In the world of cryptography, security is of utmost importance. With the increasing threat of hackers and cybercriminals, it has become essential to have unbreakable encryption methods. One of the most reliable methods of encryption is the use of asymmetric algorithms. These algorithms are based on complex mathematical problems that are practically impossible to solve with current computing technology. However, with the advent of quantum computing, there is a fear that the security of asymmetric algorithms may be compromised. But why are asymmetric algorithms safe from quantum?
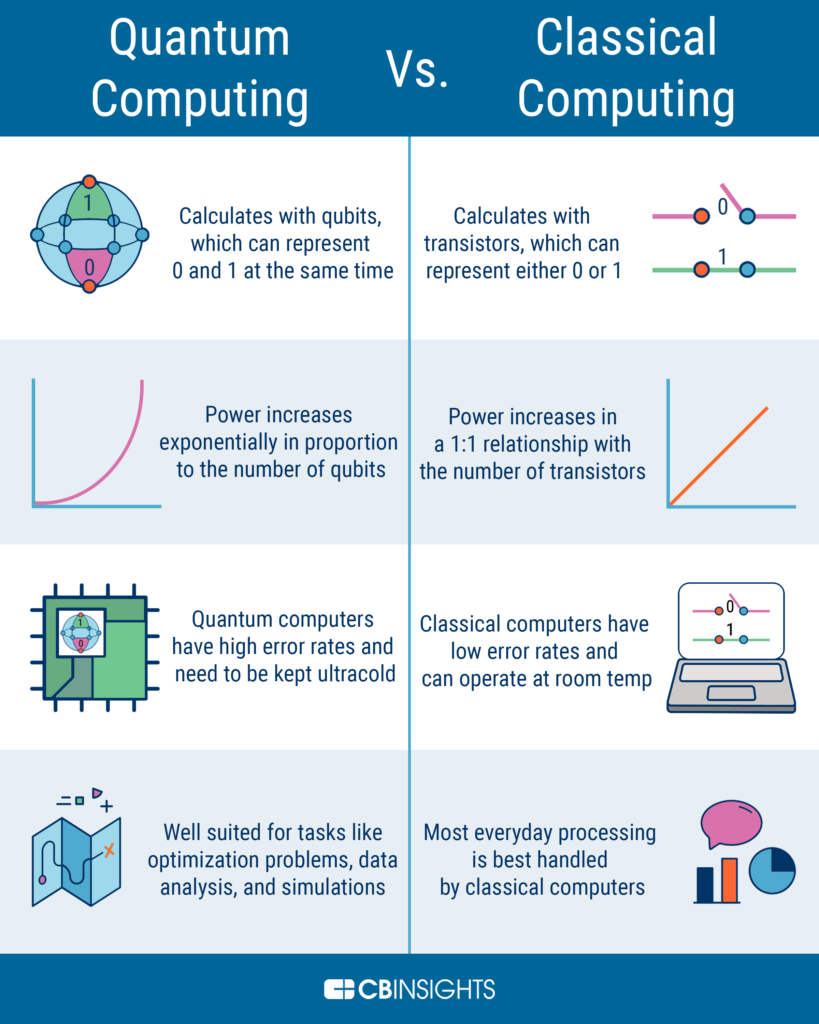
To understand why asymmetric algorithms are safe from quantum, we need to first understand the basic principles behind quantum computing. Quantum computers use quantum bits or qubits, which can exist in multiple states simultaneously, allowing for lightning-fast processing speeds. Asymmetric algorithms rely on the difficulty of factoring large prime numbers, a problem that is not easily solvable by classical computers. However, quantum computers have the ability to use Shor’s algorithm, which can factor large numbers in a fraction of the time that classical computers would take. Despite this, asymmetric algorithms are still safe from quantum computing because they rely on a different mathematical problem known as the discrete logarithm problem, which is not efficiently solvable by quantum computers using current technology.
Why are Asymmetric Algorithms Safe From Quantum?
Asymmetric encryption algorithms are widely used and are an integral part of secure communication. But with the emergence of quantum computing, the security of these algorithms is under threat. The question is, why are asymmetric algorithms safe from quantum?
What is Asymmetric Encryption?
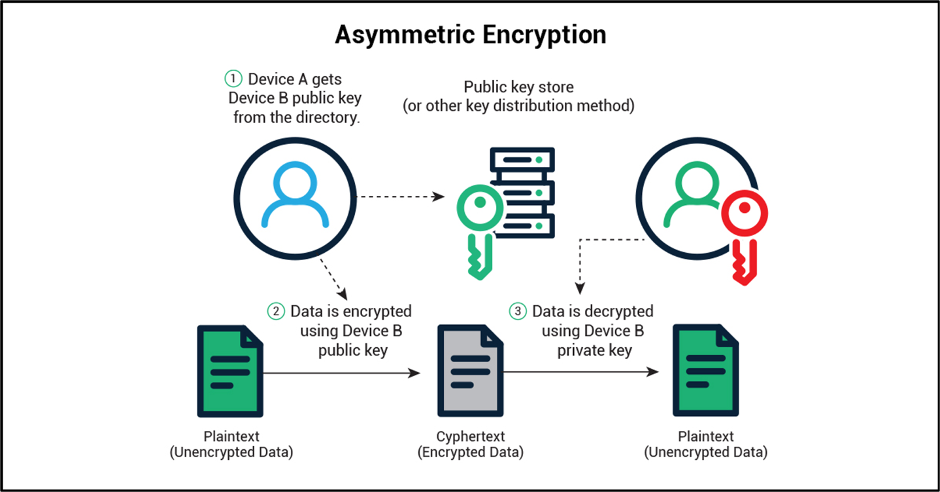
Asymmetric encryption, also known as public-key cryptography, is a type of encryption that uses two different keys– one for encryption and one for decryption. The sender of the data uses the public key to encrypt the data and the receiver uses the private key to decrypt the data. This type of encryption is used to secure communication between two parties, as it ensures that only the intended receiver can decrypt the data.
What is Quantum Computing?
Quantum computing is a form of computing that uses quantum mechanics to process information. It is based on the idea that certain particles can exist in multiple states at the same time, allowing them to process information much faster than traditional computers. This makes quantum computers extremely powerful, as they can solve complex problems in a fraction of the time.
Why are Asymmetric Algorithms Safe from Quantum?
Asymmetric algorithms are protected from quantum computing because of the way they work. Unlike symmetric encryption algorithms, which use the same key for encryption and decryption, asymmetric algorithms use two different keys. This means that a quantum computer would need to be able to break both of the keys in order to gain access to the data.
Furthermore, asymmetric algorithms are designed to be extremely secure and resistant to attack. They use complex mathematical functions and large key sizes to make it difficult for a quantum computer to decrypt the data. This makes it much more difficult for a quantum computer to gain access to the data, as it would have to break both of the keys to do so.
Overall, asymmetric algorithms are safe from quantum computing because of their complexity and the use of two different keys. This makes it very difficult for a quantum computer to gain access to the data, as it would need to break both of the keys to do so. As a result, asymmetric algorithms remain secure and resistant to attack.
Frequently Asked Questions – Why are Asymmetric Algorithms Safe from Quantum?
Asymmetric algorithms are a type of cryptography that provide a secure way of encrypting and decrypting data. They are resistant to attack from quantum computers, making them an ideal choice for secure communication.
What are Asymmetric Algorithms?
Asymmetric algorithms, also known as public-key cryptography, use a pair of mathematically related, but different, keys to encrypt and decrypt data. The public key is used to encrypt data, while the private key is used to decrypt it. This makes it more secure than symmetric algorithms, which use the same key for both encryption and decryption.
Why are Asymmetric Algorithms Safe from Quantum?
Asymmetric algorithms are believed to be safe from attack by quantum computers because the underlying mathematics that they rely on is not susceptible to attack by a quantum computer. This makes them much more secure than symmetric algorithms, which can be cracked relatively easily by a quantum computer.
What are the Advantages of Asymmetric Algorithms?
Asymmetric algorithms offer several advantages over symmetric algorithms. They are more secure, since the data is encrypted and decrypted using different keys. They also provide a way to authenticate data, since the public key can be used to verify that the data has not been tampered with. Finally, they are more efficient, since the same key is not used for encryption and decryption.
What are the Disadvantages of Asymmetric Algorithms?
The main disadvantage of asymmetric algorithms is that they are slower than symmetric algorithms. This can be an issue if the data needs to be encrypted and decrypted quickly. Additionally, asymmetric algorithms require more storage space than symmetric algorithms, since two keys are required for encryption and decryption.
Are Asymmetric Algorithms Secure?
Yes, asymmetric algorithms are considered to be secure. They are resistant to attack by quantum computers, and they provide a way to authenticate data. Additionally, they provide a secure way of encrypting and decrypting data without the need to share a secret key.

In conclusion, asymmetric algorithms, such as RSA and ECC, are considered safe from quantum attacks due to their reliance on mathematical problems that are difficult for quantum computers to solve. While quantum computers have the potential to break the security of symmetric algorithms, such as AES, through the use of Shor’s algorithm, asymmetric algorithms’ security is largely unaffected. This is because asymmetric algorithms rely on the difficulty of factoring large prime numbers or solving the elliptic curve discrete logarithm problem, which are currently believed to be intractable for quantum computers.
However, it is important to note that quantum computing is still a rapidly developing field, and researchers are continuously working towards developing new algorithms and techniques that may be capable of breaking current asymmetric algorithms. Therefore, it is essential for the security industry to stay up-to-date with the latest advancements in quantum computing and develop new cryptographic methods that are resistant to quantum attacks. By doing so, we can ensure that our data and communications remain secure in the face of this emerging technology.