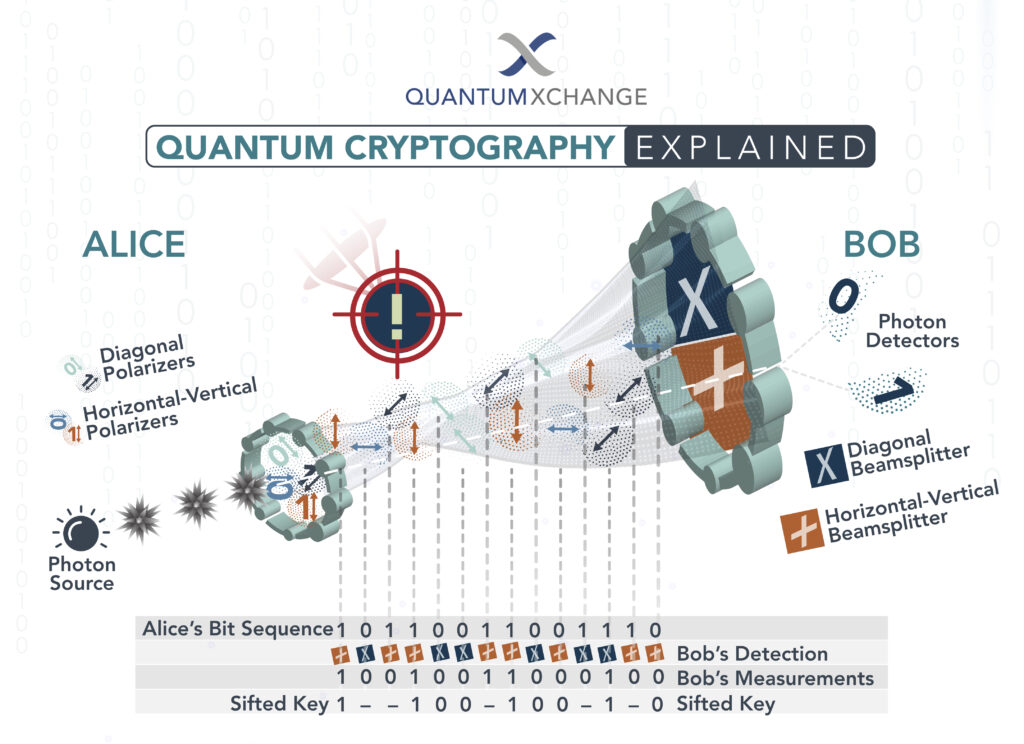
Quantum cryptography is a cutting-edge technology that allows for secure communication between two parties without the risk of interception or hacking. As the world becomes increasingly digital, the need for secure communication has become more critical than ever. Quantum cryptography offers a solution to this problem by using the principles of quantum mechanics to encode information in a way that is virtually impossible to decode by anyone other than the intended recipient.
However, implementing quantum cryptography is not a simple task, and it requires a solid understanding of the principles of quantum mechanics, as well as the ability to apply these principles in a practical setting. In this guide, we’ll explore the basics of quantum cryptography and provide a step-by-step approach to implementing this technology in your organization. Whether you’re a researcher, a business owner, or just someone interested in the future of secure communication, this guide will provide you with the knowledge and tools you need to get started with quantum cryptography.
Quantum cryptography is a secure form of communication that is based on the principles of quantum mechanics. It uses the laws of physics to create a secure channel between two communicating parties. To implement quantum cryptography, the two parties must have access to a quantum channel, such as an optical fiber or a satellite link. This channel must be free of eavesdroppers and other interference. The two parties must also possess a quantum key, which is shared between them and used to encrypt and decrypt messages. Finally, they must use quantum algorithms to perform the encryption and decryption operations.
- Step 1: Establish a quantum channel between the two communicating parties.
- Step 2: Create and share a quantum key between the two parties.
- Step 3: Use quantum algorithms to encrypt and decrypt messages.
- Step 4: Verify that the quantum channel is secure and free of eavesdroppers.

What is Quantum Cryptography?
Quantum cryptography is an advanced security technology used to protect data from attacks and unauthorized access. It uses the principles of quantum mechanics to generate a secure key that can be used to encrypt and decrypt data. Quantum cryptography is considered to be the most secure form of encryption available today.
How to Implement Quantum Cryptography?
Implementing quantum cryptography requires careful planning and a thorough understanding of the technology. The following steps outline the process for implementing quantum cryptography in an organization:
Step 1: Choose a Quantum Cryptography Algorithm
The first step in implementing quantum cryptography is to select the appropriate algorithm. There are several quantum cryptography algorithms available, each with its own strengths and weaknesses. Organizations should carefully evaluate their needs and select the algorithm that best meets their requirements.
Once the appropriate algorithm has been selected, the organization should develop a plan for implementing it. This plan should include information about how the algorithm will be implemented, who will be responsible for it, and what resources will be needed.
Step 2: Install the Quantum Cryptography Software
Once the algorithm has been chosen, the organization should install the necessary software to enable quantum cryptography. This software is typically provided by the algorithm provider and should be installed on the organization’s servers. The software enables the organization to generate and manage the quantum key used for encryption and decryption.
Step 3: Configure the Quantum Cryptography Software
Once the software is installed, the organization should configure it to meet their specific needs. This includes setting up the key management system, configuring the encryption and decryption processes, and setting up access control.
Step 4: Test the Quantum Cryptography System
Before the organization can begin using the quantum cryptography system, they must ensure that it is functioning properly. This includes testing the system to make sure it is secure and reliable.
Step 5: Deploy the Quantum Cryptography System
Once the system has been tested and configured, the organization can begin using it in their environment. This includes deploying the necessary hardware and software, establishing secure communication channels, and training users on how to use the system.
Step 6: Monitor the Quantum Cryptography System
The organization should regularly monitor the quantum cryptography system to ensure its security and functionality. This includes checking the system for any vulnerabilities or weaknesses, monitoring the system’s performance, and ensuring that the system is updated with the latest security patches.
Frequently Asked Questions about Quantum Cryptography
Quantum cryptography is a secure communication method that utilizes principles of quantum mechanics to encrypt data. This technique is being used to ensure secure communication between two parties and is considered to be one of the most secure encryption methods available.
What is quantum cryptography?
Quantum cryptography is a secure communication method that uses the principles of quantum mechanics to encrypt data. This technique works by encoding the data in a way that it cannot be read by anyone other than the intended recipient. The data is sent through a quantum channel, which is a special type of communication channel that uses quantum principles to keep the data secure. Once the data is sent, the recipient is able to decode the data using a key, which is also kept secure using quantum principles.
What are the advantages of quantum cryptography?
One of the main advantages of quantum cryptography is its high level of security. Since the data is encoded using quantum principles, it is virtually impossible for anyone to crack the encryption and gain access to the data. Additionally, quantum cryptography is not vulnerable to many of the attacks that plague traditional encryption methods. This means that the data is much more secure than with traditional encryption methods.
How is quantum cryptography implemented?
Quantum cryptography is implemented by using a special type of communication channel known as a quantum channel. This is a special type of communication channel that uses quantum principles to keep the data secure. The data is encoded into a quantum state and then sent through the quantum channel to the intended recipient. The recipient then uses a key to decode the data.
What are the limitations of quantum cryptography?
One of the main limitations of quantum cryptography is that it can only be used for point-to-point communication. This means that it is not suitable for applications that require multiple parties to communicate at the same time. Additionally, quantum cryptography is limited by the length of the quantum channel and the distance between the sender and the recipient.
What is the future of quantum cryptography?
The future of quantum cryptography is very promising. Researchers are already working on new algorithms and techniques to make quantum cryptography even more secure and efficient. Additionally, quantum cryptography is being used in many different applications such as banking, government, and military communications. As the technology continues to develop, it is likely that quantum cryptography will become an even more secure and reliable way to communicate.
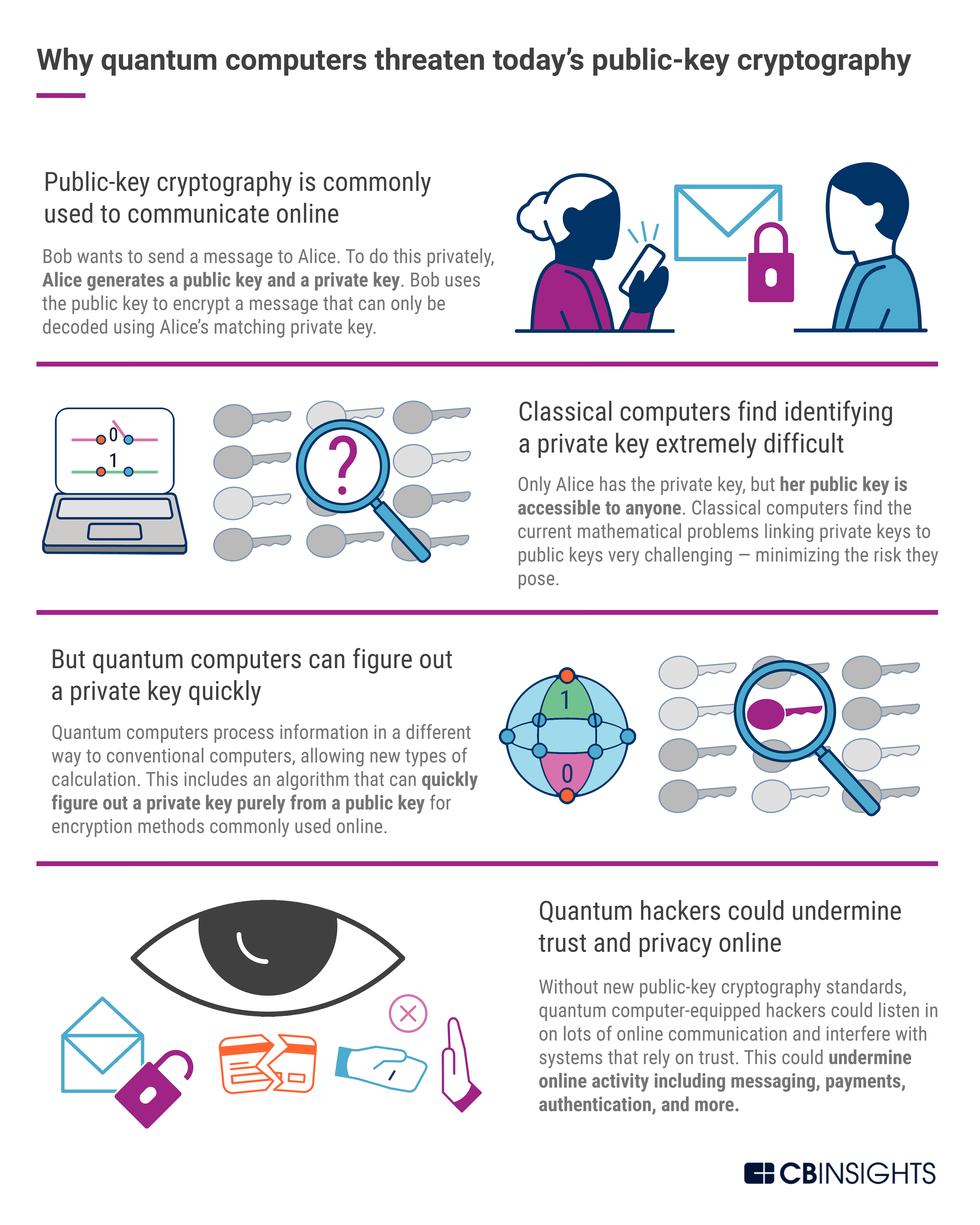
In conclusion, implementing quantum cryptography requires a deep understanding of the underlying quantum principles, as well as a thorough knowledge of the available cryptographic techniques. It is a complex and challenging process that requires a multidisciplinary approach, involving experts in quantum mechanics, cryptography, and computer science.
Despite the challenges, the potential benefits of quantum cryptography are enormous. It promises to revolutionize the way we transmit and store sensitive information, providing unprecedented levels of security and privacy. By harnessing the power of quantum mechanics, we can ensure that our most valuable information remains safe from prying eyes, enabling us to build a more secure and trustworthy digital world. So, let us work together towards a future where quantum cryptography is the norm, and where our information is protected by the strongest cryptographic methods available.