As the world becomes increasingly dependent on digital technology, the security of our online communications and transactions has become a major concern. Cryptography is the practice of secure communication, and it has been used for centuries to encode messages and protect sensitive information. However, with the advent of new and powerful computing technologies, the methods used for cryptography are becoming increasingly vulnerable to attack. This is where quantum resistant cryptography comes in.
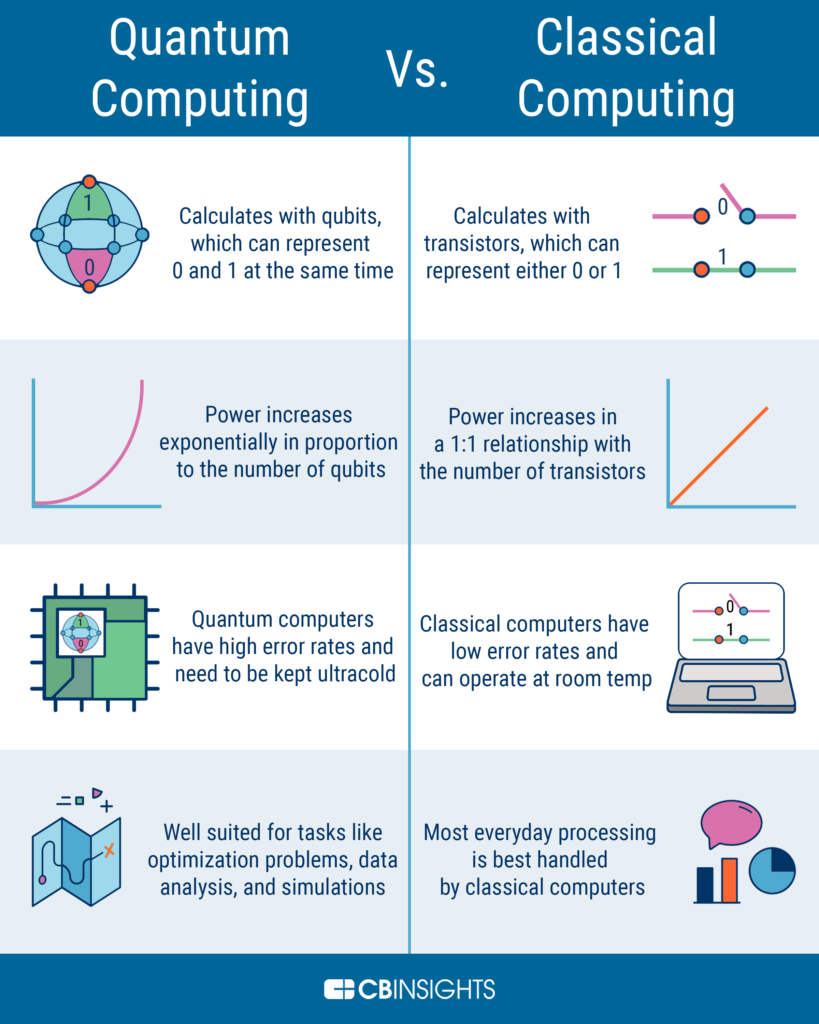
Quantum resistant cryptography is a type of encryption that is designed to be resistant to quantum computing attacks. Quantum computers use quantum bits, or qubits, which are able to process information in a fundamentally different way than traditional computers. This means that they are able to solve certain types of problems much faster than traditional computers, including problems related to cryptography. Quantum resistant cryptography is designed to be resistant to these attacks, and it is being developed as a potential solution to the growing threats to online security. In this article, we will explore what quantum resistant cryptography is, how it works, and why it is important for the future of online security.
Quantum resistant cryptography is a type of cryptography that is designed to withstand attacks from quantum computers. It is an emerging technology that is expected to become more important as quantum computing advances. Quantum resistant cryptography utilizes methods such as lattice-based cryptography, multivariate-quadratic equations, code-based cryptography and hash-based cryptography in order to protect data from quantum computer attacks.

What is Quantum Resistant Cryptography?
Quantum resistant cryptography is an emerging technology that is designed to protect data from being accessed or decoded by quantum computers. This technology is becoming increasingly important as quantum computers become more powerful and capable of cracking existing encryption methods. The goal of quantum resistant cryptography is to create an encryption system that is secure against quantum computers, allowing data to remain safe even if a quantum computer is used to try and access it.
How Does Quantum Resistant Cryptography Work?
Quantum resistant cryptography relies on mathematical algorithms and cryptographic techniques to create an encryption system that is resistant to attacks from quantum computers. These algorithms are designed to be resistant to quantum computers, meaning that they cannot be broken or decoded even if a quantum computer is used to try and access the data. These algorithms are also designed to be secure against other forms of attack, such as brute force attacks, making them more secure than traditional encryption methods.
Post-Quantum Cryptography
Post-quantum cryptography is a form of quantum resistant cryptography that is designed to be secure even against future advances in quantum computing. This type of cryptography is still in the early stages of development and is not yet widely used. However, it is expected to become more widely adopted in the future as quantum computers become more powerful and capable of breaking current encryption methods.
Quantum Key Distribution (QKD)
Quantum key distribution (QKD) is a form of quantum resistant cryptography that relies on quantum mechanics to securely distribute encryption keys. This method uses photons to send encryption keys from one user to another, making it almost impossible for a third-party to intercept the data. This type of cryptography is currently used by some government agencies and is expected to become more widely used in the future.
Quantum-Secure Authentication (QSA)
Quantum-secure authentication (QSA) is a form of quantum resistant cryptography that relies on quantum mechanics to securely authenticate users. This type of cryptography uses quantum random number generators to generate a random number that is used to authenticate users. This random number is then used to create a unique encryption key that can be used to securely authenticate a user. This type of cryptography is currently used by some government agencies and is expected to become more widely used in the future.
Quantum-Safe Cryptographic Algorithms
Quantum-safe cryptographic algorithms are algorithms that are designed to be resistant to attacks from quantum computers. These algorithms are designed to use mathematical principles that are resistant to quantum computing, allowing them to remain secure even if a quantum computer is used to try and access the data. These algorithms are currently being developed and tested, and are expected to become more widely used in the future.
Quantum-Resistant Cryptographic Protocols
Quantum-resistant cryptographic protocols are protocols that are designed to be secure against attacks from quantum computers. These protocols use cryptographic techniques to ensure that data can remain secure even if a quantum computer is used to try and access it. These protocols are currently being developed and tested, and are expected to become more widely used in the future.
Quantum-Proof Cryptographic Primitives
Quantum-proof cryptographic primitives are cryptographic primitives that are designed to be resistant to attacks from quantum computers. These primitives use mathematical principles that are resistant to quantum computing, allowing them to remain secure even if a quantum computer is used to try and access the data. These primitives are currently being developed and tested, and are expected to become more widely used in the future.
Conclusion
Quantum resistant cryptography is an emerging technology that is designed to protect data from being accessed or decoded by quantum computers. This technology is becoming increasingly important as quantum computers become more powerful and capable of cracking existing encryption methods. Quantum resistant cryptography relies on mathematical algorithms and cryptographic techniques to create an encryption system that is resistant to attacks from quantum computers. This technology is still in its early stages of development, but is expected to become more widely used in the future as quantum computers become even more powerful.
Frequently Asked Questions about Quantum Resistant Cryptography
Quantum resistant cryptography is a type of cryptography designed to protect data against potential attacks from quantum computing. Quantum computers are powerful enough to break traditional encryption methods, so quantum resistant cryptography is a way to safeguard data from these powerful computers.
What is Quantum Resistant Cryptography?
Quantum Resistant Cryptography is a type of cryptography that is designed to protect data from potential attacks by quantum computers. Traditional encryption methods, such as RSA and Elliptic Curve Cryptography, are vulnerable to attacks by quantum computers. As such, quantum resistant cryptography was developed to provide a way to protect data against these powerful computers.
Quantum resistant cryptography utilizes algorithms that are resistant to attacks by quantum computers. These algorithms are designed to be robust enough to withstand attacks from quantum computers, and they are also designed to be as secure as possible. One example of a quantum resistant algorithm is the McEliece algorithm. This algorithm is based on an error-correcting code, and it is believed to be one of the most secure algorithms available.
What are the Benefits of Quantum Resistant Cryptography?
Quantum resistant cryptography provides a way to protect data from potential attacks by quantum computers. By using quantum resistant algorithms, data can be protected from the most powerful computers. Additionally, these algorithms are designed to be as secure and robust as possible, which helps ensure that data is not vulnerable to attack.
Quantum resistant cryptography also helps to ensure that data is safe from potential threats in the future. As quantum computing technology advances, traditional encryption methods will become increasingly vulnerable to attack. By using quantum resistant cryptography, organizations can ensure that their data is protected even as quantum computing technology advances.
What are the Limitations of Quantum Resistant Cryptography?
One limitation of quantum resistant cryptography is that it is not currently as widely used as traditional encryption methods. As such, there are still some security risks associated with using quantum resistant algorithms. Additionally, quantum resistant algorithms are still being developed, which means that they may not be as secure as other traditional encryption methods.
Another limitation of quantum resistant cryptography is that it is not always the most practical solution. Quantum resistant algorithms are more complex than traditional encryption methods, which means that they require more computing power and resources to implement. Additionally, quantum resistant algorithms are not as widely supported as traditional encryption methods, which can make it more difficult to use them.
How Can I Use Quantum Resistant Cryptography?
If you are looking to use quantum resistant cryptography, you will need to find a provider that offers quantum resistant algorithms. These providers will generally provide software and services that can be used to implement quantum resistant algorithms. Additionally, some providers may also offer consulting services to help organizations implement quantum resistant cryptography.
Once you have chosen a provider, you will need to implement the quantum resistant algorithm into your system. This may involve making changes to your existing system, or it may involve creating a new system from scratch. Additionally, you may need to hire a consultant to help you implement the quantum resistant algorithm.
What is the Future of Quantum Resistant Cryptography?
The future of quantum resistant cryptography is promising. As quantum computing technology advances, quantum resistant algorithms will become increasingly important. Additionally, quantum resistant algorithms are being developed at an ever-increasing rate, which means that they will become more secure and robust over time.
In the future, quantum resistant cryptography may become the standard for data security. As quantum computing technology continues to advance, traditional encryption methods will become increasingly vulnerable to attack. As such, organizations may begin to rely on quantum resistant cryptography to keep their data secure. Additionally, quantum resistant cryptography may become more widely supported, which will make it easier to use.
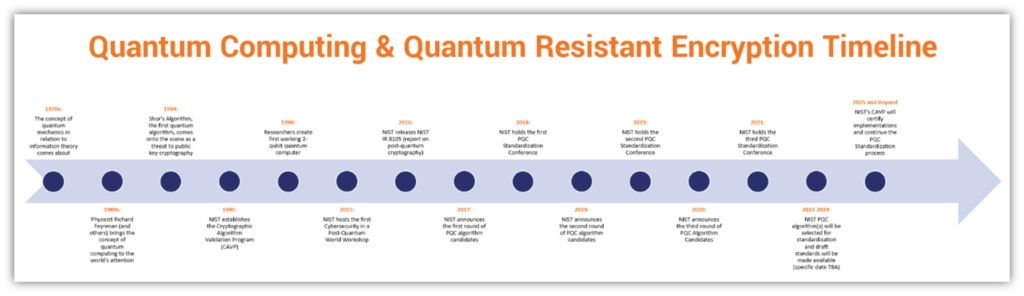
In conclusion, quantum resistant cryptography is a rapidly evolving field that promises to revolutionize the way we secure our data. With the advent of quantum computing, it has become increasingly clear that the traditional cryptographic algorithms we use today will not be sufficient to protect our sensitive information from the threats of tomorrow. As such, quantum resistant cryptography is emerging as a critical technology that will enable us to safeguard our data against the sophisticated attacks of quantum computers.
Moving forward, it is clear that quantum resistant cryptography will play a crucial role in shaping the future of cybersecurity. As quantum computing becomes more prevalent, it will be essential for businesses, governments, and individuals to adopt new cryptographic algorithms that can resist the power of quantum computers. By embracing quantum resistant cryptography, we can ensure that our data remains secure and protected from the threats of the future.