Quantum key cryptography is an advanced technology that has been gaining traction in recent years. It is a cryptographic technique that uses the principles of quantum mechanics to secure communication between two parties. With the increasing threats of cyber attacks and data breaches, quantum key cryptography provides a much-needed solution to protect sensitive information.
Implementing quantum key cryptography is not an easy task, and requires a deep understanding of quantum mechanics and cryptography. However, with the right knowledge and tools, it is possible to implement this technology effectively. In this article, we will explore the basics of quantum key cryptography and provide a step-by-step guide on how to implement it. Whether you are a cybersecurity professional or an enthusiast, this guide will equip you with the knowledge you need to secure your communication with quantum key cryptography.
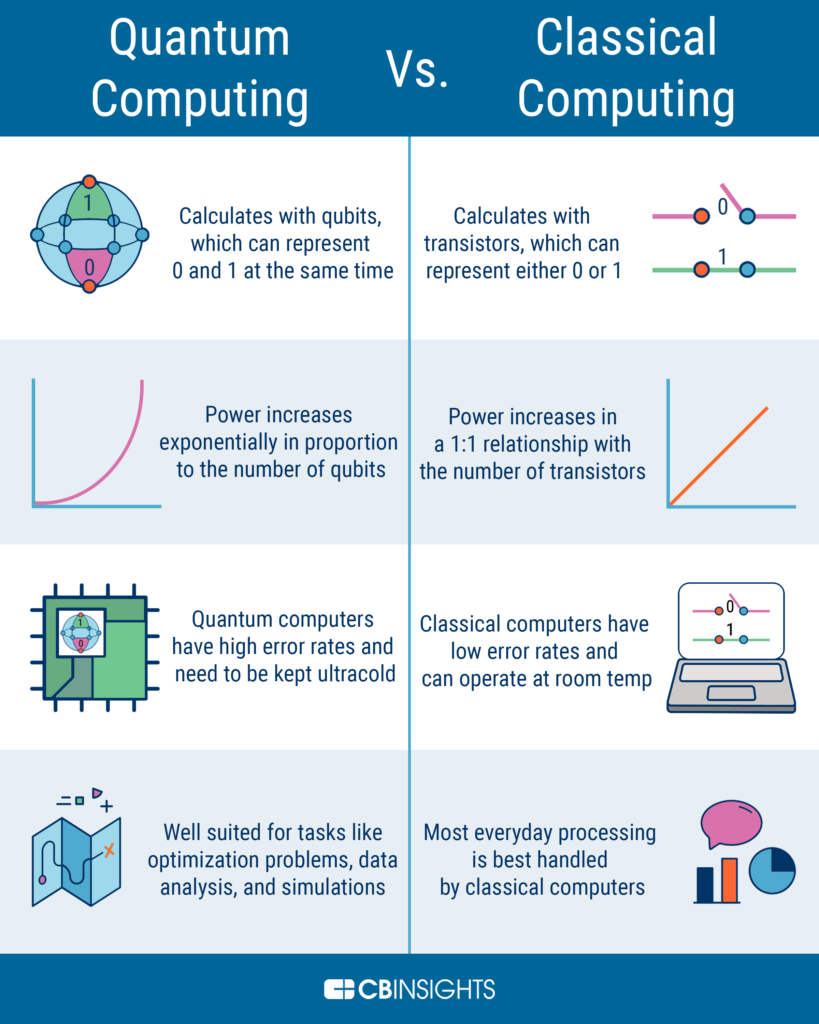
Quantum key cryptography (QKC) is a secure communication method that relies on the principles of quantum mechanics. It can be implemented in two ways: quantum key distribution (QKD) and quantum random number generation (QRNG). QKD uses quantum entanglement to generate a shared secret key between two parties, while QRNG relies on the quantum nature of particles to generate random numbers. Both methods are secure and reliable, and can be used for secure communication.
To implement QKC, first start by setting up a secure link between two parties. This can be done using a quantum-safe network such as the IBM Quantum Network. Next, the two parties must agree on a protocol, such as Diffie-Hellman key exchange, to generate a shared secret key. Once the key is generated, it must be securely transmitted to both parties. Finally, the key can be used to encrypt and decrypt messages.
- Set up a secure link between two parties
- Agree on a protocol to generate a shared secret key
- Securely transmit the key to both parties
- Use the key to encrypt and decrypt messages

What is Quantum Key Cryptography?
Quantum key cryptography is an emerging field of cryptography that uses quantum mechanical properties to secure data. It is based on the principles of quantum mechanics and provides a new level of security for information communication. Quantum key cryptography is different from traditional cryptography in that the security of the system is based on the physical properties of the quantum particles used for transmission, rather than on mathematical algorithms. As such, it provides a higher level of security than traditional cryptography.
How to Implement Quantum Key Cryptography?
Step 1: Generate Quantum Key
The first step in implementing quantum key cryptography is to generate a quantum key. This is done by using a quantum random number generator (QRNG) to generate a random string of numbers or letters. The QRNG is a device that produces random numbers which are unpredictable and cannot be predicted or guessed. The quantum key generated by the QRNG is then used to encrypt the data being sent.
Step 2: Transmit Quantum Key
Once a quantum key has been generated, it needs to be transmitted over a secure connection. This is done using quantum key distribution (QKD). QKD is a process where two parties exchange quantum keys over a secure channel. The keys are transmitted using quantum particles, such as photons, which are secure from interception or manipulation.
Step 3: Encrypt Data
Once the quantum key has been transmitted, it can then be used to encrypt the data being sent. The encryption process involves transforming the data into an unreadable format. This ensures that the data is secure from interception and manipulation. The quantum key is used to encrypt the data with an algorithm that is impossible to break.
Step 4: Decrypt Data
Once the data has been encrypted, it needs to be decrypted in order to be used. This is done using the same quantum key that was used to encrypt the data. The quantum key is used to decrypt the data using the same algorithm that was used to encrypt the data. Once the data is decrypted, it can then be used by the recipient.
Step 5: Secure Communication
Finally, the quantum key can be used to secure the communication between the two parties. This is done by using the quantum key to encrypt all data that is exchanged between the two parties. This ensures that the data is secure from interception or manipulation. This ensures that the communication is secure and private.
Frequently Asked Questions
Quantum key cryptography is a secure communication method that uses quantum mechanical properties to encode and decode messages. It is an effective way of protecting confidential data and preventing interference from outside sources. Read on to find out more about how to implement quantum key cryptography.
What is quantum key cryptography?
Quantum key cryptography (QKC) is a type of cryptography that uses quantum mechanical properties to securely encrypt and decrypt messages. It utilizes a key, which is a series of randomly generated numbers, and these numbers are used to encode and decode messages. The key is created by a quantum computer and is designed to be secure, as it is impossible to predict the values of the key or to reverse engineer them. QKC is considered to be the most secure form of cryptography due to its reliance on the laws of physics, which are immutable and therefore cannot be manipulated by outside forces.
What are the benefits of using quantum key cryptography?
The primary benefit of using quantum key cryptography is its unparalleled security. This security is achieved by using principles of quantum mechanics, which are impossible to predict or manipulate. As a result, messages that are encoded and decoded using quantum key cryptography are virtually impossible to crack. Additionally, QKC is relatively easy to implement, as it does not require special hardware or software. It is also a relatively inexpensive method of encrypting data, making it an attractive option for businesses that need to protect their data.
How do I implement quantum key cryptography?
To implement quantum key cryptography, you will need a quantum computer capable of generating a secure key. The key is then shared between two parties, and can be used to securely encrypt and decrypt messages. Once the key is established, the two parties can exchange messages using the key to ensure the security of the data. It is important to note that the key must be kept secure and should be changed periodically to prevent any potential breaches.
What are the drawbacks of quantum key cryptography?
The primary drawback of quantum key cryptography is that it requires a quantum computer to generate the key. This can be an expensive and time-consuming process, and may not be feasible for some applications. Additionally, quantum key cryptography is not compatible with all systems, which can limit its effectiveness in certain cases. Finally, quantum key cryptography is only as secure as the key that is generated, so it is important to ensure that the key is kept secure and is regularly changed to prevent any potential breaches.
Are there any alternatives to quantum key cryptography?
Yes, there are several alternatives to quantum key cryptography. These include traditional symmetric and asymmetric encryption algorithms, as well as hash functions. However, these methods are not as secure as quantum key cryptography and can be vulnerable to attacks. Additionally, some of these methods require specialized hardware or software, making them less practical for some applications.

In conclusion, quantum key cryptography is a highly promising field that can revolutionize the way we approach data security. By using the principles of quantum mechanics, we can create cryptographic keys that are virtually unbreakable, ensuring that our sensitive information remains safe and secure. However, implementing this technology requires a deep understanding of quantum mechanics, and a significant investment in research and development.
As more and more companies and organizations become aware of the growing threat of cyberattacks, the demand for quantum key cryptography is only going to increase. By staying up to date with the latest advancements in this field, we can ensure that we are well equipped to protect ourselves and our data from even the most sophisticated attacks. With the right tools and knowledge, we can make quantum key cryptography a reality, ushering in a new era of security and peace of mind.