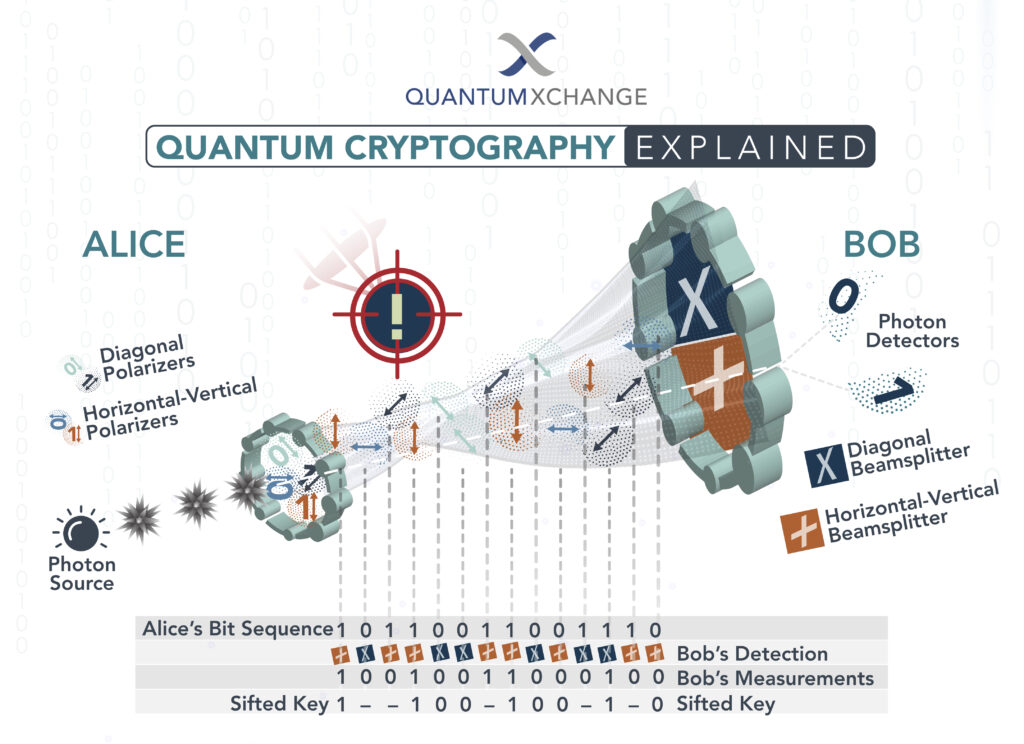
In today’s digital age, security has become a top priority for individuals and organizations alike. With the rise of quantum computing, the security of traditional cryptographic methods is becoming increasingly vulnerable. This is where post-quantum cryptography comes in. But what exactly is post-quantum cryptography?
Post-quantum cryptography refers to a class of cryptographic algorithms that are designed to withstand attacks by quantum computers. Unlike traditional cryptographic methods, which rely on the difficulty of solving certain mathematical problems, post-quantum cryptography utilizes mathematical problems that are believed to be resistant to quantum computing. As the world moves closer to the age of quantum computing, post-quantum cryptography will play a vital role in ensuring the security of our digital communication and data.
Post-quantum cryptography (also known as quantum-resistant cryptography) is a type of cryptography that relies on mathematical problems that are not solvable by current quantum computer technology. It is designed to protect data in the event that quantum computers become available, and is considered a more secure alternative to traditional cryptographic algorithms.
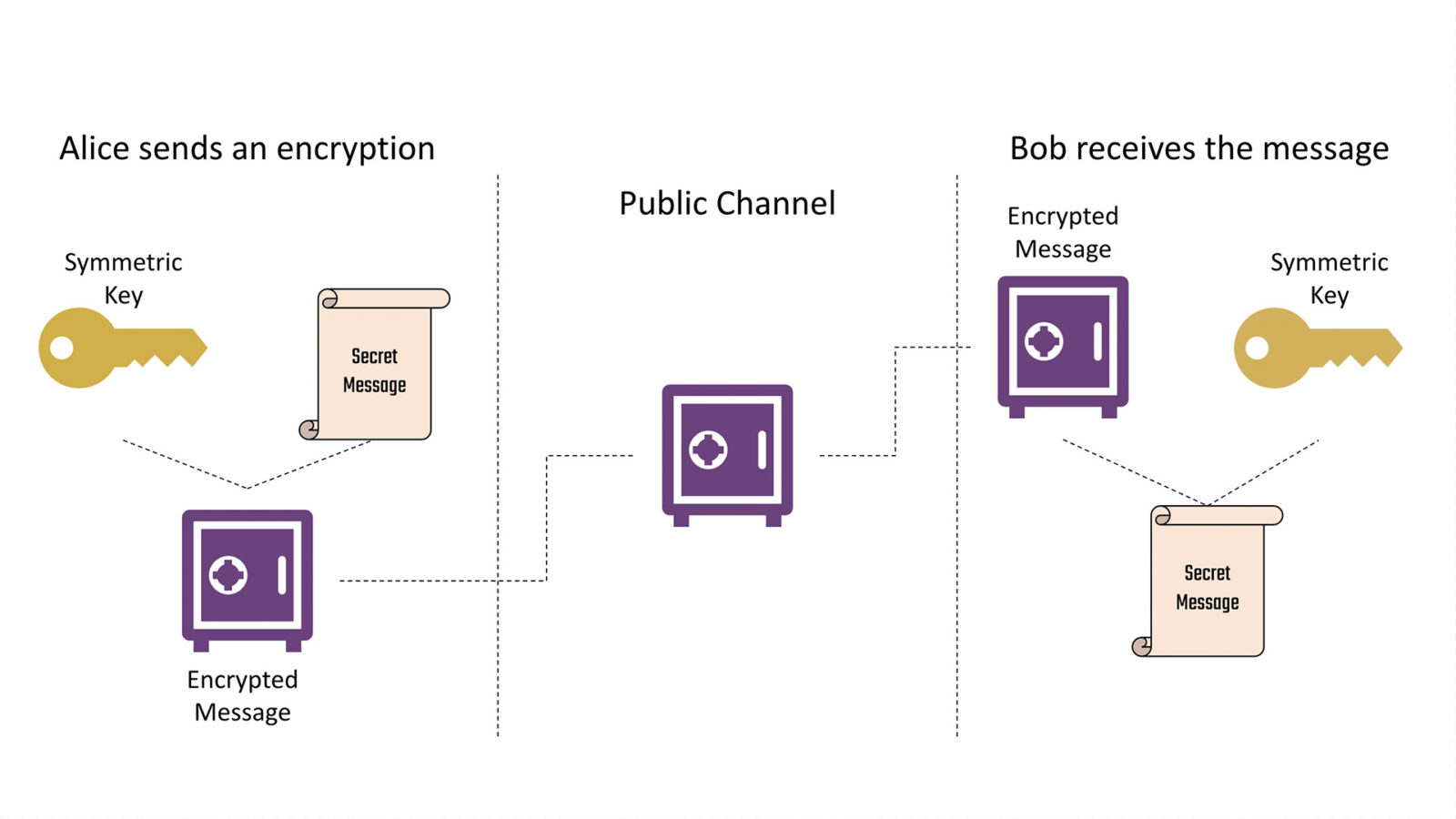
What is post-quantum cryptography?
Post-quantum cryptography is an advanced form of cryptography designed to protect data against attacks from quantum computers. It is an emerging field that is still in its early stages, but is rapidly gaining popularity due to the increasing threat of quantum computers. Post-quantum cryptography relies on mathematical algorithms that are much more complex than traditional encryption methods, making them resistant to attacks from quantum computers.
History of Post-Quantum Cryptography
Post-quantum cryptography has its roots in the 1970s, when the first quantum computers were proposed. At the time, cryptographers began to explore the possibility of using mathematical algorithms that could resist attacks from quantum computers. In the 1980s and 1990s, researchers developed various post-quantum algorithms, and in the 2000s, post-quantum cryptography began to gain traction as a viable security solution.
Today, post-quantum cryptography is an important part of the security landscape, and it is becoming increasingly important as quantum computers become more powerful. Post-quantum cryptography is used to protect data in a variety of industries, including finance, healthcare, and government.
How Post-Quantum Cryptography Works
Post-quantum cryptography relies on mathematical algorithms that are much more complex than traditional encryption methods. These algorithms are designed to resist attacks from quantum computers, which can break traditional encryption methods. Post-quantum algorithms are also designed to be computationally secure, meaning that they are resistant to brute force attacks.
Post-quantum cryptography is used in a variety of ways. It can be used to encrypt data, protect digital signatures, and authenticate communications. Post-quantum algorithms can also be used to protect data stored in a cloud or other remote locations.
Advantages of Post-Quantum Cryptography
Post-quantum cryptography provides a number of advantages over traditional encryption methods. It is resistant to attacks from quantum computers, making it more secure than traditional encryption methods. Post-quantum algorithms are also computationally secure, meaning that they are resistant to brute force attacks. Additionally, post-quantum cryptography is more efficient than traditional methods, allowing for faster encryption and authentication processes.
Disadvantages of Post-Quantum Cryptography
Post-quantum cryptography is still a relatively new field, and there are a few drawbacks to using it. First, post-quantum algorithms require more computing power than traditional encryption methods, making them more expensive. Additionally, post-quantum algorithms can be difficult to implement, and they require a deep understanding of cryptography. Finally, post-quantum algorithms are not yet widely available, and they are not supported by all software and hardware vendors.
Conclusion
Post-quantum cryptography is an advanced form of cryptography designed to protect data against attacks from quantum computers. It relies on complex mathematical algorithms that are resistant to attacks from quantum computers, and it is becoming increasingly important as quantum computers become more powerful. Post-quantum algorithms provide a number of advantages over traditional encryption methods, but they can also be difficult to implement and are not yet widely available.
Frequently Asked Questions about Post-Quantum Cryptography
Post-quantum cryptography is a type of cryptography that is secure against an attack by a quantum computer. It is used to protect data from eavesdropping and tampering.
What is Post-Quantum Cryptography?
Post-quantum cryptography is a type of cryptography that is designed to be secure against an attack by a quantum computer. It is used to protect data from eavesdropping and tampering. Post-quantum cryptography relies on mathematical problems that are believed to be hard to solve even with a quantum computer. Examples of these problems include the discrete logarithm problem and the integer factorization problem.
Post-quantum cryptography is still in its early stages of development. Most existing cryptography is vulnerable to attack by a quantum computer, so the need for post-quantum cryptography is becoming increasingly evident.
How Does Post-Quantum Cryptography Work?
Post-quantum cryptography relies on mathematical problems that are believed to be hard to solve even with a quantum computer. These problems can include the discrete logarithm problem and the integer factorization problem. By using these mathematical problems as the basis for encryption, it makes it much harder for a quantum computer to break the encryption.
Post-quantum cryptography is also designed to be secure against classical attacks. This means that even if an attacker does not have access to a quantum computer, they will still be unable to break the encryption. This makes post-quantum cryptography much more secure than traditional cryptography.
Why is Post-Quantum Cryptography Necessary?
Post-quantum cryptography is necessary because traditional cryptography is vulnerable to attack by a quantum computer. A quantum computer is able to solve certain mathematical problems much faster than a traditional computer, which means that it can break traditional cryptography much faster. Post-quantum cryptography is designed to be secure even against a quantum computer, which makes it much more secure than traditional cryptography.
Additionally, post-quantum cryptography is also designed to be secure against classical attacks. This means that even if an attacker does not have access to a quantum computer, they will still be unable to break the encryption.
What are the Benefits of Post-Quantum Cryptography?
The main benefit of post-quantum cryptography is that it is much more secure than traditional cryptography. Post-quantum cryptography is designed to be secure even against a quantum computer, which means that it is much more secure than traditional cryptography. Additionally, post-quantum cryptography is also designed to be secure against classical attacks. This means that even if an attacker does not have access to a quantum computer, they will still be unable to break the encryption.
The other benefit of post-quantum cryptography is that it is more efficient than traditional cryptography. Post-quantum cryptography is designed to be much faster and more efficient than traditional cryptography, which makes it more suitable for use in applications that require high levels of security.
Is Post-Quantum Cryptography Widely Used?
Post-quantum cryptography is still in its early stages of development, so it is not widely used yet. However, there are a number of organizations and companies that are beginning to use post-quantum cryptography. Additionally, there are a number of initiatives that are attempting to promote the adoption of post-quantum cryptography, such as the National Institute of Standards and Technology’s Post-Quantum Cryptography Standardization Project.
It is likely that post-quantum cryptography will become more widely used in the future as quantum computers become more powerful.

In conclusion, post-quantum cryptography is a new and evolving field that aims to address the security concerns that arise with the advent of quantum computers. With its focus on developing new cryptographic algorithms that can withstand attacks from quantum computers, post-quantum cryptography is set to revolutionize the world of cybersecurity. While there is still much research and development needed, post-quantum cryptography holds great promise in securing our digital lives in the face of emerging technologies.
As technology continues to advance, the need for secure communication and data storage becomes increasingly important. Post-quantum cryptography offers a solution to this challenge by providing a new generation of cryptographic algorithms that can resist attacks from quantum computers. As we move further into the digital age, it is essential to invest in the development of post-quantum cryptography to ensure the security of our information and protect against cyber threats.