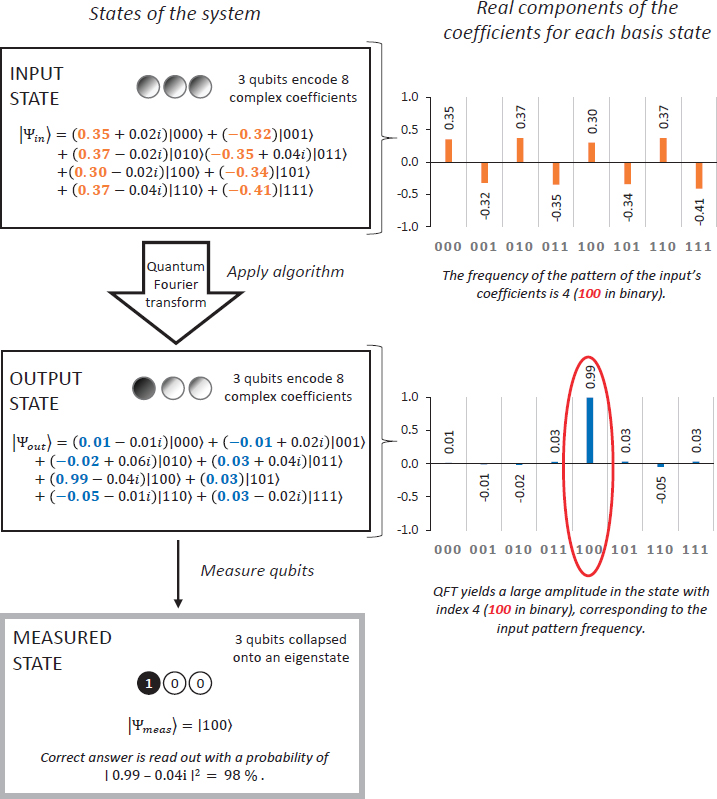
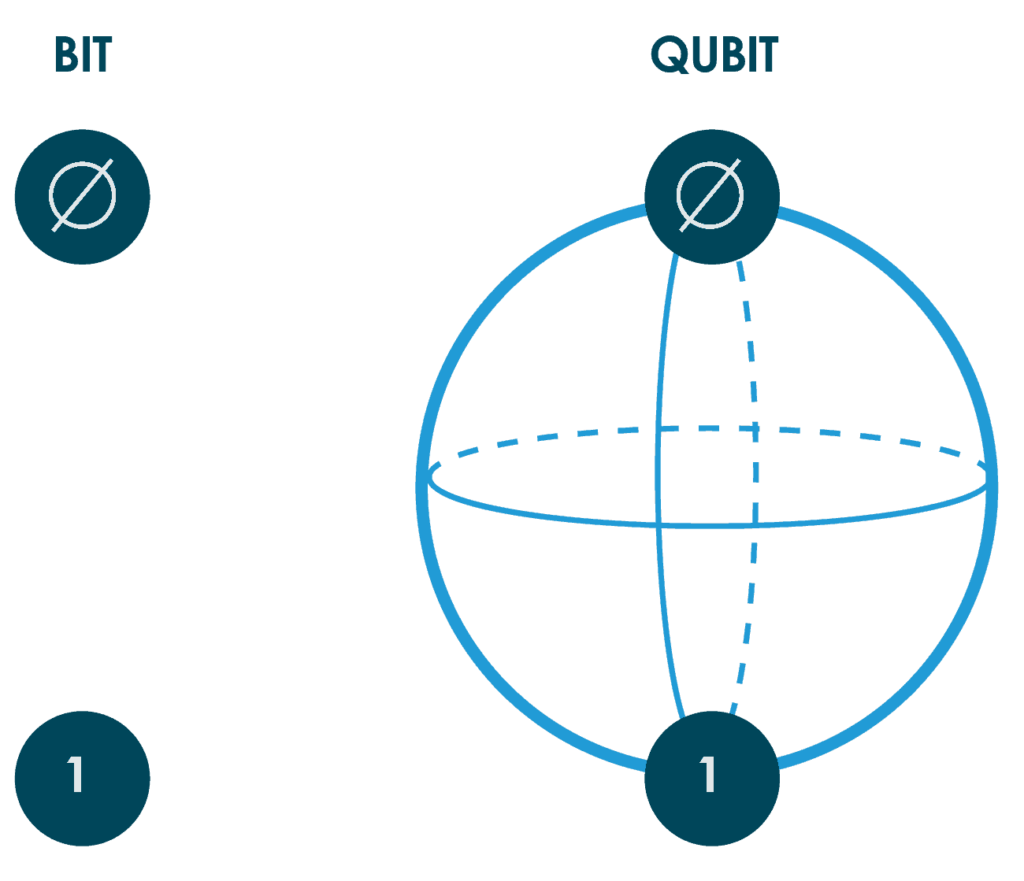
Quantum computing has emerged as a cutting-edge technology that is revolutionizing the way we process data. The technology has been touted as a game-changer in the field of data security, particularly with the development of quantum encryption algorithms. Encryption algorithms provide a way to protect data from unauthorized access and ensure its confidentiality. However, traditional encryption algorithms are becoming increasingly vulnerable to attacks, and quantum computing provides a means to develop more robust security measures.
If you’re looking to learn how to make encryption algorithms for quantum computing, you’ve come to the right place. In this article, we’ll explore the basics of quantum computing and encryption, as well as the key concepts and principles that underpin quantum encryption algorithms. We’ll also delve into some of the most widely used quantum encryption algorithms and provide a step-by-step guide on how to create your own quantum encryption algorithms. So, whether you’re a seasoned cryptographer or just starting out in the field, read on to discover how to make encryption algorithms for quantum computing.
Quantum computing encryption algorithms are based on the principles of quantum mechanics and can be used to securely encrypt data. To create quantum encryption algorithms, you need to understand the fundamentals of quantum computing, such as the principles of quantum entanglement and superposition, and the principles behind quantum key distribution. You also need to be familiar with the mathematical algorithms used to create and manage encryption keys. Once you understand the basics, you can begin to develop your own quantum encryption algorithms.
- Understand the fundamentals of quantum computing and quantum mechanics.
- Familiarize yourself with the mathematical algorithms used to create and manage encryption keys.
- Develop your own quantum encryption algorithm.
- Test the algorithm against existing encryption algorithms.
- Optimize the algorithm and make sure it is secure.

What is quantum computing?
Quantum computing is a form of computing that uses the quantum state of particles to process information. It is based on the principles of quantum mechanics and allows for the processing of large amounts of data in much shorter timeframes than traditional computing. Quantum computing has been proposed as a potential way to solve some of the most challenging problems in computing, such as cryptography.
How to make encryption algorithms of quantum computing?
Step 1: Understand the Basics of Cryptography
The first step to understanding how to make encryption algorithms of quantum computing is to understand the basics of cryptography. Cryptography is the art of writing and solving codes. It is used to protect data from being viewed or modified by unauthorized individuals. This can include both encryption and decryption of data.
Step 2: Learn About Quantum Computing
The next step to making encryption algorithms of quantum computing is to learn about quantum computing. Quantum computing is a form of computing that uses the quantum state of particles to process information. It is based on the principles of quantum mechanics and allows for the processing of large amounts of data in much shorter timeframes than traditional computing. To understand quantum computing, it is important to understand quantum mechanics and how it applies to computing.
Step 3: Design an Algorithm
The third step to making encryption algorithms of quantum computing is to design an algorithm. An algorithm is a set of instructions that tells a computer how to do something. When designing an algorithm for quantum computing, the steps taken will depend on the specific problem the algorithm is trying to solve. It is important to understand the problem and to create an algorithm that is efficient and secure.
Step 4: Test and Debug the Algorithm
The fourth step to making encryption algorithms of quantum computing is to test and debug the algorithm. This is done by running the algorithm through a series of tests to ensure it is functioning properly and is secure. This is an important step in the process and should not be overlooked.
Step 5: Implement the Algorithm
The fifth step to making encryption algorithms of quantum computing is to implement the algorithm. This involves taking the algorithm and putting it into practice. This can include incorporating the algorithm into a system or network, as well as ensuring that the algorithm is secure and functioning properly.
Step 6: Monitor and Maintain the Algorithm
The sixth and final step to making encryption algorithms of quantum computing is to monitor and maintain the algorithm. This involves regularly checking the algorithm for any potential security vulnerabilities or weaknesses, as well as making sure the algorithm is running efficiently. This is an ongoing process and should be done on a regular basis.
Frequently Asked Questions
Here is a list of commonly asked questions and answers about how to make encryption algorithms of quantum computing.
What is quantum computing?
Quantum computing is a technique in which data is stored and processed using the principles of quantum mechanics. By exploiting the principles of quantum mechanics, such as superposition and entanglement, quantum computers can perform calculations much faster than conventional computers. Quantum computing is a rapidly developing field of computer science, with potential applications in fields such as cryptography, finance, and medicine.
What are encryption algorithms?
Encryption algorithms are mathematical functions used to secure data by scrambling it into an unreadable form. It is commonly used to protect data from unauthorized access and to ensure that it is kept confidential. Encryption algorithms are used to protect data in transit and when stored on a computer or other device. The most commonly used encryption algorithms are symmetric key algorithms and public-key algorithms.
What are quantum encryption algorithms?
Quantum encryption algorithms are encryption algorithms that are based on the principles of quantum mechanics. These algorithms use the properties of quantum physics to create secure keys that are impossible to duplicate or intercept. Quantum encryption algorithms are used to protect data in transit, as well as data that is stored on a computer or other device.
How can I make encryption algorithms of quantum computing?
Making encryption algorithms of quantum computing involves understanding the principles of quantum mechanics and designing an algorithm that utilizes those principles. The algorithm must be able to generate a secure key that cannot be duplicated or intercepted. It should also be able to encrypt and decrypt data securely. Additionally, the algorithm should be able to securely store data on a computer or other device.
What are the benefits of using quantum encryption algorithms?
The benefits of using quantum encryption algorithms are numerous. These algorithms are much more secure than traditional encryption algorithms, as they are based on the principles of quantum mechanics. Additionally, quantum encryption algorithms are much faster than traditional algorithms, allowing for faster data transfer. Finally, quantum encryption algorithms are more resistant to attack and are much more difficult to crack than traditional algorithms.

In conclusion, developing encryption algorithms for quantum computing is a complex and challenging task. However, it is essential to ensure the security of sensitive data and communication in the era of increasingly powerful computing technologies. By leveraging the principles of quantum mechanics and exploring new approaches, researchers and developers can create encryption algorithms that are resistant to attacks from quantum computers. This will require collaboration and innovation from experts in various fields, including cryptography, mathematics, and physics.
As quantum computing continues to advance, the need for secure encryption will only grow. Therefore, it is crucial to invest in research and development efforts to create robust and scalable encryption algorithms. With cutting-edge technologies and the right expertise, we can ensure that sensitive information remains confidential and secure, even as computing power evolves. By working together and staying ahead of the curve, we can protect our data and maintain privacy in a rapidly changing digital landscape.